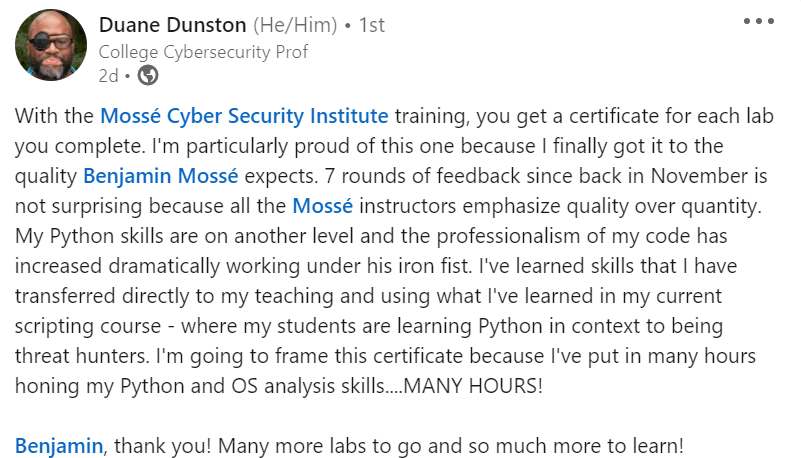
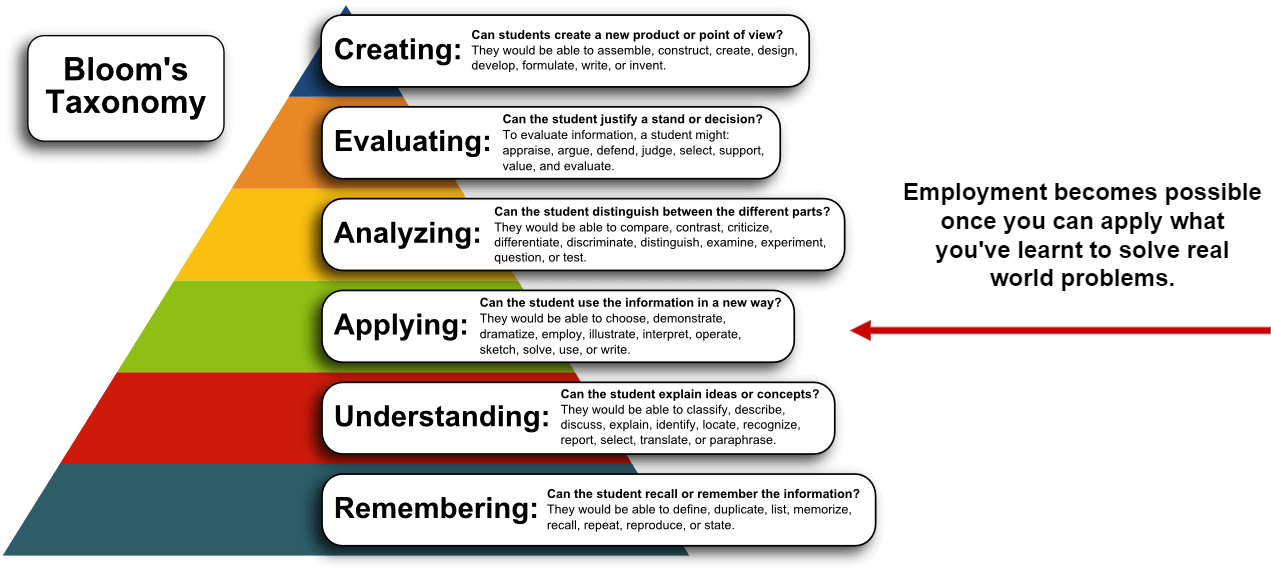
|
22
|
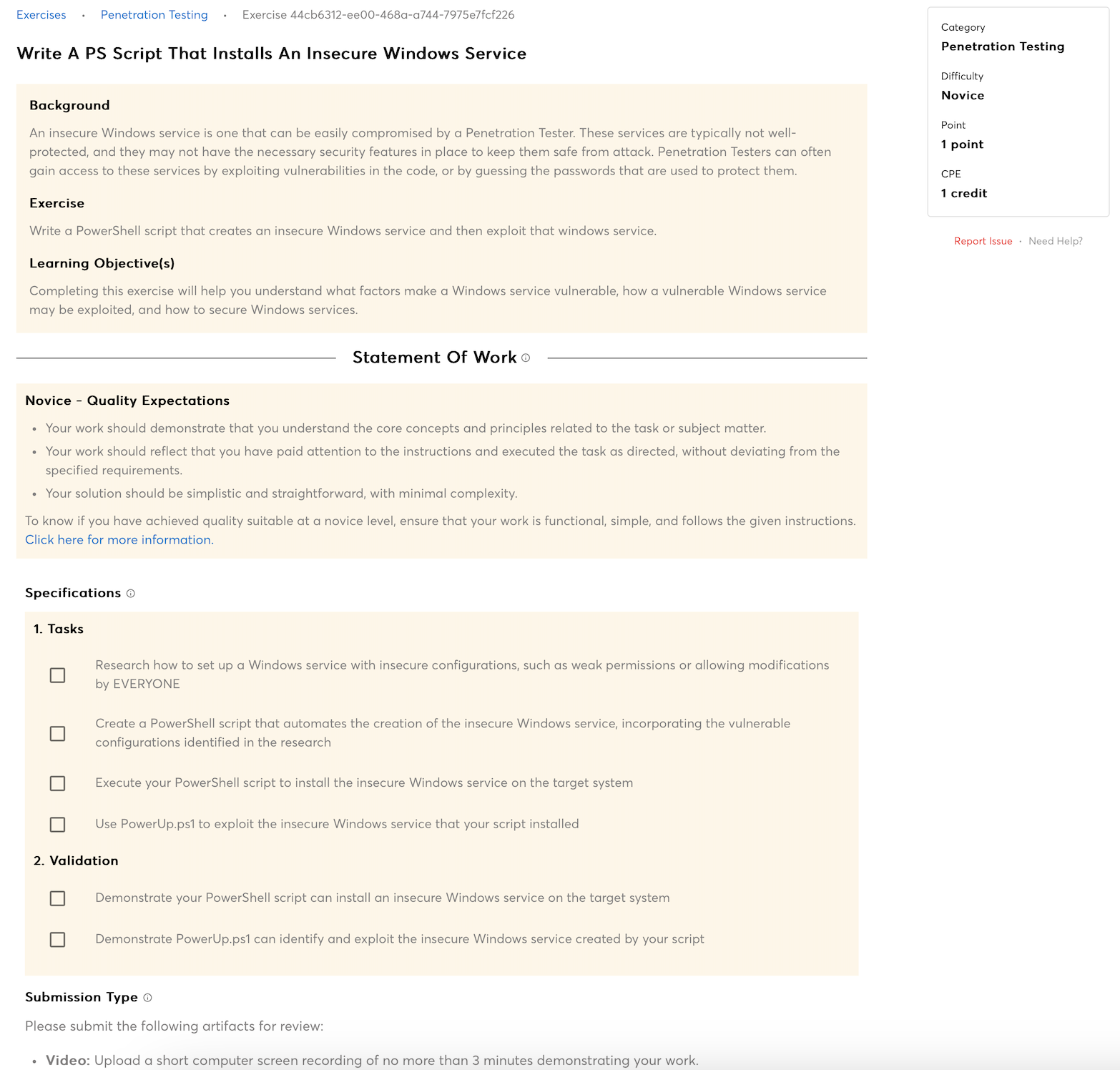
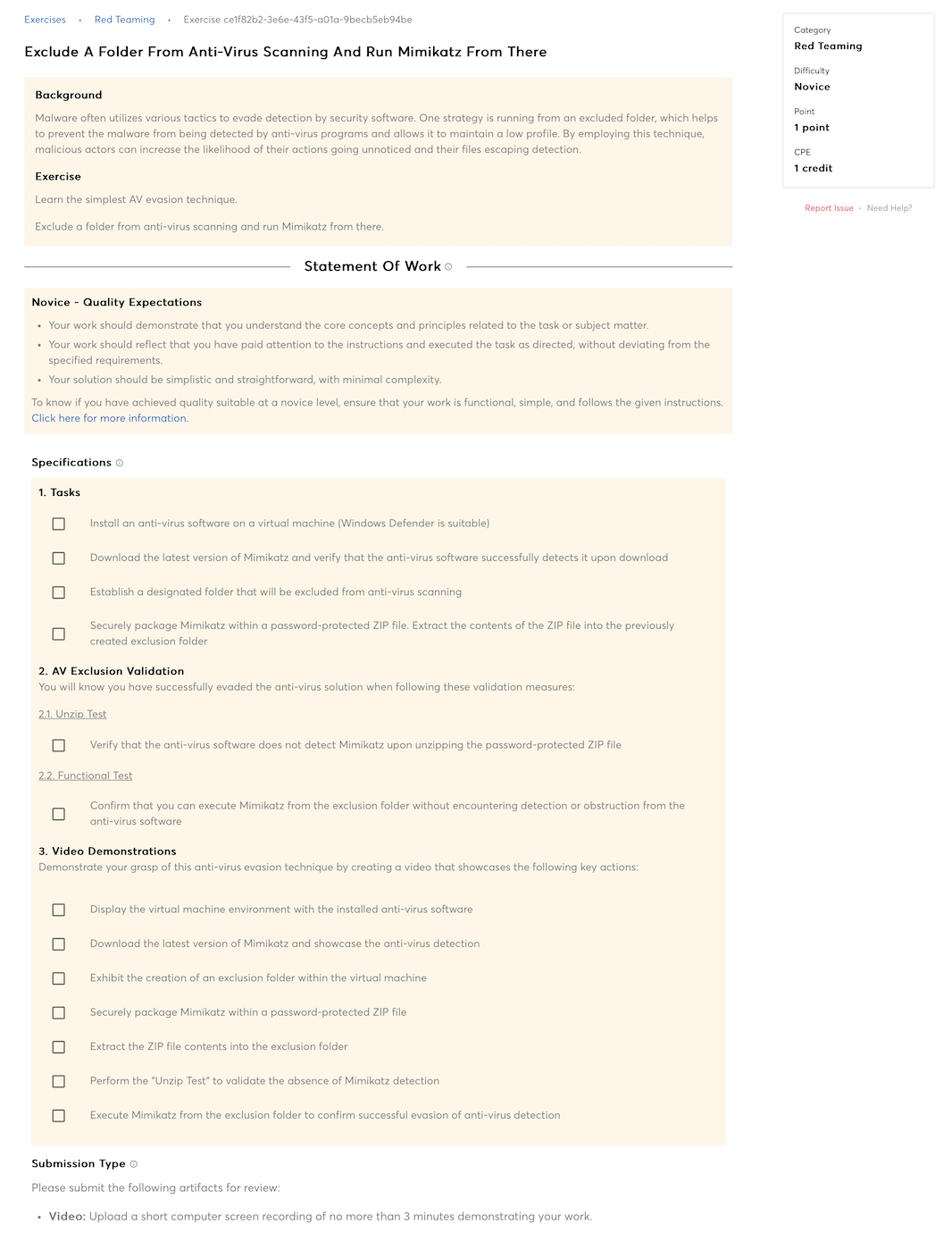
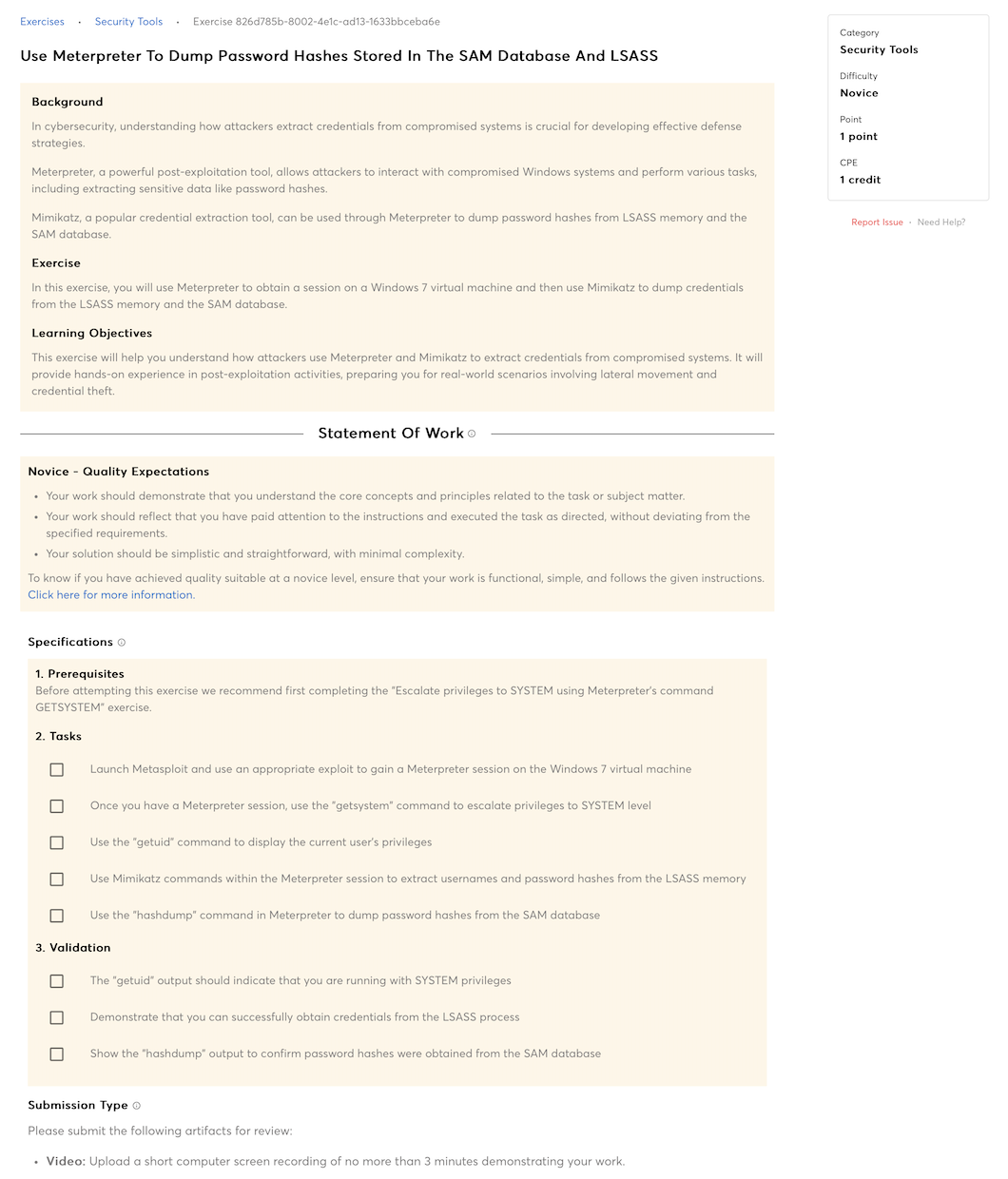
Knowledge of computer networking concepts and protocols, and network security methodologies.
|
|
108
|
Knowledge of risk management processes (e.g., methods for assessing and mitigating risk).
|
|
264
|
Knowledge of basic physical computer components and architectures, including the functions of various components and peripherals (e.g., CPUs, Network Interface Cards, data storage).
|
|
1158
|
Knowledge of cybersecurity principles.
|
|
1159
|
Knowledge of cyber threats and vulnerabilities.
|
|
3095
|
Knowledge of internet network addressing (IP addresses, classless inter-domain routing, TCP/UDP port numbering).
|
|
3106
|
Knowledge of a wide range of basic communications media concepts and terminology (e.g., computer and telephone networks, satellite, cable, wireless).
|
|
3107
|
Knowledge of a wide range of concepts associated with websites (e.g., website types, administration, functions, software systems, etc.).
|
|
3129
|
Knowledge of attack methods and techniques (DDoS, brute force, spoofing, etc.).
|
|
3137
|
Knowledge of basic malicious activity concepts (e.g., foot printing, scanning and enumeration).
|
|
3179
|
Knowledge of common networking devices and their configurations.
|
|
3191
|
Knowledge of concepts for operating systems (e.g., Linux, Unix).
|
|
3225
|
Knowledge of data communications terminology (e.g., networking protocols, Ethernet, IP, encryption, optical devices, removable media).
|
|
3289
|
Knowledge of how hubs, switches, routers work together in the design of a network.
|
|
3291
|
Knowledge of how internet applications work (SMTP email, web-based email, chat clients, VOIP).
|
|
3346
|
Knowledge of Internet and routing protocols.
|
|
3407
|
Knowledge of network security (e.g., encryption, firewalls, authentication, honey pots, perimeter protection).
|
|
3410
|
Knowledge of network topology.
|
|
3513
|
Knowledge of system administration concepts for Unix/Linux and/or Windows operating systems.
|
|
3543
|
Knowledge of the basic structure, architecture, and design of modern communication networks.
|
|
6900
|
Knowledge of specific operational impacts of cybersecurity lapses.
|
|
345
|
Knowledge of web mail collection, searching/analyzing techniques, tools, and cookies.
|
|
912
|
Knowledge of collection management processes, capabilities, and limitations.
|
|
915
|
Knowledge of front-end collection systems, including traffic collection, filtering, and selection.
|
|
3055B
|
Knowledge of basic implants.
|
|
3113
|
Knowledge of target intelligence gathering and operational preparation techniques and life cycles.
|
|
3139
|
Knowledge of basic principles of the collection development processes (e.g., Dialed Number Recognition, Social Network Analysis).
|
|
3146
|
Knowledge of both internal and external customers and partner organizations, including information needs, objectives, structure, capabilities, etc.
|
|
3155
|
Knowledge of client organizations, including information needs, objectives, structure, capabilities, etc.
|
|
3166
|
Knowledge of collection searching/analyzing techniques and tools for chat/buddy list, emerging technologies, VOIP, Media Over IP, VPN, VSAT/wireless, web mail and cookies.
|
|
3181
|
Knowledge of common reporting databases and tools.
|
|
3201
|
Knowledge of all relevant reporting and dissemination procedures.
|
|
3226
|
Knowledge of data flow process for terminal or environment collection.
|
|
3256
|
Knowledge of terminal or environmental collection (process, objectives, organization, targets, etc.).
|
|
3261
|
Knowledge of evasion strategies and techniques.
|
|
3296
|
Knowledge of how to collect, view, and identify essential information on targets of interest from metadata (e.g., email, http).
|
|
3349
|
Knowledge of intrusion sets.
|
|
3386
|
Knowledge of midpoint collection (process, objectives, organization, targets, etc.).
|
|
3432
|
Knowledge of identification and reporting processes.
|
|
3454
|
Knowledge of products and nomenclature of major vendors (e.g., security suites – Trend Micro, Symantec, McAfee, Outpost, Panda, Kaspersky) and how differences affect exploitation/vulnerabilities.
|
|
3474
|
Knowledge of scripting
|
|
3505
|
Knowledge of strategies and tools for target research.
|
|
3525
|
Knowledge of organizational and partner policies, tools, capabilities, and procedures.
|
|
3542
|
Knowledge of the basic structure, architecture, and design of converged applications.
|
|
3622
|
Knowledge of organizational and partner authorities, responsibilities, and contributions to achieving objectives.
|
|
3637
|
Knowledge of Unix/Linux and Windows operating systems structures and internals (e.g., process management, directory structure, installed applications).
|

 Advanced
Advanced