|
10
|
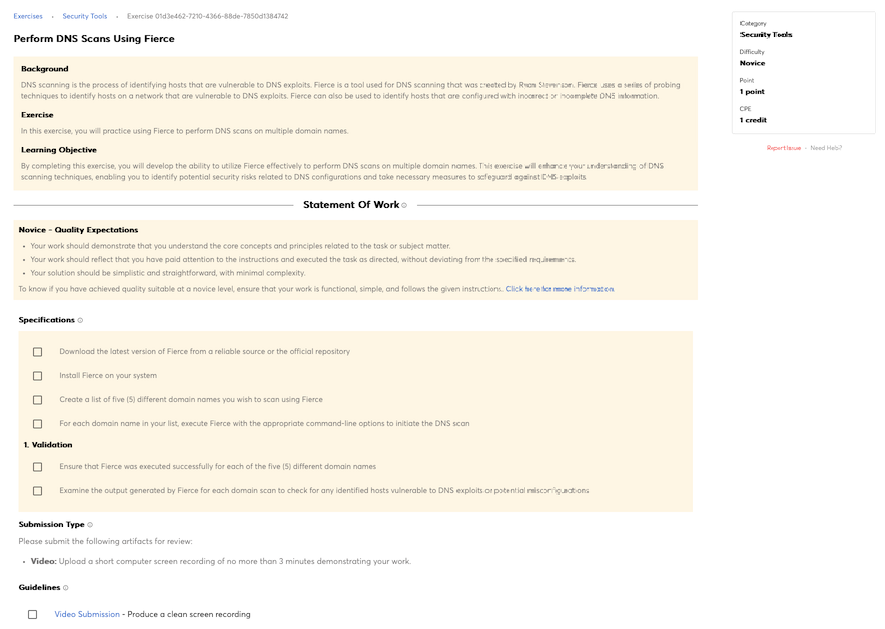
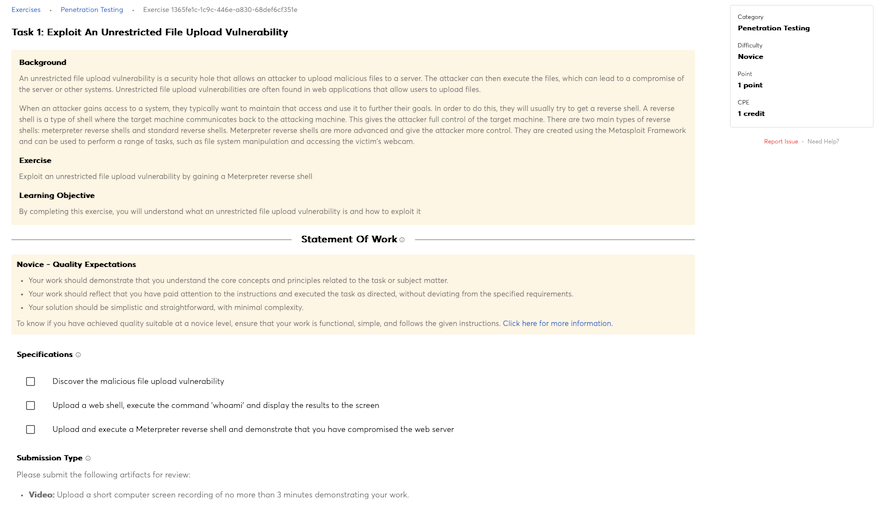
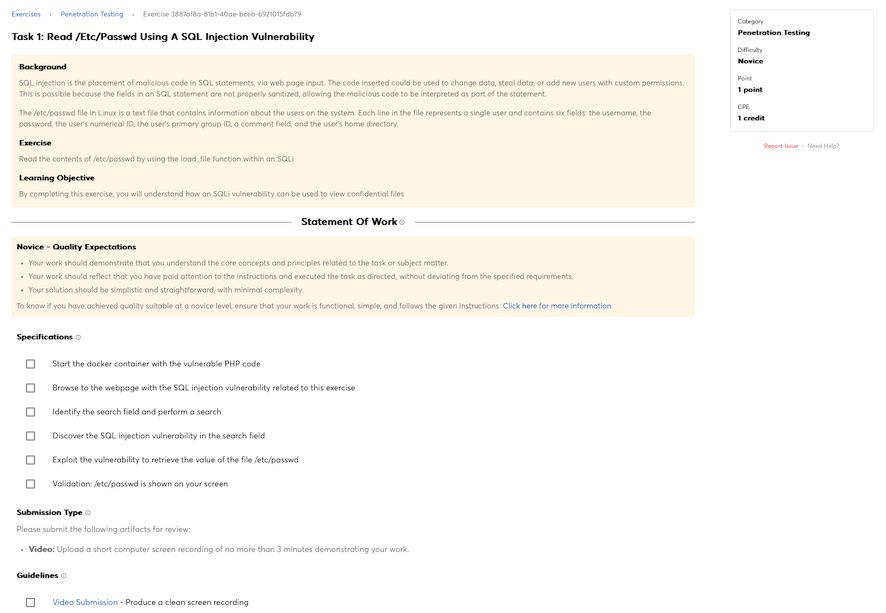
Knowledge of application vulnerabilities.
|
|
22
|
Knowledge of computer networking concepts and protocols, and network security methodologies.
|
|
92
|
Knowledge of how traffic flows across the network (e.g., Transmission Control Protocol [TCP] and Internet Protocol [IP], Open System Interconnection Model [OSI], Information Technology Infrastructure Library, current version [ITIL]).
|
|
105
|
Knowledge of system and application security threats and vulnerabilities (e.g., buffer overflow, mobile code, cross-site scripting, Procedural Language/Structured Query Language [PL/SQL] and injections, race conditions, covert channel, replay, return-oriented attacks, malicious code).
|
|
108
|
Knowledge of risk management processes (e.g., methods for assessing and mitigating risk).
|
|
150
|
Knowledge of what constitutes a network attack and the relationship to both threats and vulnerabilities.
|
|
1072
|
Knowledge of network security architecture concepts including topology, protocols, components, and principles (e.g., application of defense-in-depth).
|
|
1158
|
Knowledge of cybersecurity principles.
|
|
1159
|
Knowledge of cyber threats and vulnerabilities.
|
|
6900
|
Knowledge of specific operational impacts of cybersecurity lapses.
|
|
6935
|
Knowledge of cloud computing service models Software as a Service (SaaS), Infrastructure as a Service (IaaS), and Platform as a Service (PaaS).
|
|
6938
|
Knowledge of cloud computing deployment models in private, public, and hybrid environment and the difference between on-premises and off-premises environments.
|
|
27
|
Knowledge of cryptography and cryptographic key management concepts.
|
|
29
|
Knowledge of data backup, types of backups (e.g., full, incremental), and recovery concepts and tools.
|
|
49
|
Knowledge of host/network access control mechanisms (e.g., access control list).
|
|
63
|
Knowledge of cybersecurity principles and organizational requirements (relevant to confidentiality, integrity, availability, authentication, non-repudiation).
|
|
79
|
Knowledge of network access, identity, and access management (e.g., public key infrastructure [PKI]).
|
|
81A
|
Knowledge of network protocols such as TCP/IP, Dynamic Host Configuration, Domain Name System (DNS), and directory services.
|
|
95B
|
Knowledge of penetration testing principles, tools, and techniques, including specialized tools for non-traditional systems and networks (e.g., control systems).
|
|
102
|
Knowledge of programming language structures and logic.
|
|
128
|
Knowledge of systems diagnostic tools and fault identification techniques.
|
|
214B
|
Knowledge of packet-level analysis using appropriate tools (e.g., Wireshark, tcpdump).
|
|
801B
|
Knowledge of threat and risk assessment.
|
|
904
|
Knowledge of interpreted and compiled computer languages.
|
|
991
|
Knowledge of different classes of attacks (e.g., passive, active, insider, close-in, distribution).
|
|
992C
|
Knowledge of threat environments (e.g., first generation threat actors, threat activities).
|
|
992B
|
Knowledge of cyber attackers (e.g., script kiddies, insider threat, non-nation state sponsored, and nation sponsored).
|
|
1033
|
Knowledge of basic system administration, network, and operating system hardening techniques.
|
|
1038A
|
Knowledge of infrastructure supporting information technology (IT) for safety, performance, and reliability.
|
|
1069
|
Knowledge of general attack stages (e.g., foot printing and scanning, enumeration, gaining access, escalation or privileges, maintaining access, network exploitation, covering tracks).
|
|
1141A
|
Knowledge of an organization’s information classification program and procedures for information compromise.
|
|
1142
|
Knowledge of security models (e.g., Bell-LaPadula model, Biba integrity model, Clark-Wilson integrity model).
|
|
3150
|
Knowledge of ethical hacking principles and techniques.
|
|
3222
|
Knowledge of data backup and restoration concepts.
|
|
3513
|
Knowledge of system administration concepts for Unix/Linux and/or Windows operating systems.
|
|
6210
|
Knowledge of cloud service models and possible limitations for an incident response.
|

 Intermediate
Intermediate