|
22
|
Knowledge of computer networking concepts and protocols, and network security methodologies.
|
|
24A
|
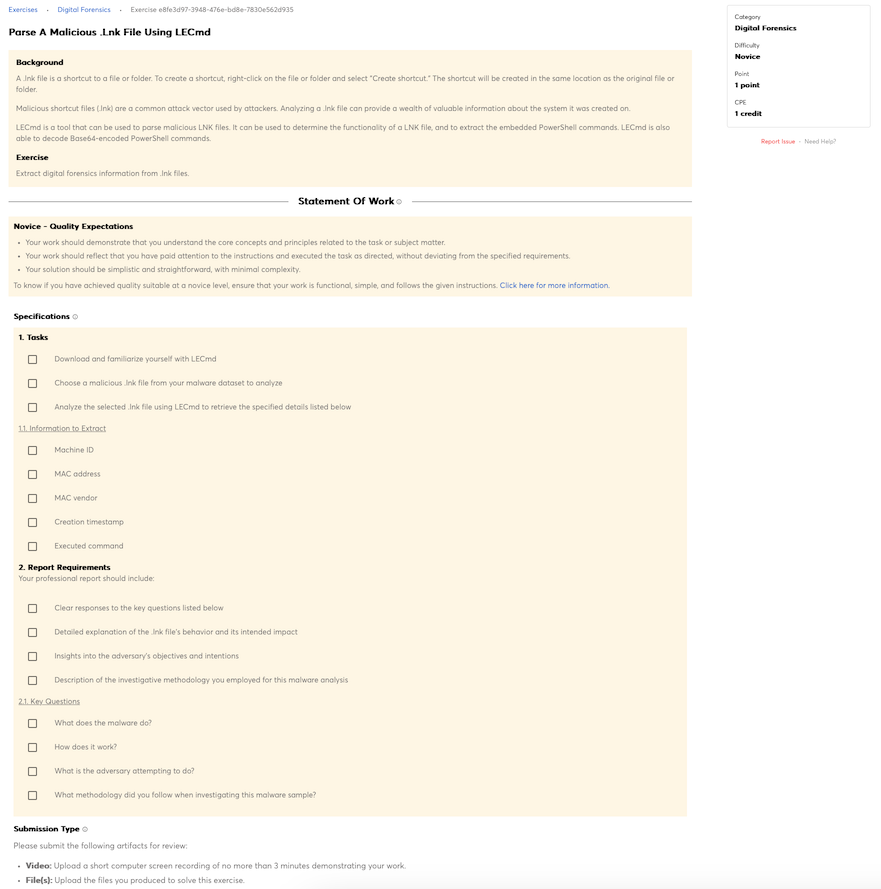
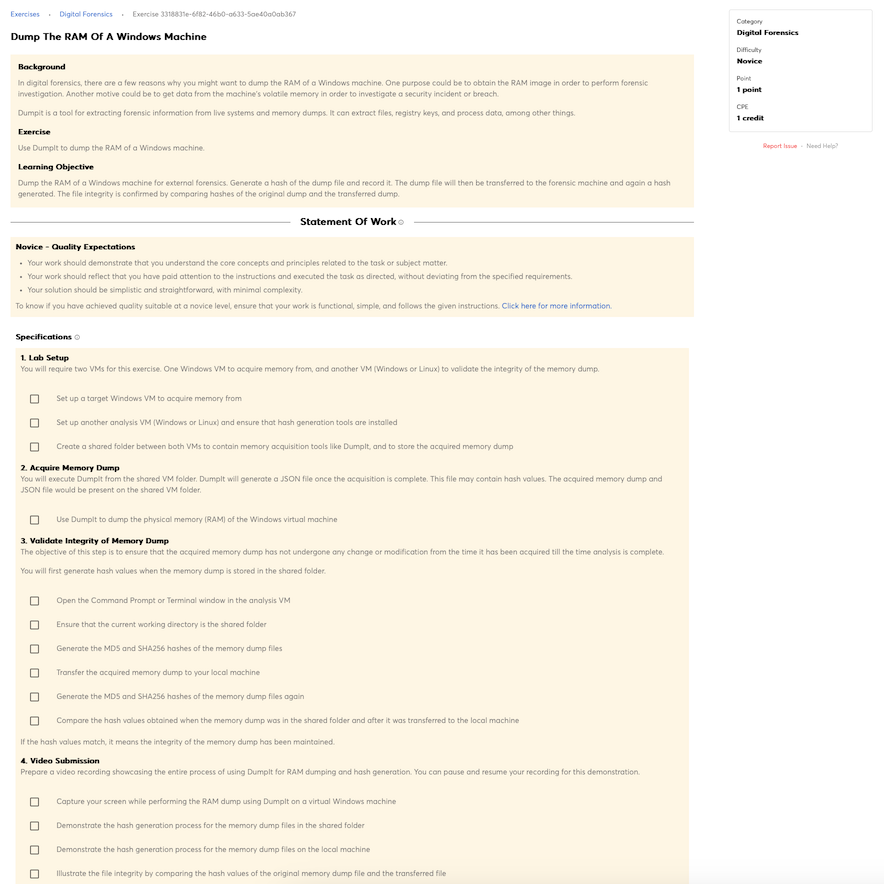
Knowledge of basic concepts and practices of processing digital forensic data.
|
|
108
|
Knowledge of risk management processes (e.g., methods for assessing and mitigating risk).
|
|
302
|
Knowledge of investigative implications of hardware, Operating Systems, and network technologies.
|
|
1086
|
Knowledge of data carving tools and techniques (e.g., Foremost).
|
|
1089
|
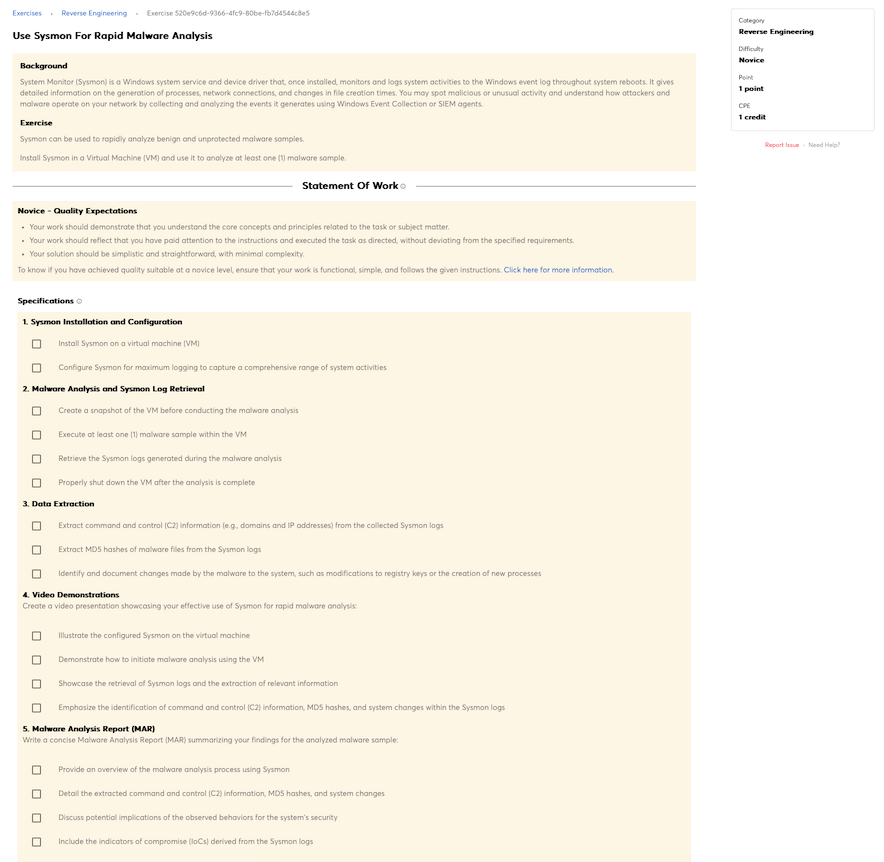
Knowledge of reverse engineering concepts.
|
|
1092
|
Knowledge of anti-forensics tactics, techniques, and procedures.
|
|
1096
|
Knowledge of malware analysis tools (e.g., Oily Debug, Ida Pro).
|
|
1158
|
Knowledge of cybersecurity principles.
|
|
1159
|
Knowledge of cyber threats and vulnerabilities.
|
|
6810
|
Knowledge of binary analysis.
|
|
6900
|
Knowledge of specific operational impacts of cybersecurity lapses.
|
|
6935
|
Knowledge of cloud computing service models Software as a Service (SaaS), Infrastructure as a Service (IaaS), and Platform as a Service (PaaS).
|
|
6938
|
Knowledge of cloud computing deployment models in private, public, and hybrid environment and the difference between on-premises and off-premises environments.
|
|
25
|
Knowledge of encryption algorithms (e.g., Internet Protocol Security [IPSEC], Advanced Encryption Standard [AES], Generic Routing Encapsulation [GRE], Internet Key Exchange [IKE], Message Digest Algorithm [MD5], Secure Hash Algorithm [SHA], Triple Data Encryption Standard [3DES]).
|
|
29
|
Knowledge of data backup, types of backups (e.g., full, incremental), and recovery concepts and tools.
|
|
61
|
Knowledge of incident response and handling methodologies.
|
|
90
|
Knowledge of operating systems.
|
|
105
|
Knowledge of system and application security threats and vulnerabilities (e.g., buffer overflow, mobile code, cross-site scripting, Procedural Language/Structured Query Language [PL/SQL] and injections, race conditions, covert channel, replay, return-oriented attacks, malicious code).
|
|
113
|
Knowledge of server and client operating systems.
|
|
114
|
Knowledge of server diagnostic tools and fault identification techniques.
|
|
139
|
Knowledge of the common networking protocols (e.g., TCP/IP), services (e.g., web, mail, Domain Name Server), and how they interact to provide network communications.
|
|
264
|
Knowledge of basic physical computer components and architectures, including the functions of various components and peripherals (e.g., CPUs, Network Interface Cards, data storage).
|
|
287
|
Knowledge of file system implementations (e.g., New Technology File System [NTFS], File Allocation Table [FAT], File Extension [EXT]).
|
|
290
|
Knowledge of processes for seizing and preserving digital evidence (e.g., chain of custody).
|
|
294
|
Knowledge of hacking methodologies in Windows or Unix/Linux environment.
|
|
310
|
Knowledge of legal governance related to admissibility (e.g., Federal Rules of Evidence).
|
|
316
|
Knowledge of processes for collecting, packaging, transporting, and storing electronic evidence to avoid alteration, loss, physical damage, or destruction of data.
|
|
340
|
Knowledge of types and collection of persistent data.
|
|
345
|
Knowledge of web mail collection, searching/analyzing techniques, tools, and cookies.
|
|
346
|
Knowledge of which system files (e.g., log files, registry files, configuration files) contain relevant information and where to find those system files.
|
|
888
|
Knowledge of types of digital forensics data and how to recognize them.
|
|
889
|
Knowledge of deployable forensics.
|
|
923
|
Knowledge of security event correlation tools.
|
|
1033
|
Knowledge of basic system administration, network, and operating system hardening techniques.
|
|
1036
|
Knowledge of applicable laws (e.g., Electronic Communications Privacy Act, Foreign Intelligence Surveillance Act, Protect America Act, search and seizure laws, civil liberties and privacy laws), statutes (e.g., in Titles 10, 18, 32, 50 in U.S. Code), Presidential Directives, executive branch guidelines, and/or administrative/criminal legal guidelines and procedures relevant to work performed.
|
|
1072
|
Knowledge of network security architecture concepts including topology, protocols, components, and principles (e.g., application of defense-in-depth).
|
|
1093
|
Knowledge of common forensics tool configuration and support applications (e.g., VMWare, WIRESHARK).
|
|
1094
|
Knowledge of debugging procedures and tools.
|
|
1095
|
Knowledge of how different file types can be used for anomalous behavior.
|
|
1097
|
Knowledge of virtual machine aware malware, debugger aware malware, and packing.
|
|
3513
|
Knowledge of system administration concepts for Unix/Linux and/or Windows operating systems.
|
|
6210
|
Knowledge of cloud service models and possible limitations for an incident response.
|
|
6820
|
Knowledge of network architecture concepts including topology, protocols, and components.
|

 Advanced
Advanced