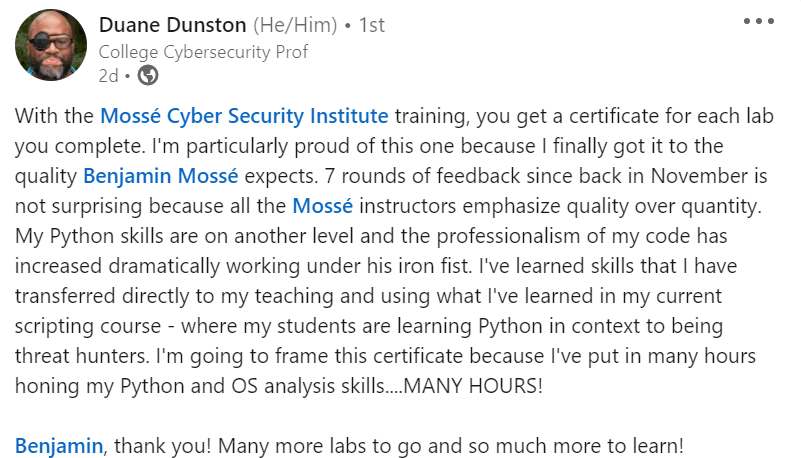
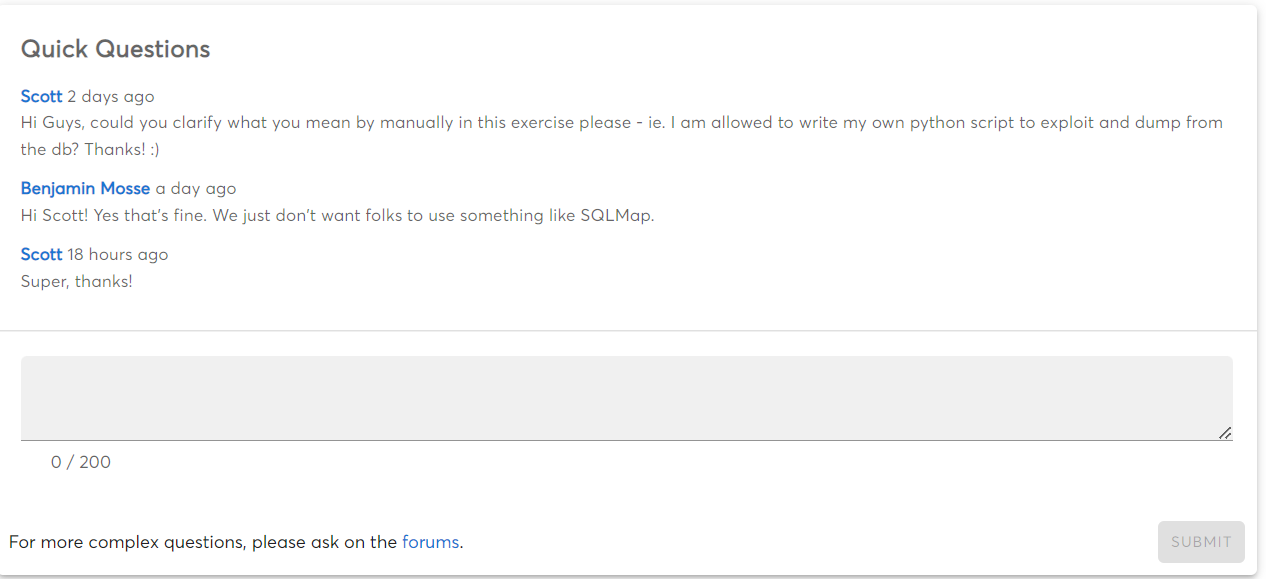
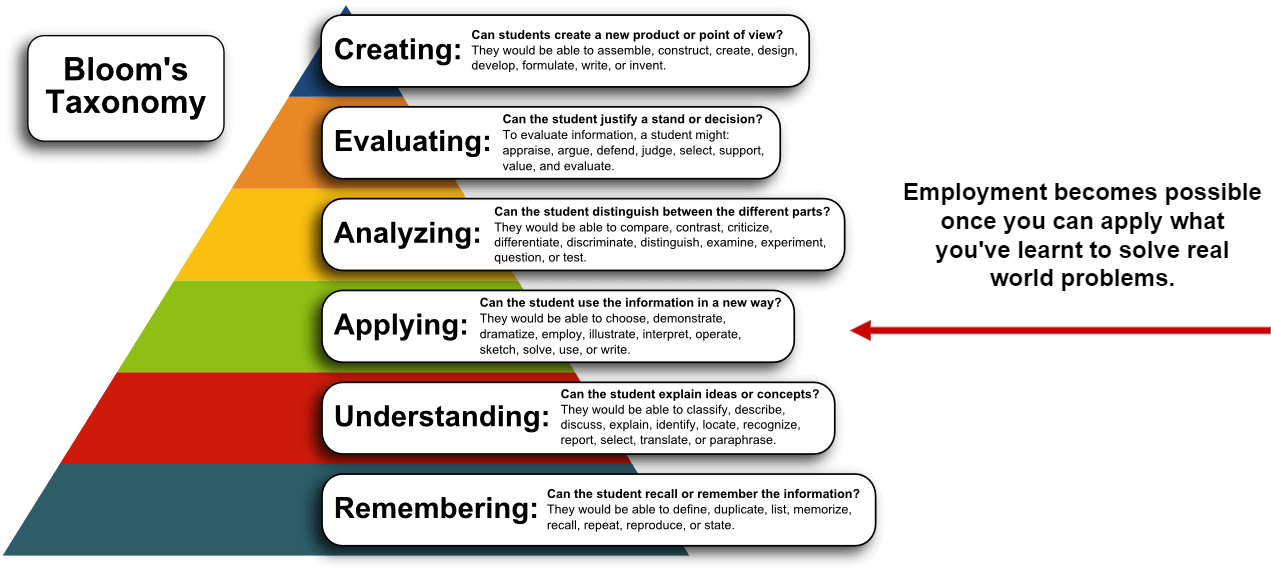
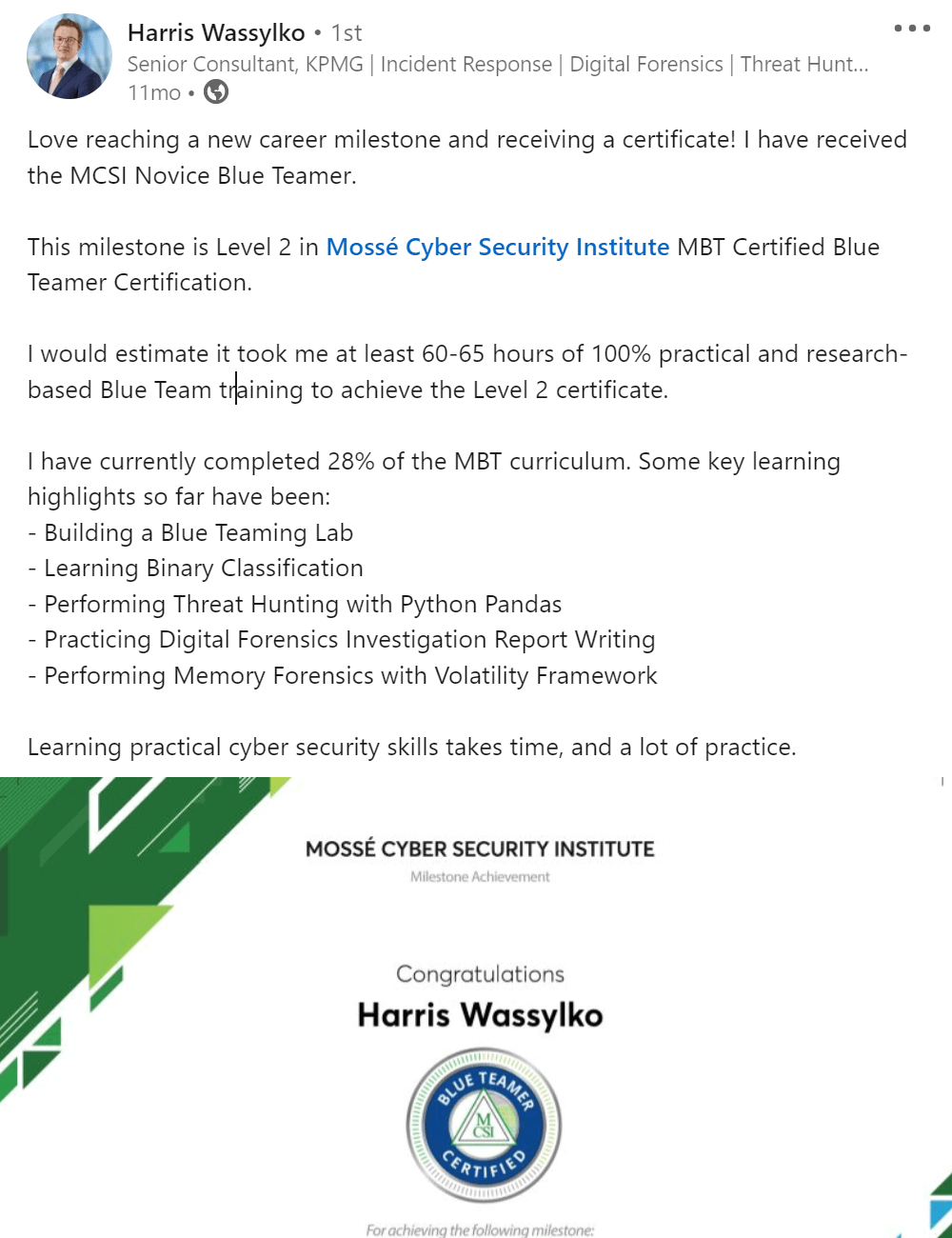
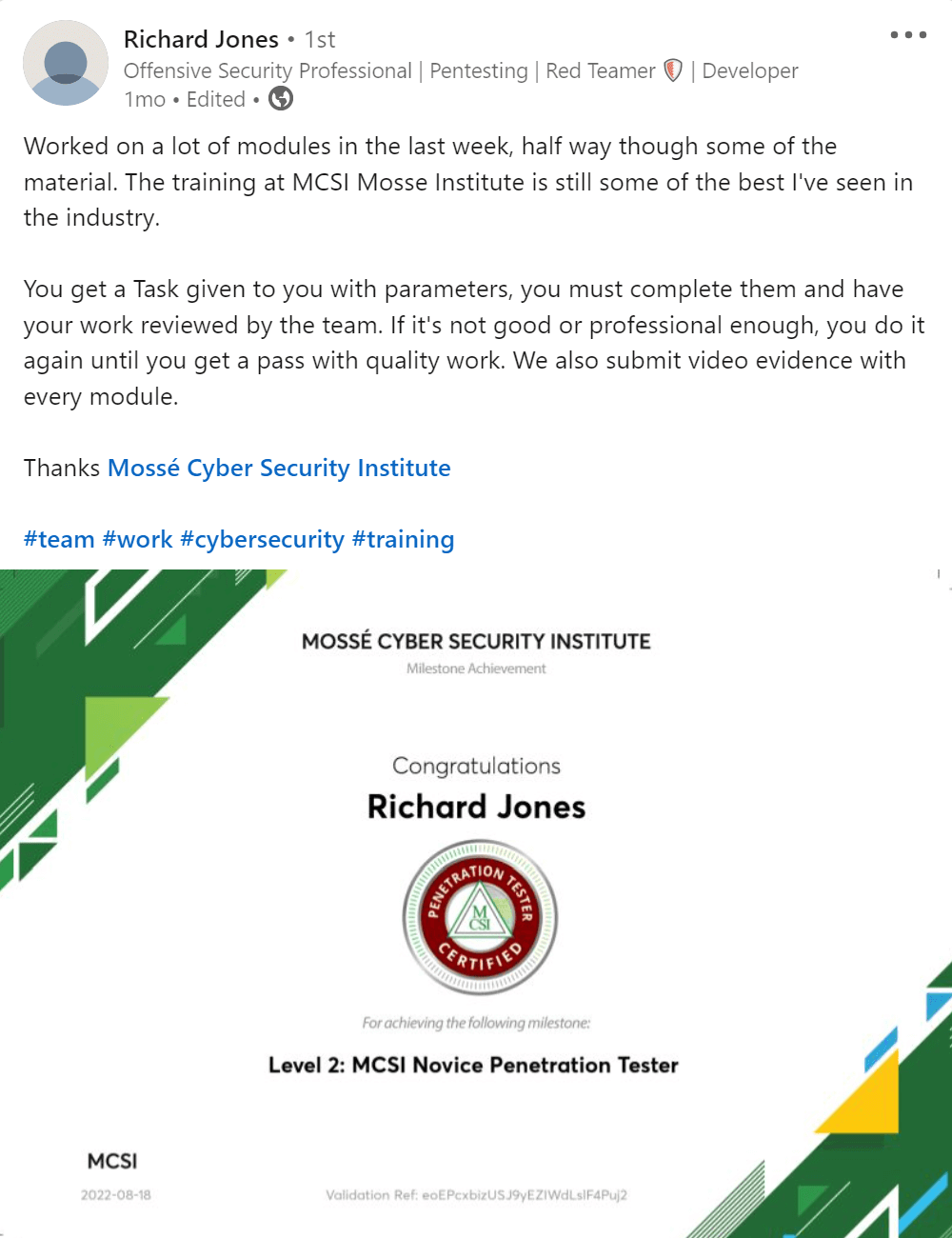
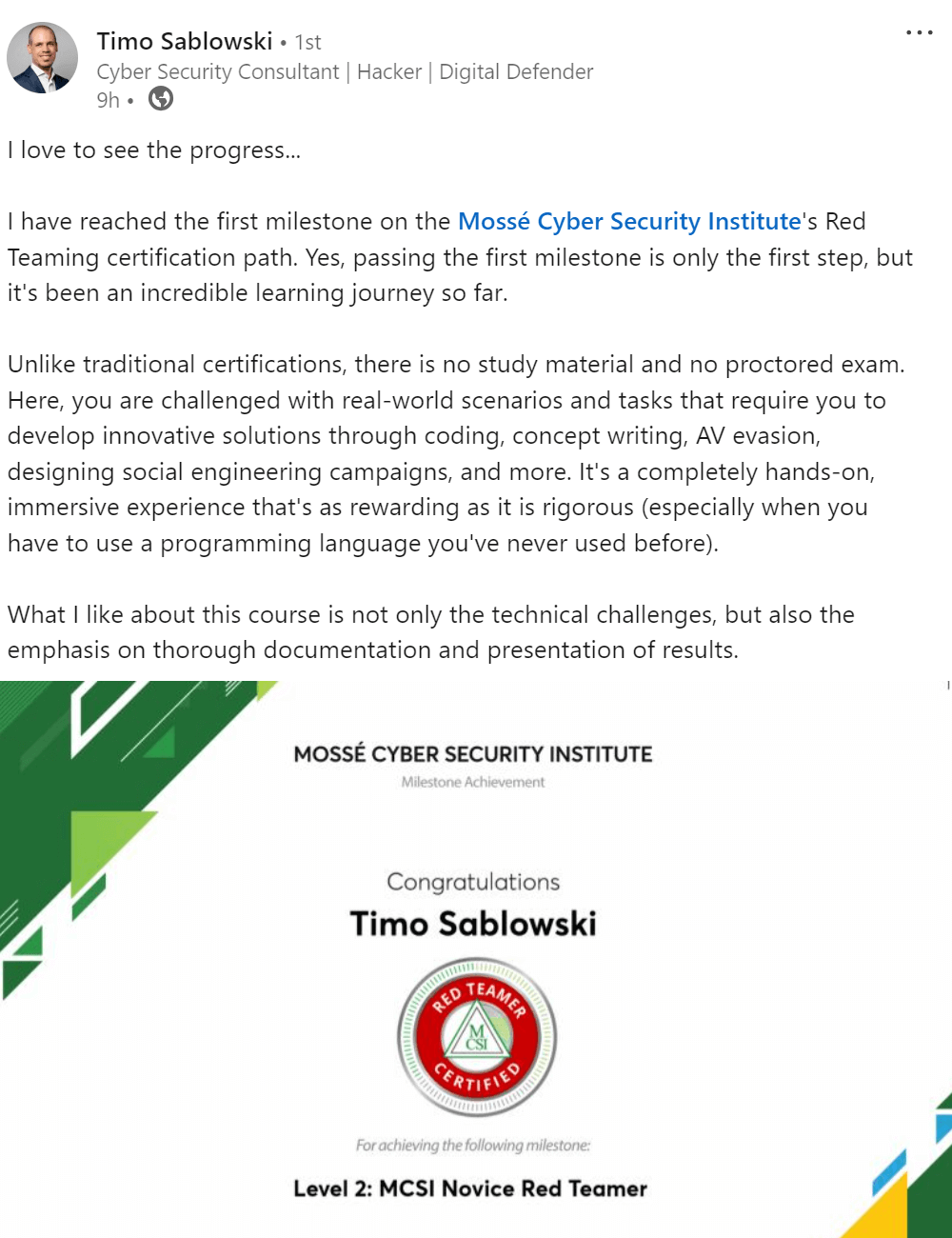
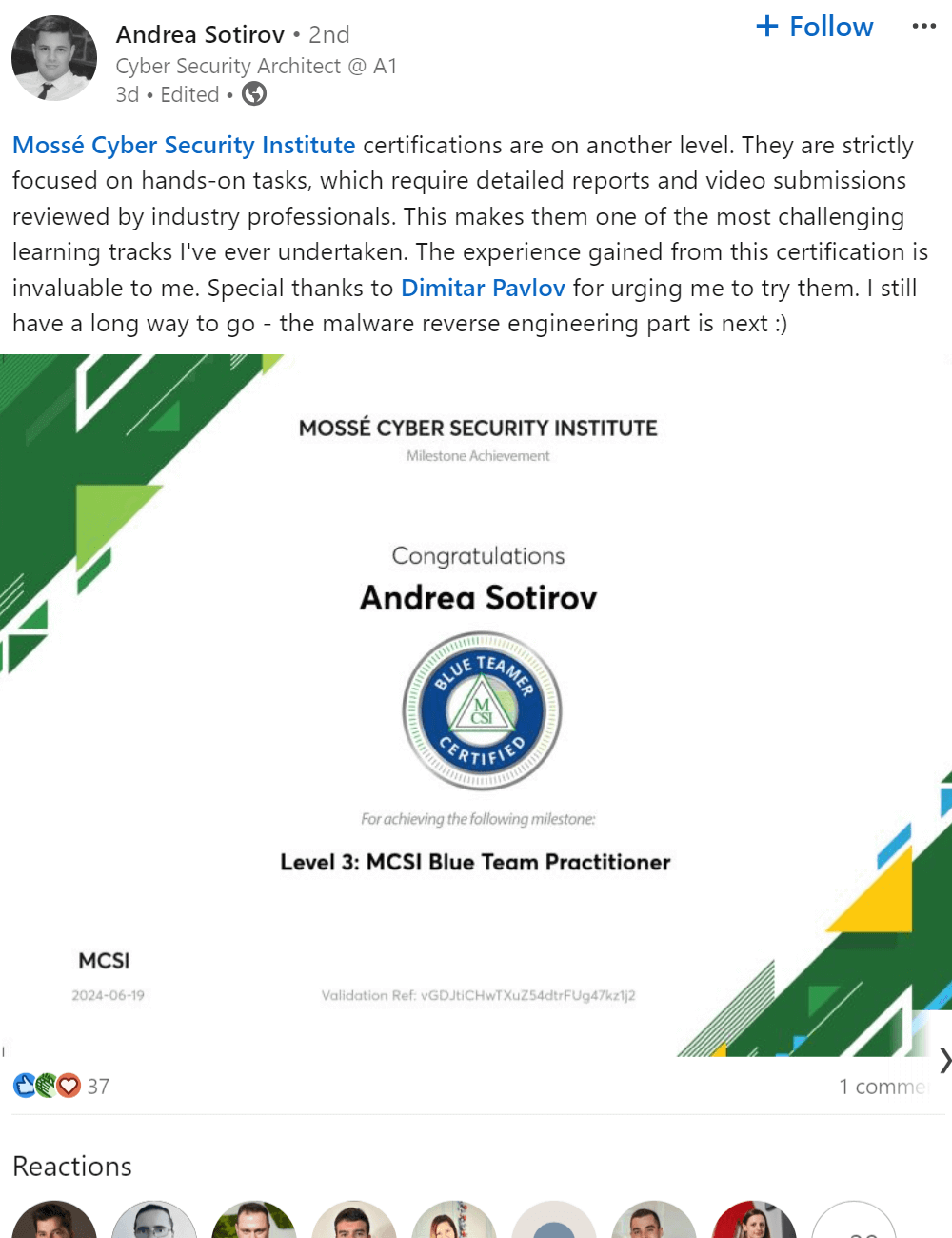
Deploying and managing incident mitigation strategies and tools can help organizations protect their systems, data, and customers. While there is no one-size-fits-all solution, organizations should consider a variety of options when defending their networks.
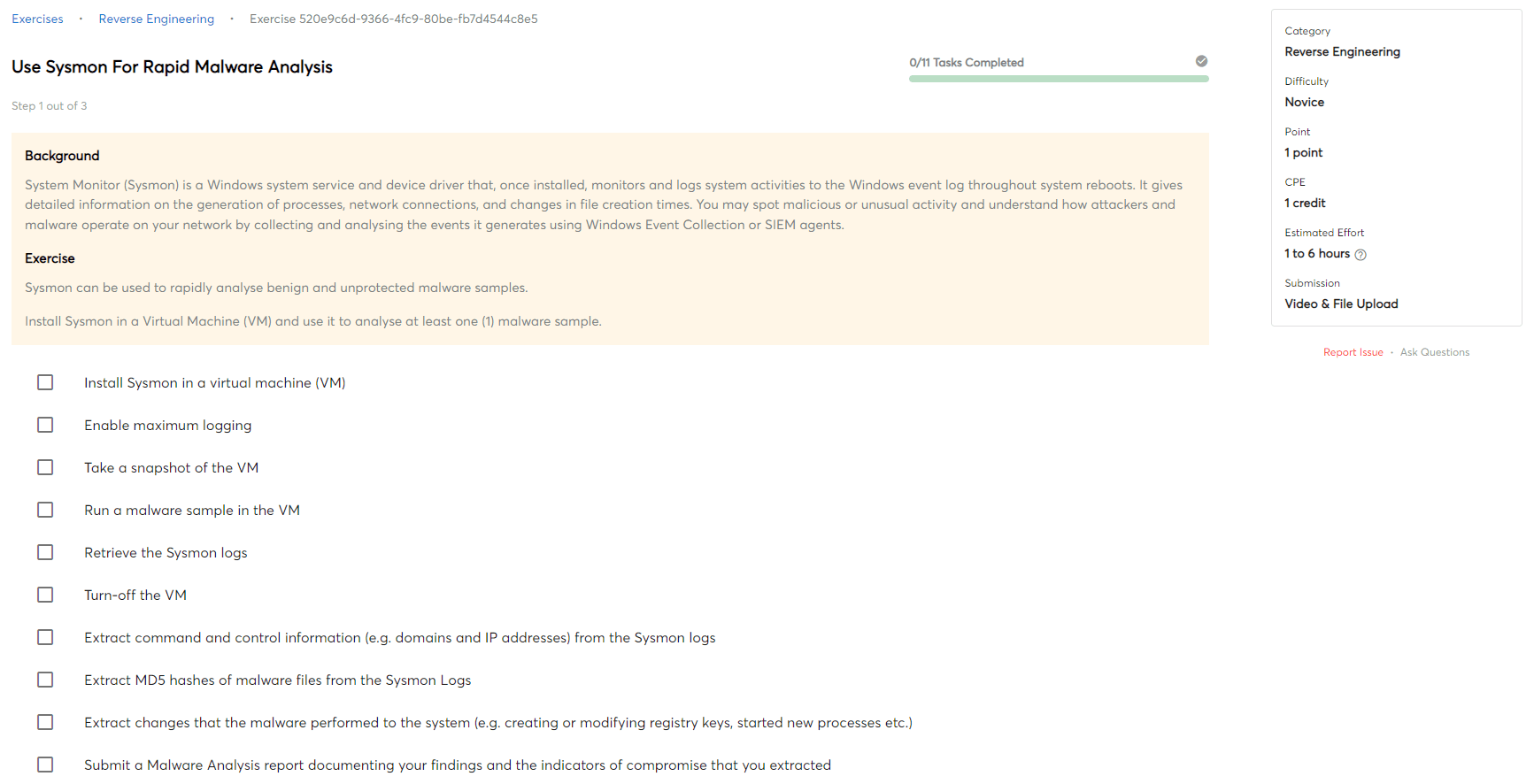
Application whitelisting
Application whitelisting is a security feature that allows approved applications to run while blocking all other applications. This security feature is used to prevent unauthorized code from running on a computer, which could result in the computer being compromised.
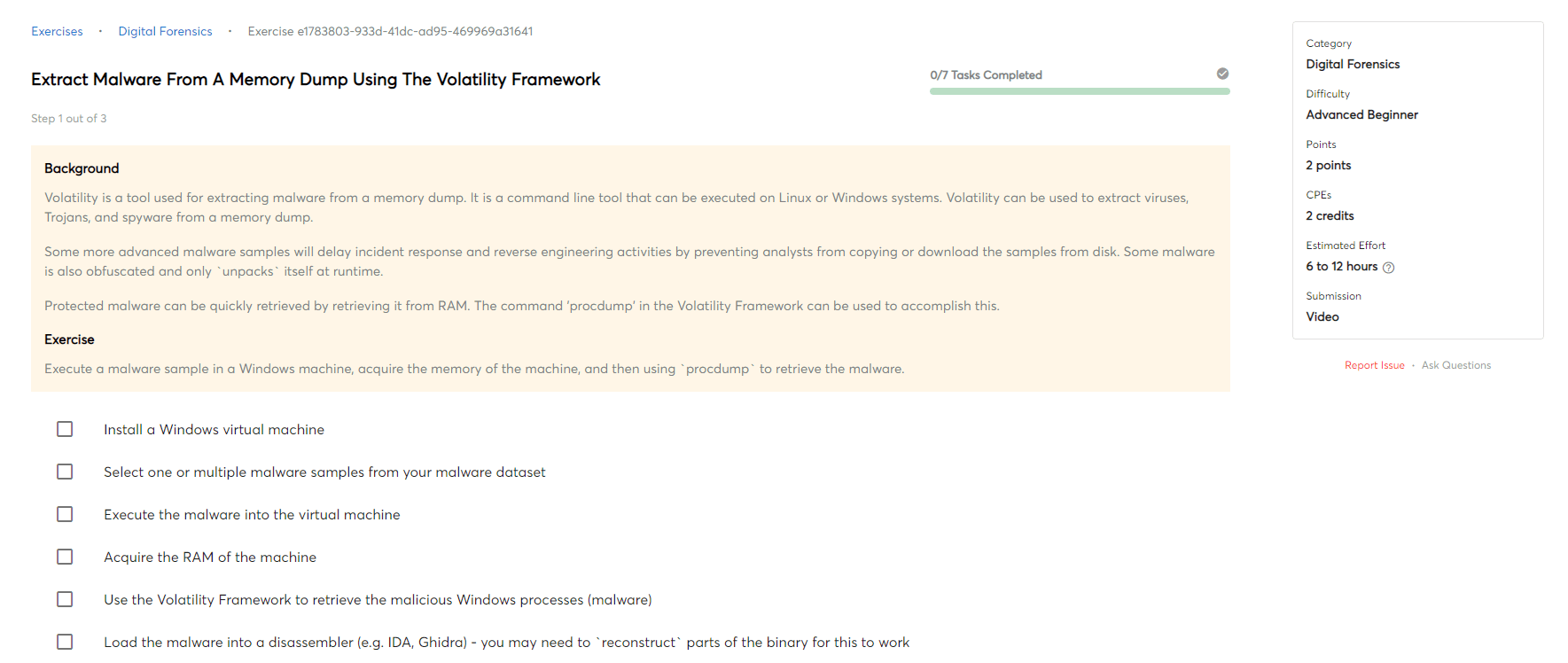
Patching applications and operating system
Patching an application or an operating system is the process of applying a software update, also known as a patch. This update fixes a problem or security vulnerability to the software. The patch may be released by the software's developer, or it may be released by the company that created the software's operating system.
Hardening user applications and operating system
One method of securing a computer system is to harden the user applications and the operating system. Hardening means making the applications and the operating system more resistant to attack by creating a more secure environment. Hardening can involve reducing the number of vulnerabilities that are present and by increasing the security of the environment.
Automated analysis and content filtering
Automated analysis and content filtering for security is the process of using software to automatically scan and analyze network traffic and content for malicious or unauthorized activity. This can help to identify threats and vulnerabilities early, and can help to protect against data breaches, malware infections, and other security threats.
Restrict administrative privileges
Limiting administrative privileges makes it more difficult for unauthorized users to gain access to the system, and also makes it more difficult for them to damage or exploit the system.
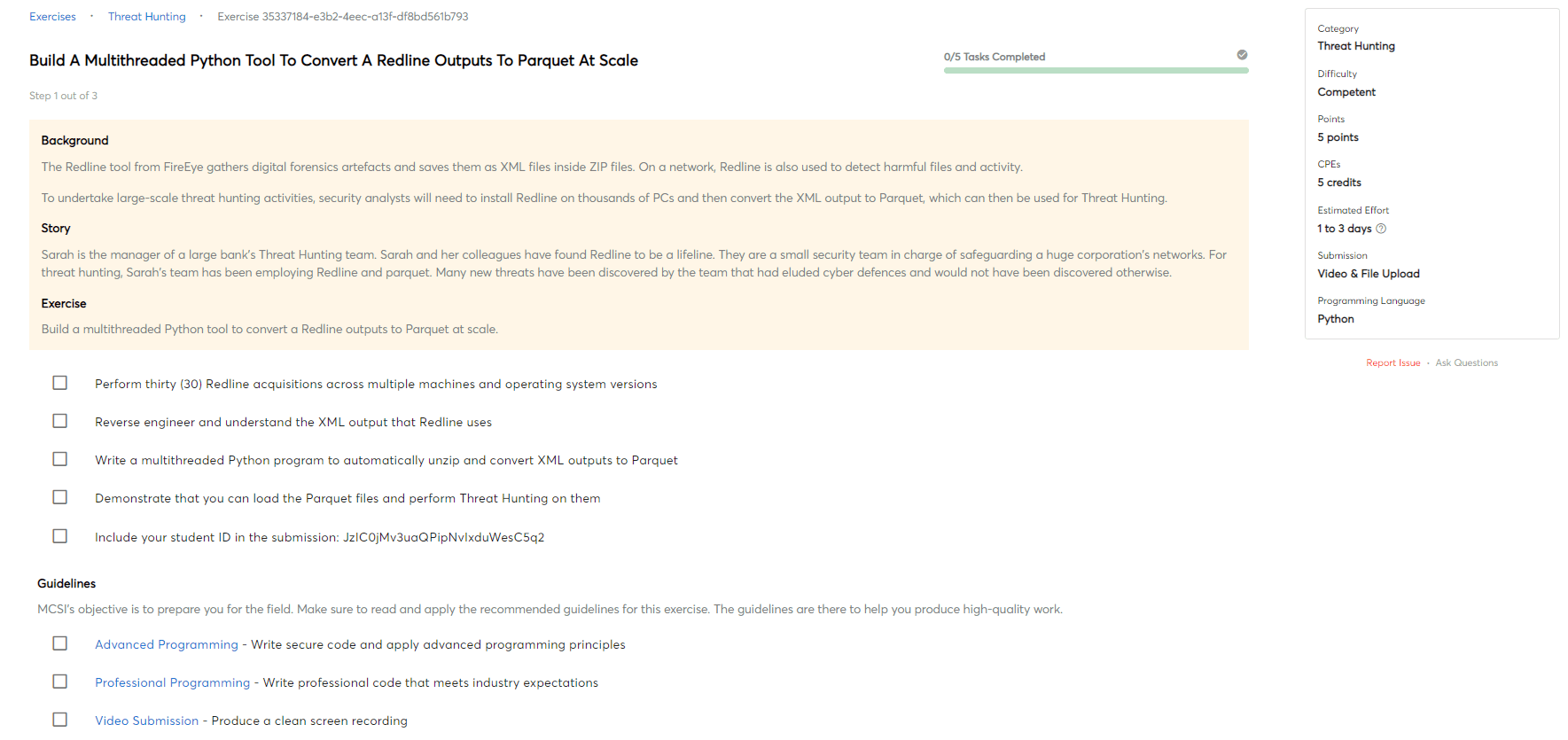
Network segmentation
Network segmentation for security is the process of logically separating a network into segments to improve security. Each segment is isolated from the others, so that if one segment is compromised, the other segments are not affected. Segmentation also makes it more difficult for attackers to move around the network and access sensitive data.
Intrusion detection and response
Intrusion detection and response is a process of monitoring the systems for any unauthorized activities and respond to it in the quickest possible manner. The main aim of this process is to prevent any potential damage to the system and also keep the confidential data safe.
Backup and recovery
Backup and recovery is the process of creating copies of data so that it can be restored if it is lost or damaged. This can include both data files and system files. The copies can be stored on removable media, such as disks or tapes, or on remote servers.

 Intermediate
Intermediate