Master Cyber Tradecraft
Our real-world education will unlock your true cyber security abilities and boost your career
Every exercise simulates an apprenticeship. We train you to the level you are expected to perform in the real-world.
You receive expert feedback to strengthen your performance. All your skills are tested, analyzed, and improved.
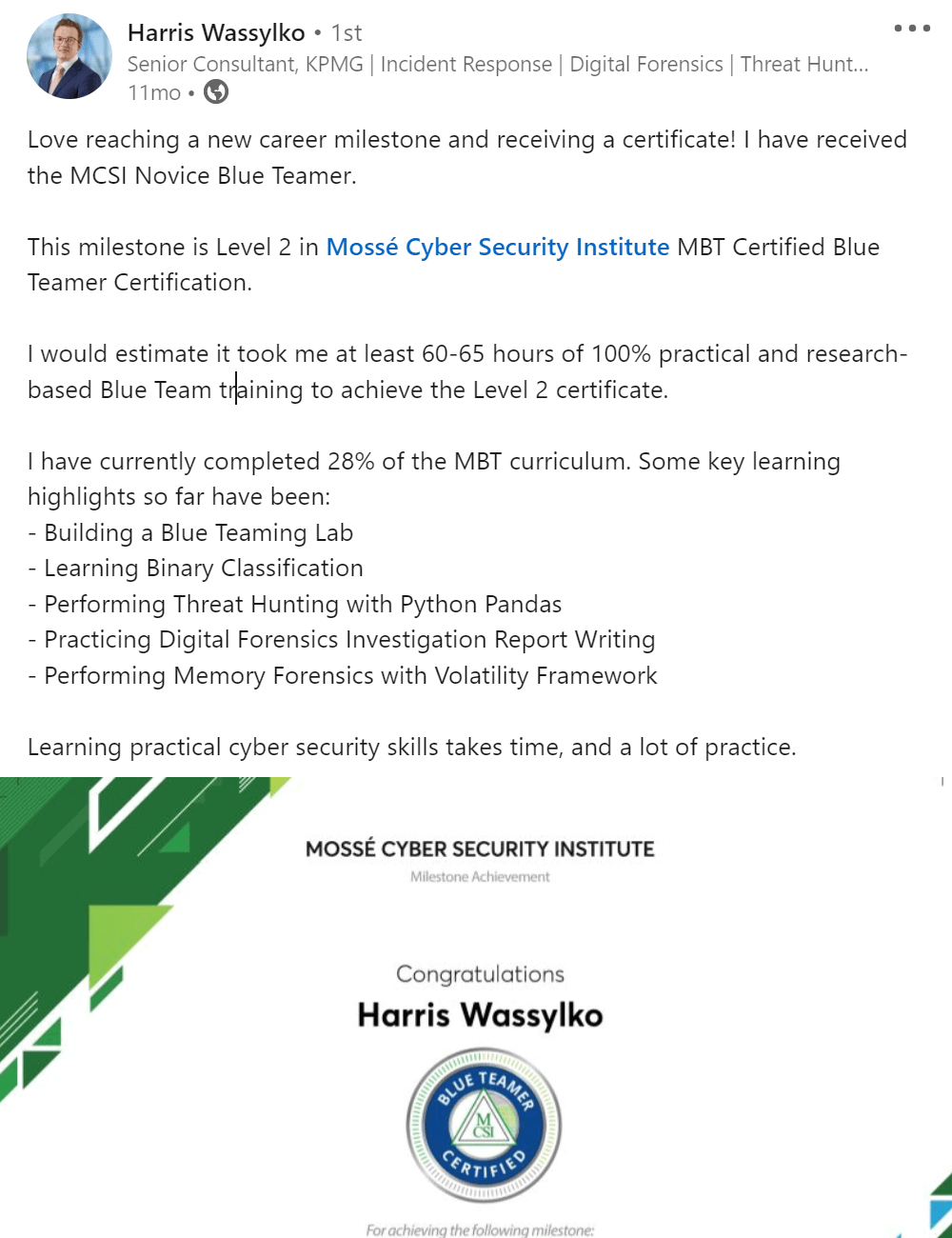
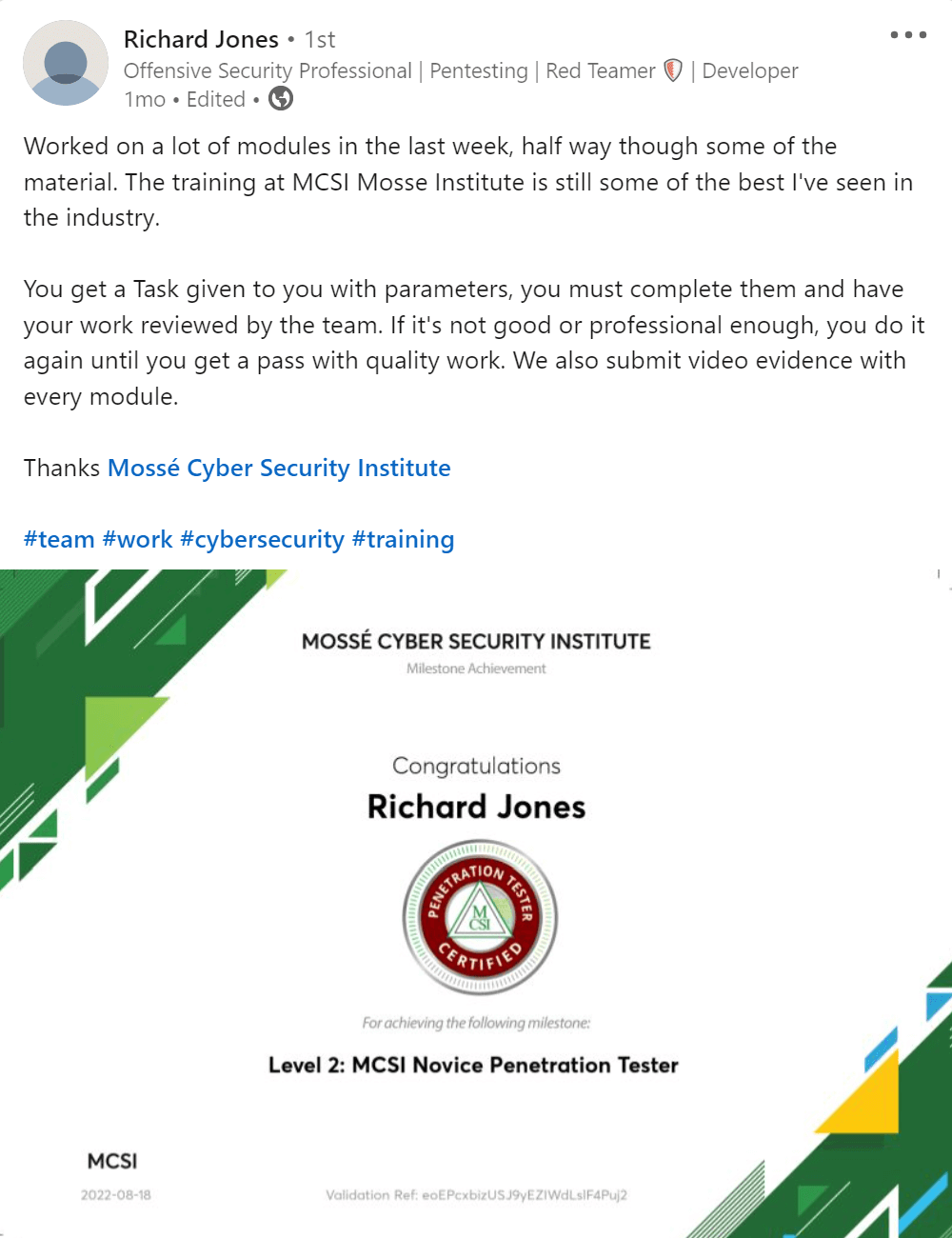
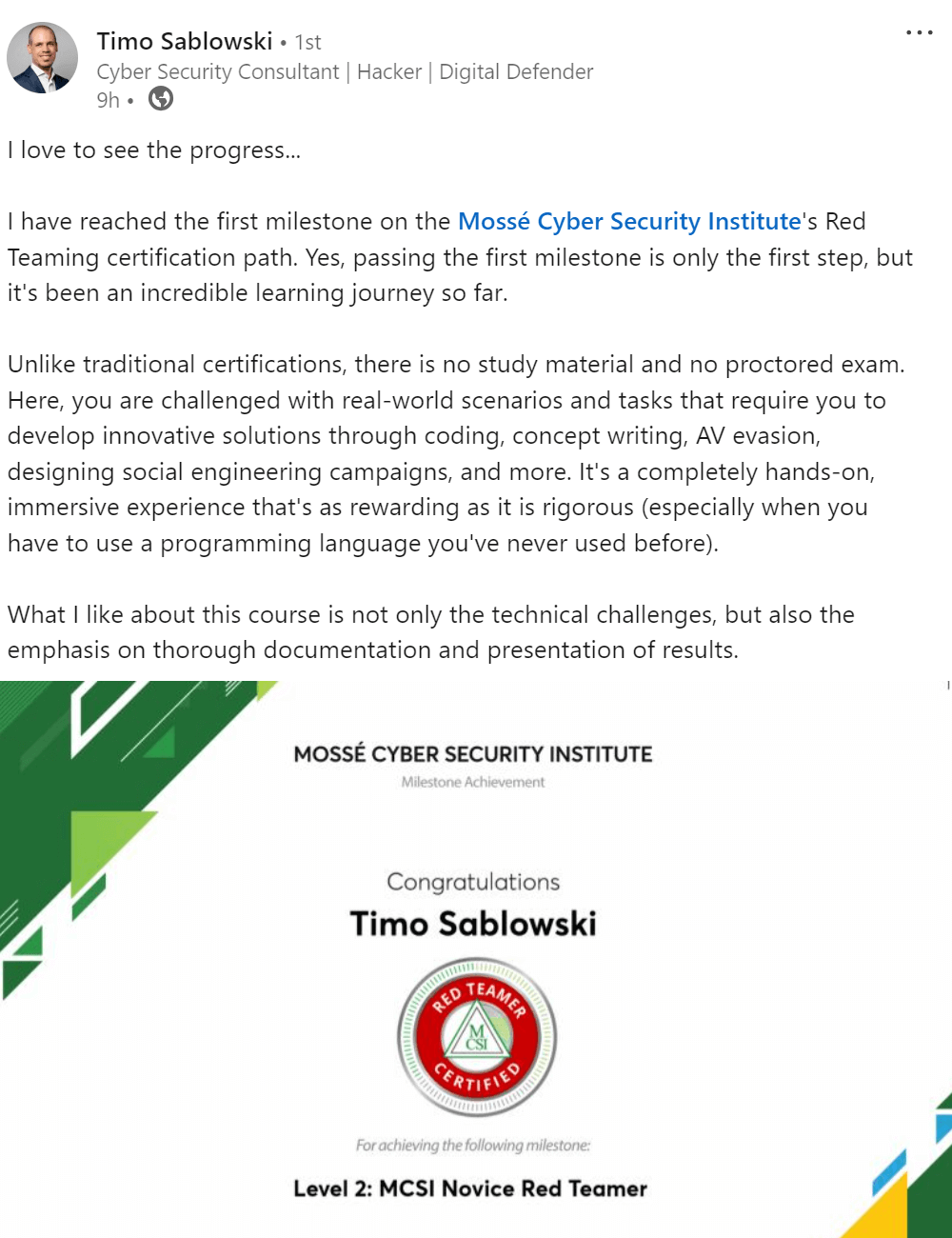
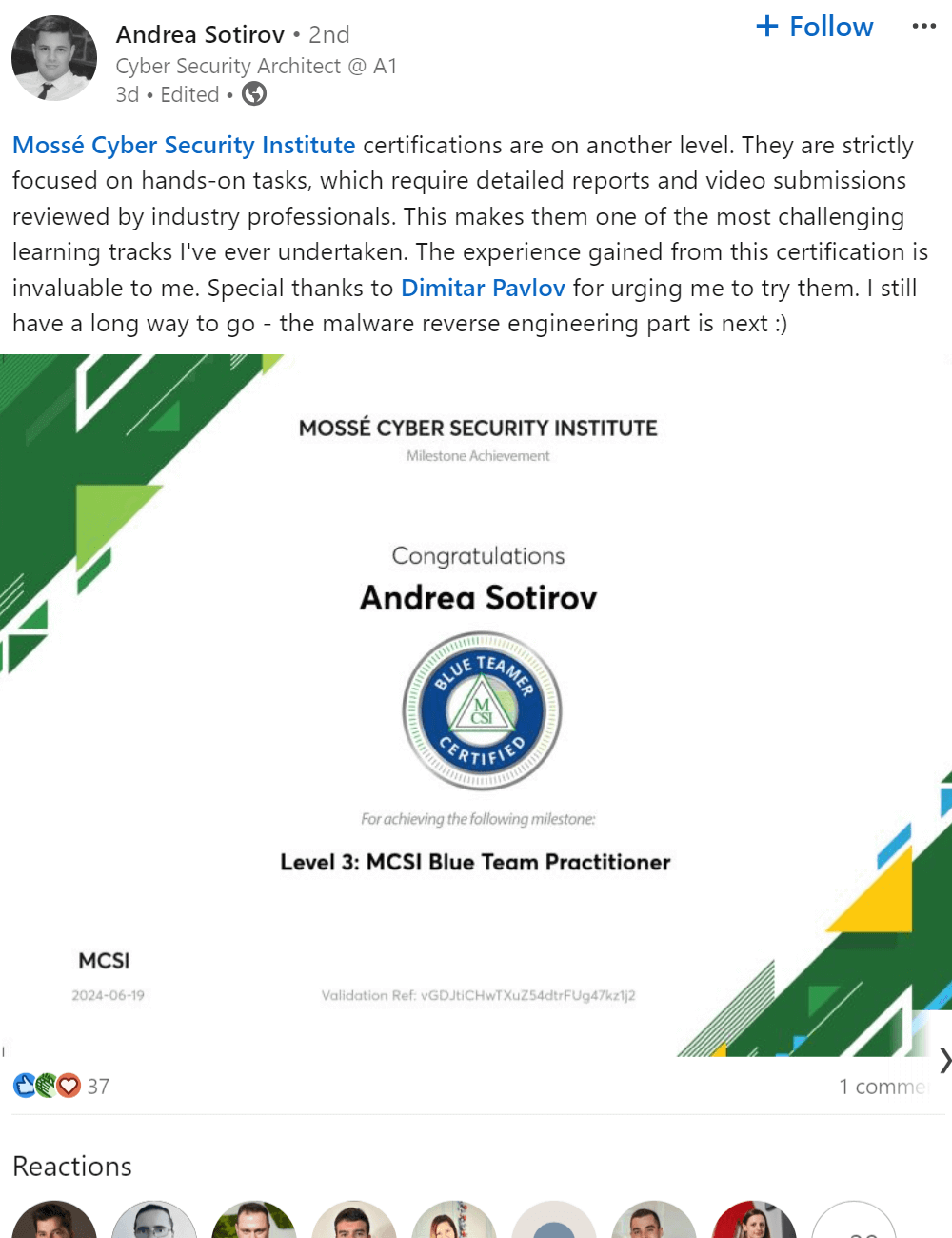
As you progress and reach milestones, MCSI provides you certificates and artefacts to promote and advance your career.
MCSI Method vs. Legacy Training
| Legacy Training | MCSI Method | MCSI Proven Success | |
|---|---|---|---|
| I want to land a job in cyber: |
Memorization tests Step-by-step instructions Paper Certifications |
Critical Thinking Problem Solving Portfolio of Skills |
Employers want problem solvers: 95% of our graduates landed jobs |
| I want to join the elite 10%: |
Guided Solutions Pre-scripted Labs Simplified Environments |
No solutions Research based Personalized Feedback |
In the real world, research is the way: 88% say MCSI elevated their skills |
| I want to make a wise financial choice: |
$5000 - $9000 54 Hours + Exam & Renewal Fees |
$450 - $699 600 Hours Lifetime Access |
Save 90% and get 11x more training hours |
Our proven training method elevates cyber operators to the top 10% of the industry—the results speak for themselves.
We empower both beginners and experts to accelerate their careers and reach new heights
- 95% of users completing our Remote Internship or an intermediate course landed cybersecurity jobs
- 84% reported an increased confidence in their real-world cybersecurity abilities
- 76% said MCSI training opened new career opportunities
- 71% said managers recognized their skills improvement
We elevate our users to elite levels through the most realistic cyber training on the planet
- With just 600 hours of MCSI training, users transform from beginners to expert practitioners—creating tools, presenting at conferences, and being recognized as top talent in their organizations
- 88% of users reported that MCSI transformed their work approach—enabling greater autonomy, fostering creativity, enhancing problem-solving skills, and improving their ability to meet work expectations
- 44% of our top users are directly involved in protecting critical infrastructure and national security
Our training transforms lives, empowering users to achieve their personal goals
- Many of our users have secured roles in tier-1 cybersecurity teams and contributed to high-profile projects featured in global news, thanks in part to our courses
- Some users received visa sponsorships, enabling them to move from developing countries to the UK, United States, and Australia to work for top firms
- Several users overcame financial challenges by securing remote freelance or contract roles, rising to the top 5% of IT earners in their countries
We certify cyber practitioners weekly, with results independently verifiable. Our users produce artifacts that employers can audit to confirm their skills—an unmatched capability for those who need to hire top talent.
Services

 40,000+ students
40,000+ students