Networking fundamentals encompass foundational concepts and technologies critical for communication and data exchange in IT systems, serving as the backbone for modern interconnected infrastructure. Understanding these principles is crucial for designing, implementing, and maintaining reliable and secure networks to support various applications and services.
OSI Model (Open Systems Interconnection Model)
The OSI model is a conceptual framework used to understand and standardize the functions of a networking system. It consists of seven layers: Physical, Data Link, Network, Transport, Session, Presentation, and Application.
Data Encapsulation and Decapsulation
Data encapsulation involves adding header information to data as it moves down the OSI layers, while decapsulation removes these headers as data moves up the layers.
Maximum Transmission Unit (MTU)
MTU is the largest size of a data packet that can be transmitted over a network link without fragmentation.
Mesh Network Topology
Mesh topology is characterized by every node being connected to every other node, providing redundant paths for data transmission and high resilience.
Peer-to-Peer (P2P) Network
A P2P network allows devices to communicate directly with each other without the need for a centralized server.
Client-Server Network
In a client-server network, client devices request services or resources from centralized servers.
Network Address Translation (NAT)
NAT is a technique used to modify IP address information in packet headers while they are in transit across a routing device.
Port Address Translation (PAT)
PAT is a type of NAT that maps multiple private IP addresses to a single public IP address using different port numbers.
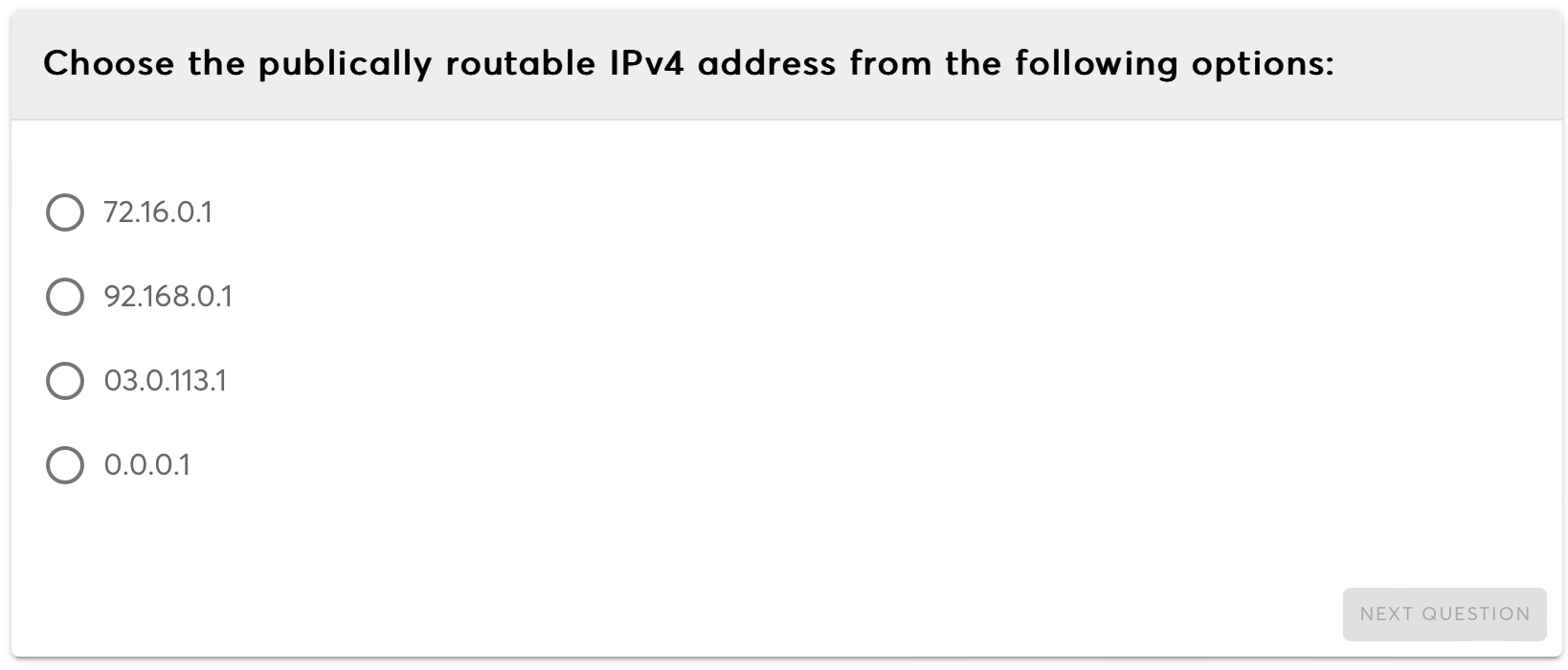
IP Class Types (IPv4)
IPv4 addresses are classified into five classes: A, B, C, D, and E, based on their leading bits and address ranges.
Classless Inter-Domain Routing (CIDR)
CIDR is a method for allocating IP addresses and IP routing, enabling more efficient use of IP address space and simpler route announcements.
Session Initiation Protocol (SIP)
SIP typically uses port 5060 for establishing, modifying, and terminating multimedia sessions such as voice and video calls over IP networks.
Transmission Control Protocol (TCP)
TCP is a connection-oriented protocol responsible for establishing reliable and error-checked data transmission between applications on hosts in a network.
User Datagram Protocol (UDP)
UDP is a connectionless protocol that provides low-latency, best-effort delivery of data without error checking or retransmission.
Internet Control Message Protocol (ICMP)
ICMP is a network protocol used to send error messages and operational information about IP networks, often used for diagnostic and troubleshooting purposes.
Start of Authority (SOA) DNS Record
The SOA record specifies the authoritative DNS server for a domain and contains important information about the zone, such as the primary name server, contact email address, and zone refresh interval.
Root DNS Server
A root DNS server is a name server that stores the complete database of domain names and their associated IP addresses for the root zone of the Domain Name System (DNS).
Infrastructure as a Service (IaaS)
IaaS is a cloud computing model that provides virtualized computing resources over the internet, including virtual machines, storage, and networking infrastructure.

 Beginner
Beginner