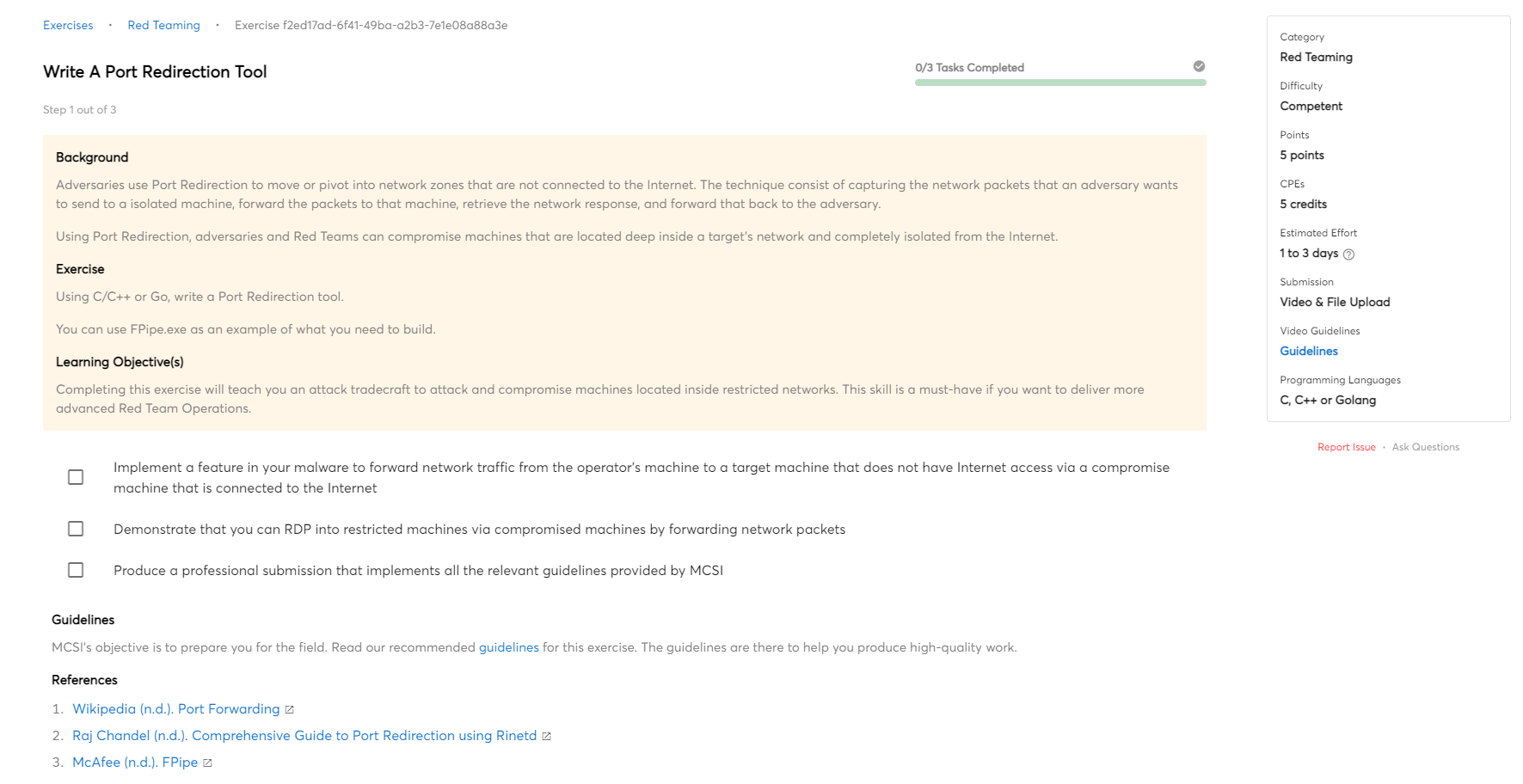
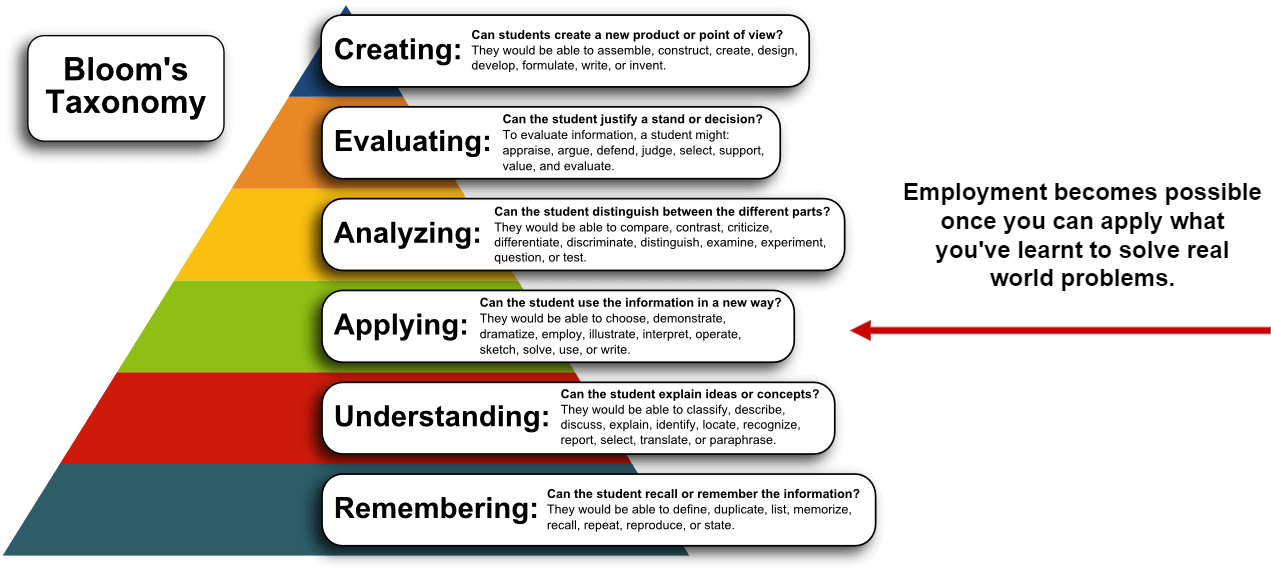
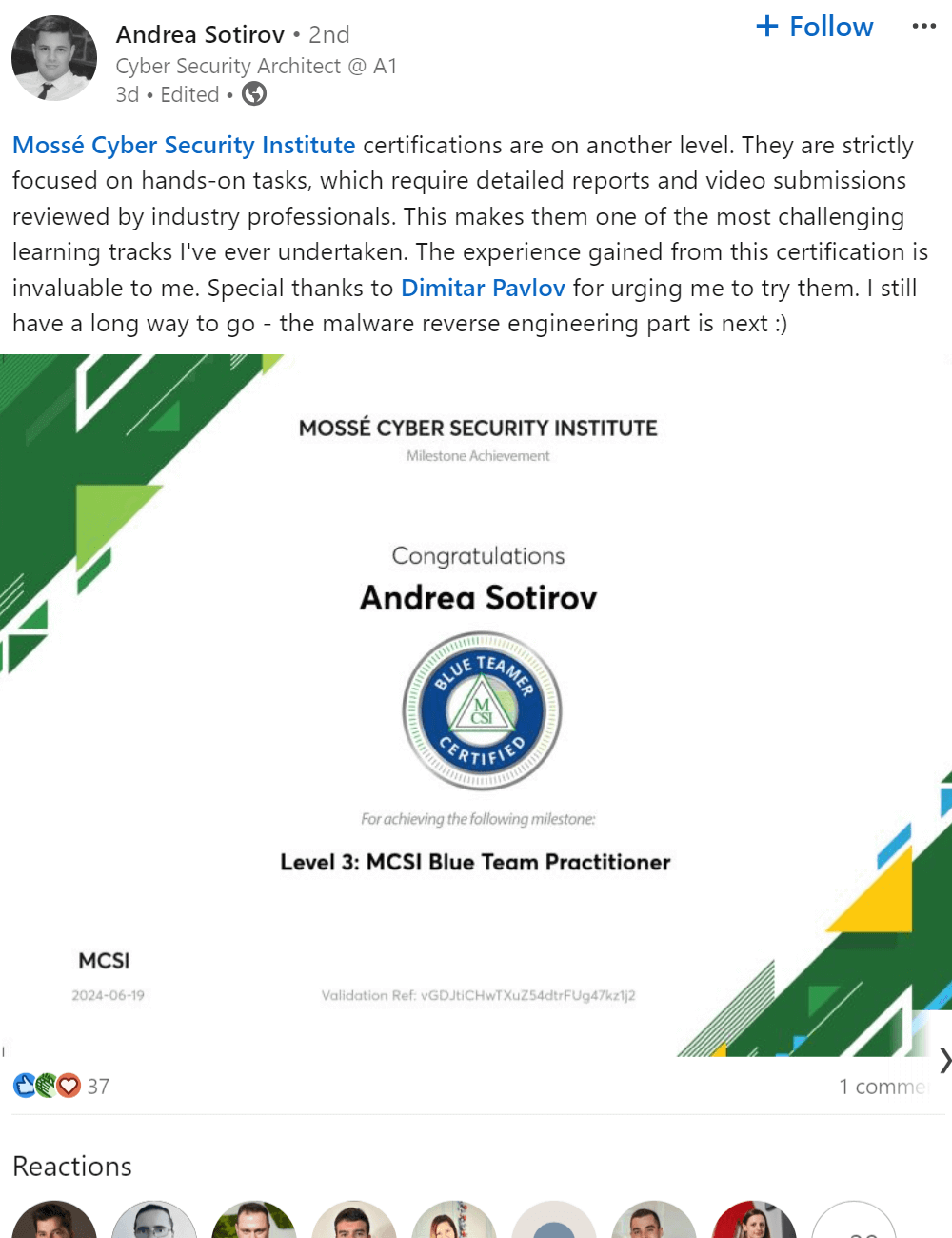
The MITRE matrix is a tool that helps Red Teams plan their operations. The matrix provides a breakdown of the different areas that need to be considered when planning a Red Team attack. This information can help Red Teams tailor their attacks to be more effective.
Initial Access
In the initial access phase, the red team is attempting to get a foothold into the target network. They will typically use a variety of techniques to get inside, such as social engineering, spear phishing, and malware. Once they have a foothold, they can begin to explore the network and look for vulnerabilities that they can exploit.
Execution
Red teamers will often execute malicious code on a target machine in order to gain access to sensitive information. Once the code is executed, it will give the red teamer access to the target machine and all of its data. Execution refers to the tools and techniques they use to execute code.
Persistence
Persistence is the ability for an attacker to maintain access to a compromised system for an extended period of time. This can be done through a number of methods, such as installing backdoors, using stolen credentials, or compromising other systems within the network. By maintaining access, the attacker can continue to gather information or launch further attacks against the organization.
Defence Evasion
In a red teaming operation, defence evasion are techniques used to evade, avoid and frustrate the cyber defenders. This can be done through the use of deception or by actively hindering the defender's ability to collect information. The goal is to make it more difficult for the defenders to understand the red team's activities.
Credential Access
Credential access is a critical step during a red team operation. The goal is to gain access to as many systems and user accounts as possible in order to increase the scope of the attack and increase the chances of achieving the mission objectives. Various methods can be used to obtain credentials, such as exploit vulnerabilities, social engineering, or brute force attacks. Once credentials are obtained, they can be used to access additional systems and user accounts, as well as to gather sensitive information.
Asset Discovery
Asset Discovery is a process that is used during Red Teaming Operations in order to identify and map out all of the assets that are present on the target network. This includes identifying devices, servers, applications, and any other type of asset that may be present. Asset Discovery can be performed manually or using automated tools, and is an essential part of any Red Teaming operation.
Lateral Movement
Lateral movement is the ability of an attacker to move through a compromised network to other systems or networks. Attackers use lateral movement to gain access to additional systems and data, and to expand their control of the network. Lateral movement can be accomplished through various means, including exploiting vulnerabilities, using stolen credentials, and using malware.
Data Collection
The data collection process in Red Teaming Operations is the method by which data is gathered from various compromised machines, sources and consolidated for use in further analysis. Data can be collected from a variety of sources, including both internal and external networks, systems, and data stores.
Exfiltration
Red Teaming Operations often requires the attacker to exfiltrate data from the target environment. Exfiltration is the process of transferring data out of a network or system, and it can be done in a number of ways.
Command and Control
Command and Control (C2) is the means by which a cyber operator communicates with and controls their compromised target. In a Red Teaming operation, C2 is often used to issue commands to the target system and to extract or upload data.

 Advanced
Advanced