|
1069A
|
Knowledge of general kill chain (e.g., footprinting and scanning, enumeration, gaining access, escalation of privileges, maintaining access, network exploitation, covering tracks).
|
|
108
|
Knowledge of risk management processes (e.g., methods for assessing and mitigating risk).
|
|
1158
|
Knowledge of cybersecurity principles.
|
|
1159
|
Knowledge of cyber threats and vulnerabilities.
|
|
150
|
Knowledge of what constitutes a network attack and the relationship to both threats and vulnerabilities.
|
|
19
|
Knowledge of cyber defense and vulnerability assessment tools, including open source tools, and their capabilities.
|
|
22
|
Knowledge of computer networking concepts and protocols, and network security methodologies.
|
|
66
|
Knowledge of intrusion detection methodologies and techniques for detecting host and network-based intrusions via intrusion detection technologies.
|
|
70
|
Knowledge of information technology (IT) security principles and methods (e.g., firewalls, demilitarized zones, encryption).
|
|
81A
|
Knowledge of network protocols such as TCP/IP, Dynamic Host Configuration, Domain Name System (DNS), and directory services.
|
|
87
|
Knowledge of network traffic analysis methods.
|
|
92
|
Knowledge of how traffic flows across the network (e.g., Transmission Control Protocol [TCP] and Internet Protocol [IP], Open System Interconnection Model [OSI], Information Technology Infrastructure Library, current version [ITIL]).
|
|
922A
|
Knowledge of how to use network analysis tools to identify vulnerabilities.
|
|
984
|
Knowledge of cyber defense policies, procedures, and regulations.
|
|
990
|
Knowledge of the common attack vectors on the network layer.
|
|
991
|
Knowledge of different classes of attacks (e.g., passive, active, insider, close-in, distribution).
|
|
6900
|
Knowledge of specific operational impacts of cybersecurity lapses.
|
|
25
|
Knowledge of encryption algorithms (e.g., Internet Protocol Security [IPSEC], Advanced Encryption Standard [AES], Generic Routing Encapsulation [GRE], Internet Key Exchange [IKE], Message Digest Algorithm [MD5], Secure Hash Algorithm [SHA], Triple Data Encryption Standard [3DES]).
|
|
27
|
Knowledge of cryptography and cryptographic key management concepts.
|
|
34
|
Knowledge of database systems.
|
|
49
|
Knowledge of host/network access control mechanisms (e.g., access control list).
|
|
58
|
Knowledge of known vulnerabilities from alerts, advisories, errata, and bulletins.
|
|
61
|
Knowledge of incident response and handling methodologies.
|
|
63
|
Knowledge of cybersecurity principles and organizational requirements (relevant to confidentiality, integrity, availability, authentication, non-repudiation).
|
|
79
|
Knowledge of network access, identity, and access management (e.g., public key infrastructure [PKI]).
|
|
88A
|
Knowledge of current and emerging cyber technologies.
|
|
90
|
Knowledge of operating systems.
|
|
95A
|
Knowledge of penetration testing principles, tools, and techniques.
|
|
98
|
Knowledge of policy-based and risk adaptive access controls.
|
|
105
|
Knowledge of system and application security threats and vulnerabilities (e.g., buffer overflow, mobile code, cross-site scripting, Procedural Language/Structured Query Language [PL/SQL] and injections, race conditions, covert channel, replay, return-oriented attacks, malicious code).
|
|
110
|
Knowledge of key concepts in security management (e.g., Release Management, Patch Management).
|
|
111
|
Knowledge of security system design tools, methods, and techniques.
|
|
130A
|
Knowledge of systems security testing and evaluation methods.
|
|
139
|
Knowledge of the common networking protocols (e.g., TCP/IP), services (e.g., web, mail, Domain Name Server), and how they interact to provide network communications.
|
|
148
|
Knowledge of Virtual Private Network (VPN) security.
|
|
177B
|
Knowledge of countermeasures for identified security risks.
|
|
212A
|
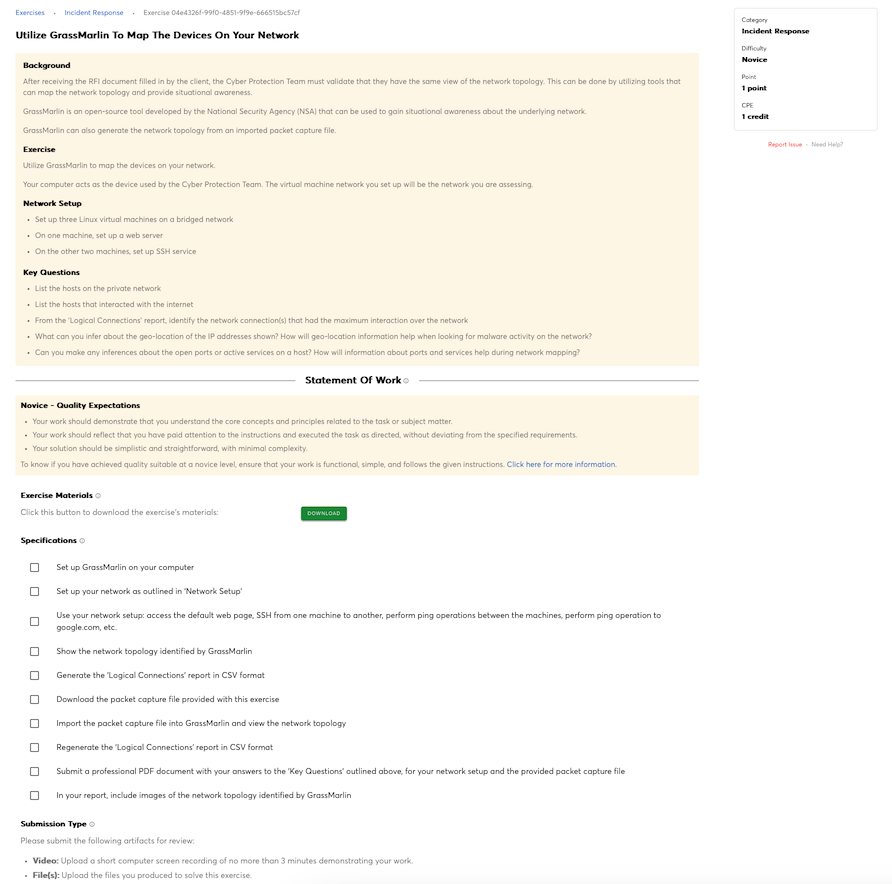
Knowledge of network mapping and recreating network topologies.
|
|
270
|
Knowledge of common adversary tactics, techniques, and procedures in assigned area of responsibility (i.e., historical country-specific tactics, techniques, and procedures; emerging capabilities).
|
|
271
|
Knowledge of common network tools (e.g., ping, traceroute, nslookup).
|
|
277
|
Knowledge of defense-in-depth principles and network security architecture.
|
|
278
|
Knowledge of different types of network communication (e.g., LAN, WAN, MAN, WLAN, WWAN).
|
|
286
|
Knowledge of file extensions (e.g., .dll, .bat, .zip, .pcap, .gzip).
|
|
342A
|
Knowledge of operating system command line/prompt.
|
|
904
|
Knowledge of interpreted and compiled computer languages.
|
|
912
|
Knowledge of collection management processes, capabilities, and limitations.
|
|
915
|
Knowledge of front-end collection systems, including traffic collection, filtering, and selection.
|
|
1033
|
Knowledge of basic system administration, network, and operating system hardening techniques.
|
|
1034C
|
Knowledge of Personal Health Information (PHI) data security standards.
|
|
1034B
|
Knowledge of Payment Card Industry (PCI) data security standards.
|
|
1034A
|
Knowledge of Personally Identifiable Information (PII) data security standards.
|
|
1072
|
Knowledge of network security architecture concepts including topology, protocols, components, and principles (e.g., application of defense-in-depth).
|
|
1073
|
Knowledge of network systems management principles, models, methods (e.g., end-to-end systems performance monitoring), and tools.
|
|
1114
|
Knowledge of encryption methodologies.
|
|
1119
|
Knowledge of signature implementation impact.
|
|
1121
|
Knowledge of Windows/Unix ports and services.
|
|
3431
|
Knowledge of OSI model and underlying network protocols (e.g., TCP/IP).
|
|
6935
|
Knowledge of cloud computing service models Software as a Service (SaaS), Infrastructure as a Service (IaaS), and Platform as a Service (PaaS).
|
|
6938
|
Knowledge of cloud computing deployment models in private, public, and hybrid environment and the difference between on-premises and off-premises environments.
|
|
43A
|
Knowledge of embedded systems.
|
|
133
|
Knowledge of key telecommunications concepts (e.g., Routing Algorithms, Fiber Optics Systems Link Budgeting, Add/Drop Multiplexers).
|
|
59A
|
Knowledge of Intrusion Detection System (IDS)/Intrusion Prevention System (IPS) tools and applications.
|
|
8
|
Knowledge of authentication, authorization, and access control methods.
|
|
21
|
Knowledge of computer algorithms.
|
|
138
|
Knowledge of the cyber defense Service Provider reporting structure and processes within one’s own organization.
|
|
234B
|
Knowledge of the use of sub-netting tools.
|
|
992C
|
Knowledge of threat environments (e.g., first generation threat actors, threat activities).
|
|
1036
|
Knowledge of applicable laws (e.g., Electronic Communications Privacy Act, Foreign Intelligence Surveillance Act, Protect America Act, search and seizure laws, civil liberties and privacy laws), statutes (e.g., in Titles 10, 18, 32, 50 in U.S. Code), Presidential Directives, executive branch guidelines, and/or administrative/criminal legal guidelines and procedures relevant to work performed.
|
|
1142
|
Knowledge of security models (e.g., Bell-LaPadula model, Biba integrity model, Clark-Wilson integrity model).
|
|
6210
|
Knowledge of cloud service models and possible limitations for an incident response.
|

 Intermediate
Intermediate