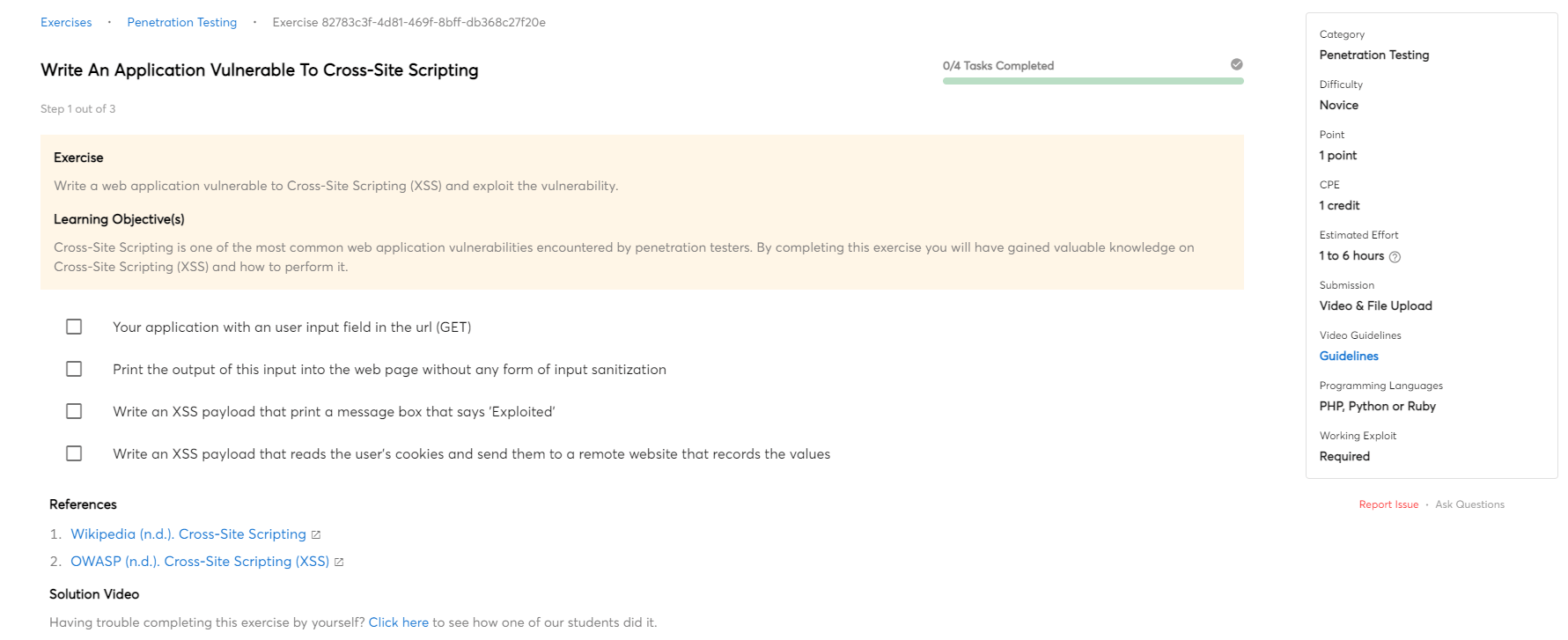
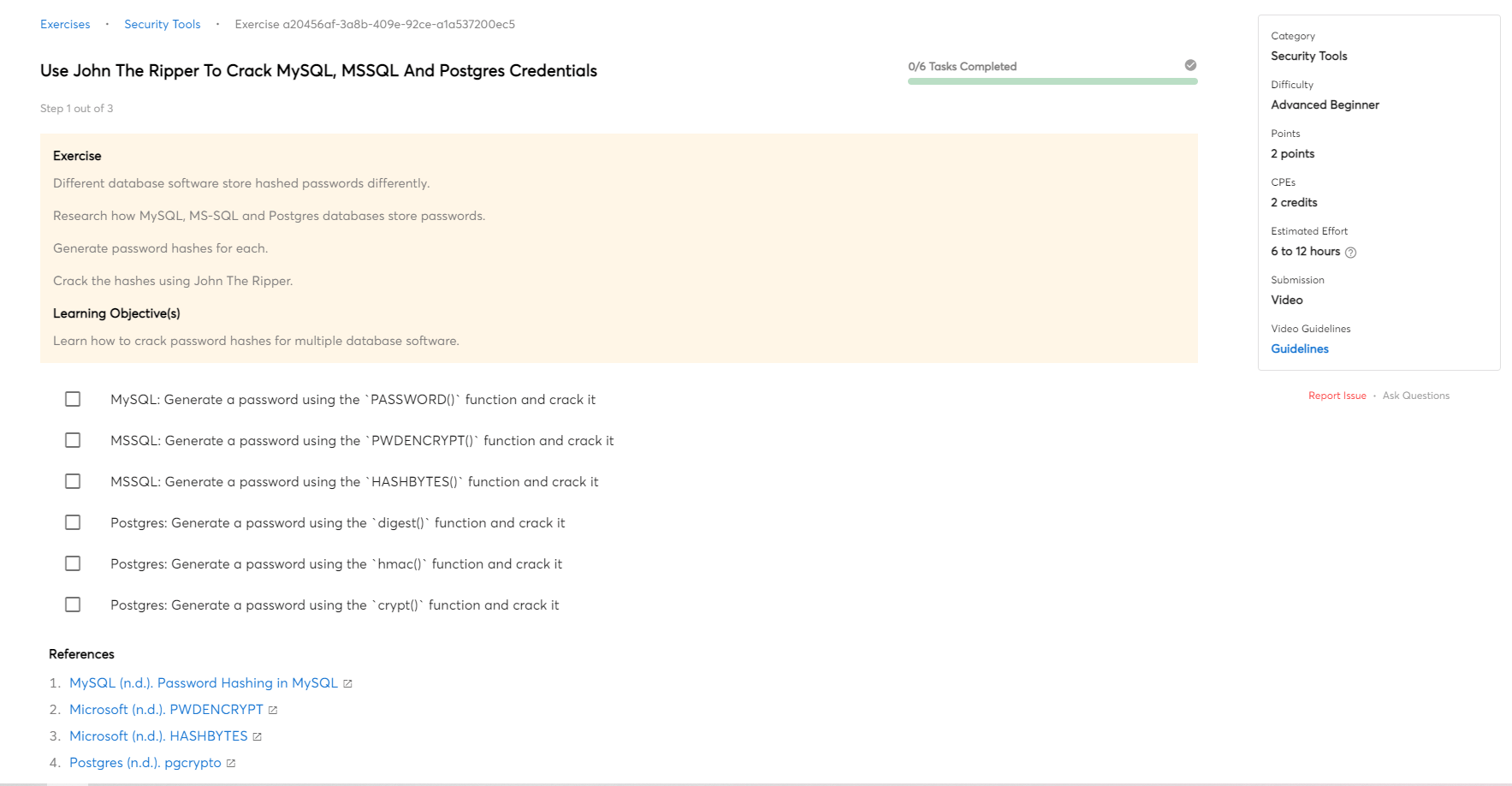
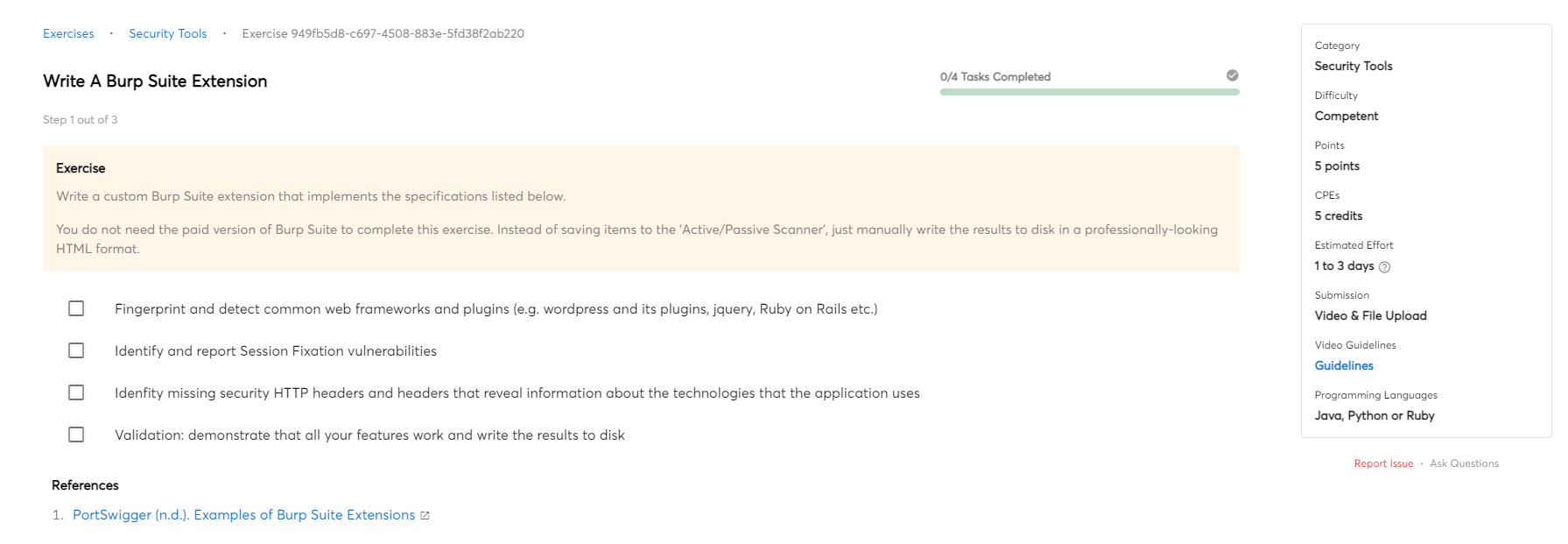
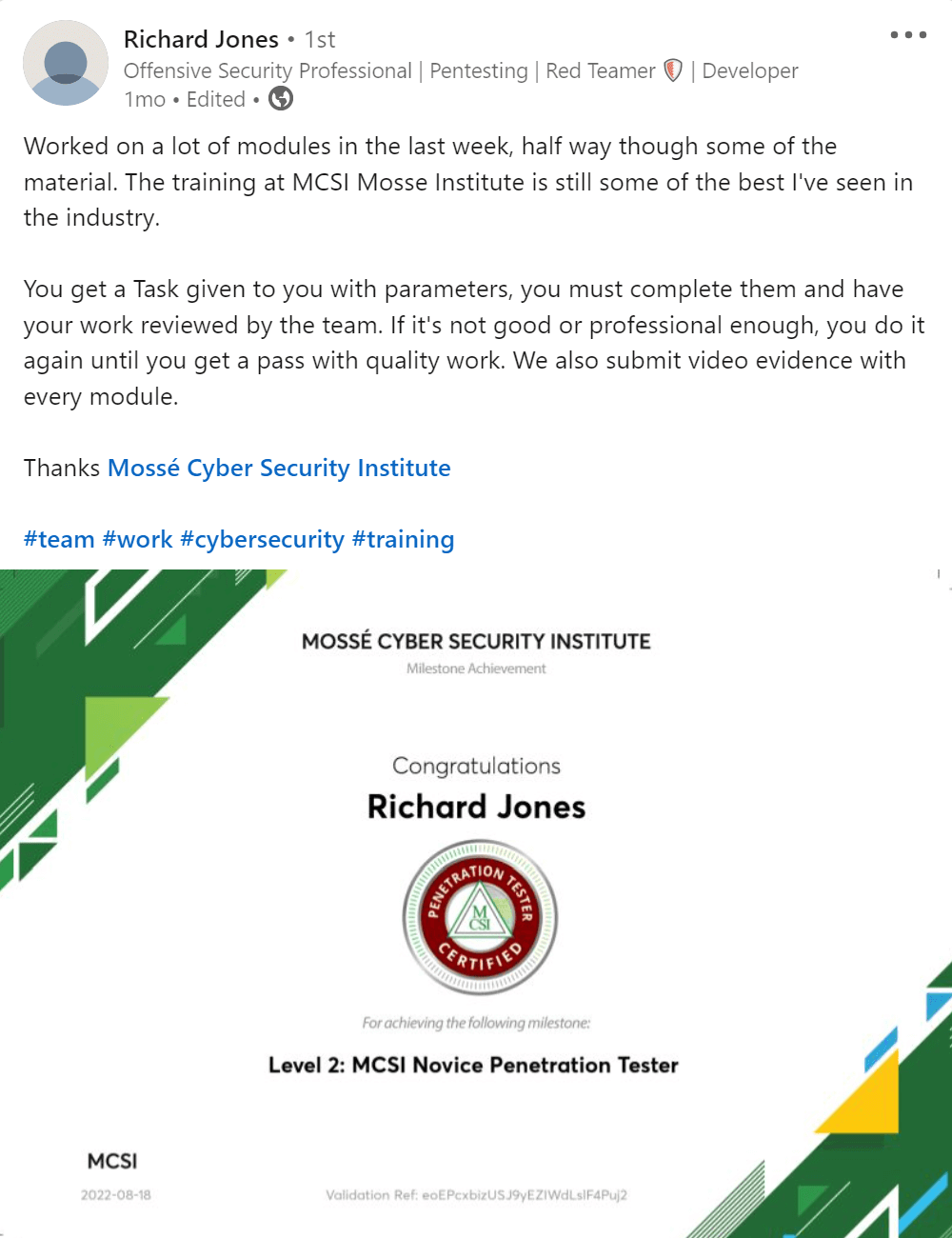
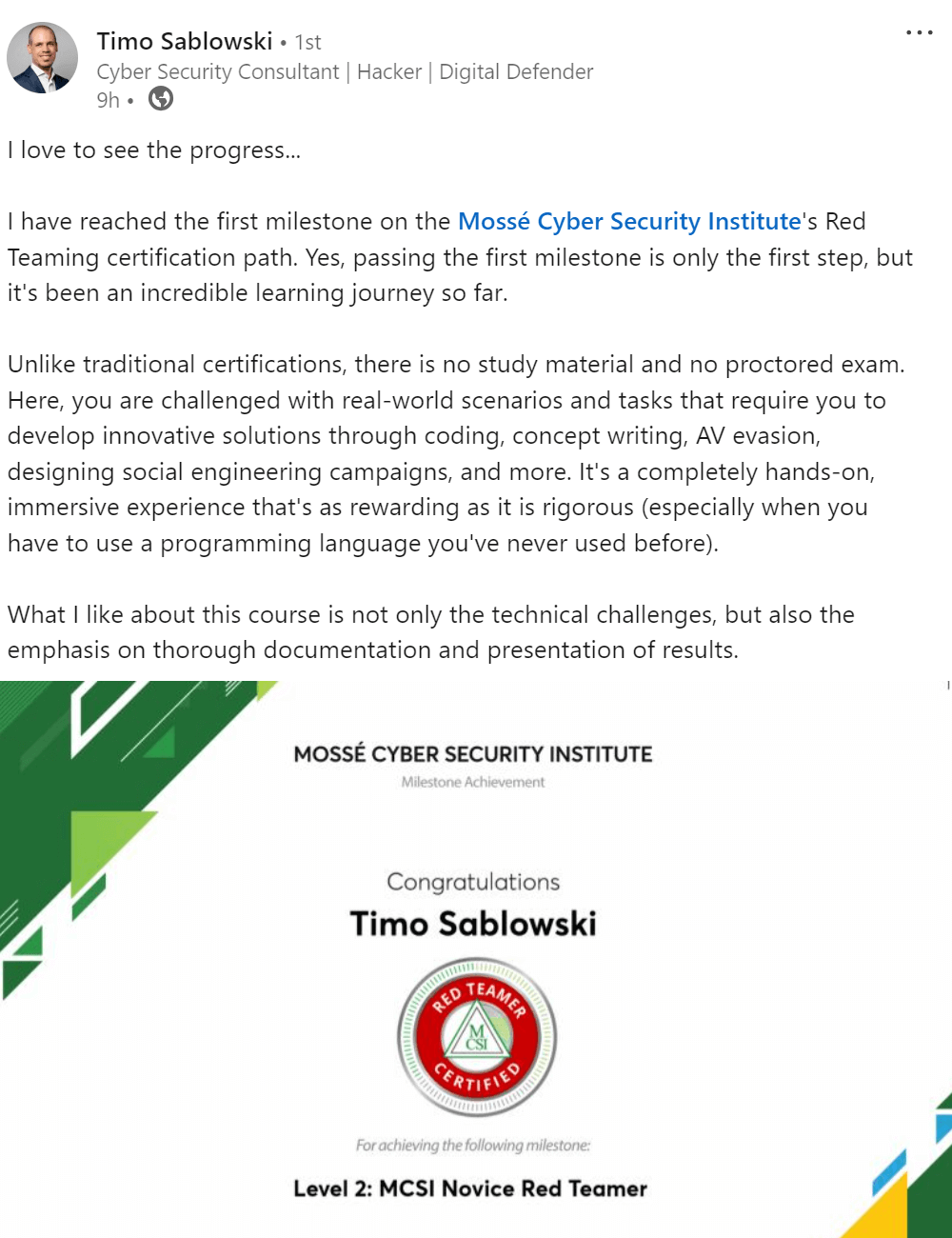
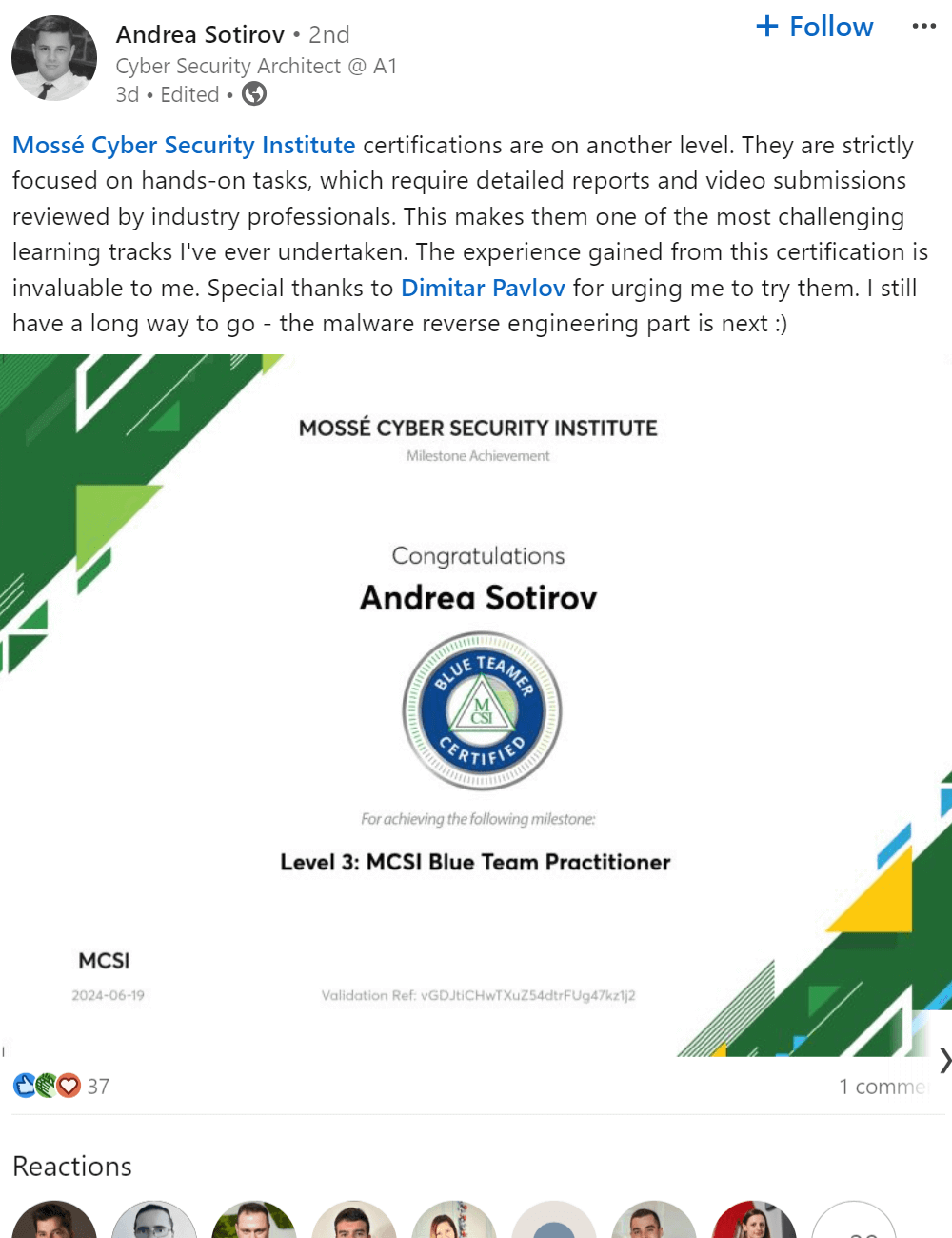
Assess the requirements and goals of the mission
The first step in designing a security testing plan is to assess the requirements and goals of the project. The requirements of the project will determine the scope of the security testing. The goals of the project will determine the focus of the security testing.
Once the requirements and goals have been assessed, the next step is to design a test plan. The test plan should include a risk assessment, which will identify potential vulnerabilities in the system. The test plan should also include a review of the security controls in place and how they will be tested.
Identify testing constraints
Identifying constraints is important in any security testing engagement, but is especially important in penetration tests. By understanding the environment and identifying any potential limitations, the pentester can better focus the assessment and deliver a more meaningful outcome.
Some common constraints include:
-
The scope of the test, which may be limited by time, budget, or other factors
-
The organization's security posture, which may affect what tests can be performed
-
The availability of systems and data, which may restrict the range of attacks that can be launched
-
The presence of security controls such as firewalls and intrusion detection systems, which may impede or complicate some attacks
By understanding these constraints and taking them into account, pentesters can tailor their tests to produce the most valuable results.
Establish a management assurance framework
When it comes to ensuring the security of your systems and data, having a strong management assurance framework in place is critical. This framework will help to ensure that security testing engagements are conducted in a consistent and effective manner, and that the resulting recommendations are properly implemented.
A management assurance framework should include clearly defined roles and responsibilities for all those involved in the security testing process, as well as documented procedures and guidelines. It should also include a reporting structure, so that everyone involved can track the progress of the testing and ensure that all stakeholders are kept up to date on the findings.
By establishing a management assurance framework, you can be sure that your security testing engagements are effectively managed and that the resulting recommendations are properly implemented, thus helping to protect your systems and data from potential security threats.
Use an effective testing methodology
Security testing engagements are extremely important, and using an effective testing methodology is critical to their success. By using an effective testing methodology, security professionals can ensure that they are covering all the necessary bases in their security assessments. This helps to reduce the risk of vulnerabilities going undetected, and ultimately helps to improve the security of the organization.
Use an effective testing methodology
There are many different ways to approach identifying and exploiting vulnerabilities in a security testing project. One common strategy is to first map the organization's assets and identify which systems and applications are most important to the business. From there, you can focus your efforts on identifying potential vulnerabilities in those systems and applications.
Once you have a list of potential vulnerabilities, you can start exploiting them to see if they are actually exploitable. This may involve using automated tools or manual techniques to attempt to take control of the system or gain access to sensitive data. It's important to be thorough in your testing, as even a single exploitable vulnerability can provide a foothold for an attacker.
Once you have identified and exploited all of the vulnerabilities in a system, it's important to document your findings and provide recommendations for how they can be fixed. This helps ensure that the system is secure and reduces the risk of a successful attack.
Report key findings
When it comes to security testing, it's important to report key findings to ensure that the project is on track and any potential security risks are addressed. Typically, a report will outline the methodology used in the testing process, as well as any major vulnerabilities that were discovered. This allows stakeholders to understand the implications of these vulnerabilities and take the necessary steps to mitigate any risks.
It's also important to keep in mind that not all vulnerabilities are created equal. Some may be more serious than others, and it's important to rank them accordingly. This helps stakeholders prioritize which vulnerabilities should be fixed first.
Finally, a good report will also include recommendations for how to address any vulnerabilities that were discovered. This can help ensure that the project stays on track and that any potential security risks are mitigated.
Extract lessons learnt
After a security testing project is complete, it's important to extract lessons learnt from the project so that the lessons can be applied to future projects.

 Intermediate
Intermediate