|
19
|
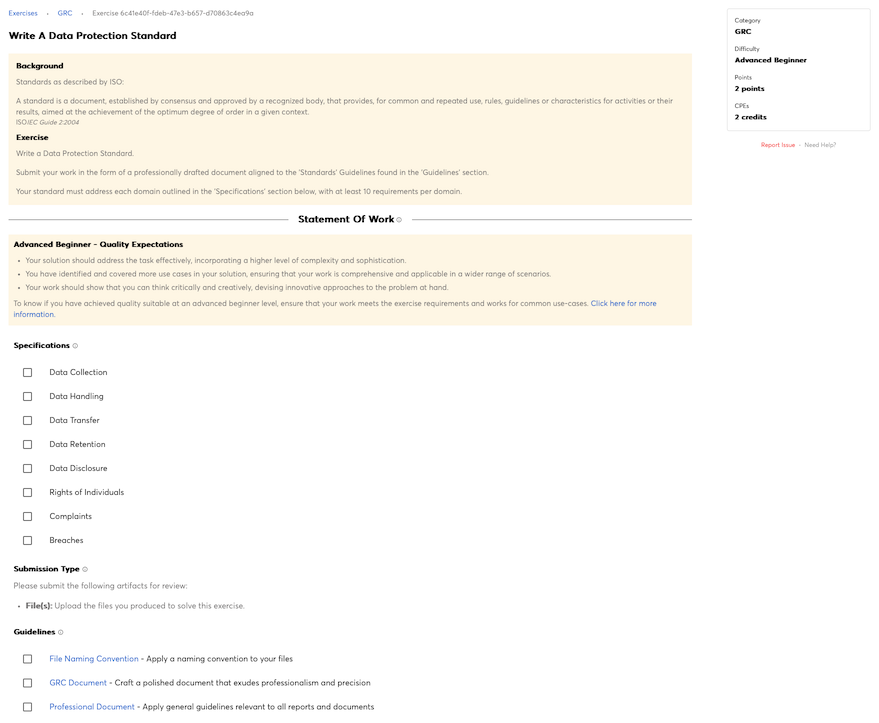
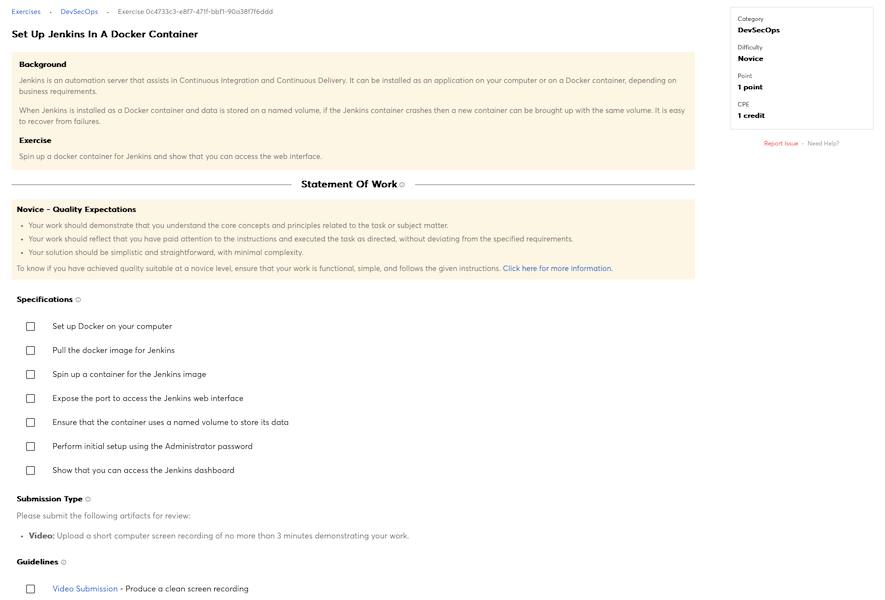
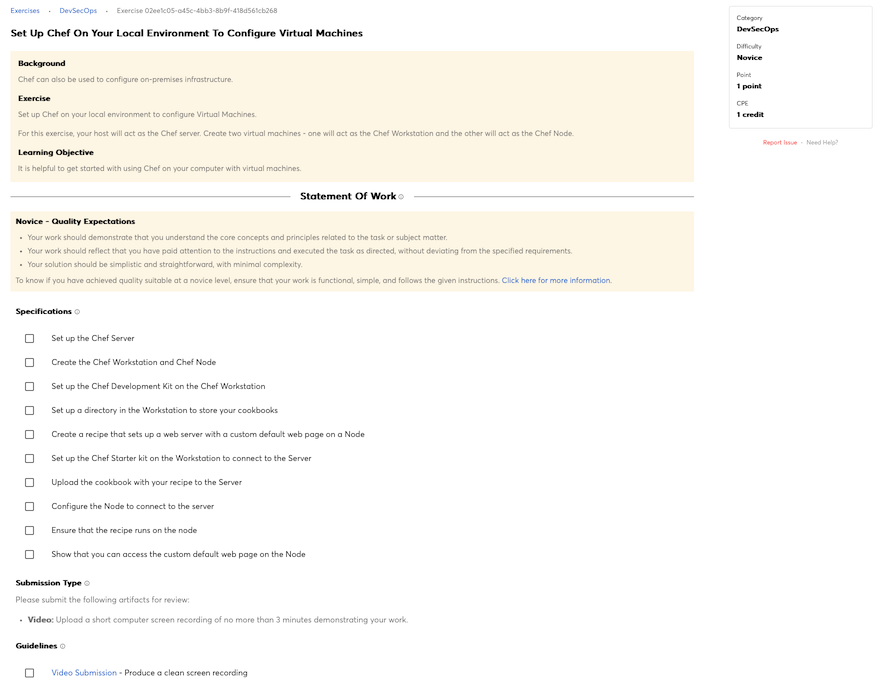
Knowledge of cyber defense and vulnerability assessment tools, including open source tools, and their capabilities.
|
|
22
|
Knowledge of computer networking concepts and protocols, and network security methodologies.
|
|
40
|
Knowledge of organization’s evaluation and validation requirements.
|
|
55
|
Knowledge of cybersecurity principles used to manage risks related to the use, processing, storage, and transmission of information or data.
|
|
58
|
Knowledge of known vulnerabilities from alerts, advisories, errata, and bulletins.
|
|
63
|
Knowledge of cybersecurity principles and organizational requirements (relevant to confidentiality, integrity, availability, authentication, non-repudiation).
|
|
70
|
Knowledge of information technology (IT) security principles and methods (e.g., firewalls, demilitarized zones, encryption).
|
|
77
|
Knowledge of current industry methods for evaluating, implementing, and disseminating information technology (IT) security assessment, monitoring, detection, and remediation tools and procedures utilizing standards-based concepts and capabilities.
|
|
105
|
Knowledge of system and application security threats and vulnerabilities (e.g., buffer overflow, mobile code, cross-site scripting, Procedural Language/Structured Query Language [PL/SQL] and injections, race conditions, covert channel, replay, return-oriented attacks, malicious code).
|
|
108
|
Knowledge of risk management processes (e.g., methods for assessing and mitigating risk).
|
|
1072
|
Knowledge of network security architecture concepts including topology, protocols, components, and principles (e.g., application of defense-in-depth).
|
|
1158
|
Knowledge of cybersecurity principles.
|
|
1159
|
Knowledge of cyber threats and vulnerabilities.
|
|
6900
|
Knowledge of specific operational impacts of cybersecurity lapses.
|
|
6935
|
Knowledge of cloud computing service models Software as a Service (SaaS), Infrastructure as a Service (IaaS), and Platform as a Service (PaaS).
|
|
6938
|
Knowledge of cloud computing deployment models in private, public, and hybrid environment and the difference between on-premises and off-premises environments.
|
|
27
|
Knowledge of cryptography and cryptographic key management concepts.
|
|
38
|
Knowledge of organization’s enterprise information security architecture system.
|
|
43A
|
Knowledge of embedded systems.
|
|
53A
|
Knowledge of security risk assessments and authorization per Risk Management Framework processes.
|
|
69A
|
Knowledge of risk management processes and requirements per the Risk Management Framework (RMF).
|
|
88
|
Knowledge of new and emerging information technology (IT) and cybersecurity technologies.
|
|
88A
|
Knowledge of current and emerging cyber technologies.
|
|
95B
|
Knowledge of penetration testing principles, tools, and techniques, including specialized tools for non-traditional systems and networks (e.g., control systems).
|
|
121
|
Knowledge of structured analysis principles and methods.
|
|
128
|
Knowledge of systems diagnostic tools and fault identification techniques.
|
|
143
|
Knowledge of the organization’s enterprise information technology (IT) goals and objectives.
|
|
942
|
Knowledge of the organization’s core business/mission processes.
|
|
1034A
|
Knowledge of Personally Identifiable Information (PII) data security standards.
|
|
1034B
|
Knowledge of Payment Card Industry (PCI) data security standards.
|
|
1034C
|
Knowledge of Personal Health Information (PHI) data security standards.
|
|
1036
|
Knowledge of applicable laws (e.g., Electronic Communications Privacy Act, Foreign Intelligence Surveillance Act, Protect America Act, search and seizure laws, civil liberties and privacy laws), statutes (e.g., in Titles 10, 18, 32, 50 in U.S. Code), Presidential Directives, executive branch guidelines, and/or administrative/criminal legal guidelines and procedures relevant to work performed.
|
|
1037
|
Knowledge of information technology (IT) supply chain security and risk management policies, requirements, and procedures.
|
|
1038B
|
Knowledge of local specialized system requirements (e.g., critical infrastructure/control systems that may not use standard information technology [IT]) for safety, performance, and reliability).
|
|
1131
|
Knowledge of security architecture concepts and enterprise architecture reference models (e.g., Zackman, Federal Enterprise Architecture [FEA]).
|
|
1141A
|
Knowledge of an organization’s information classification program and procedures for information compromise.
|
|
1142
|
Knowledge of security models (e.g., Bell-LaPadula model, Biba integrity model, Clark-Wilson integrity model).
|

 Intermediate
Intermediate