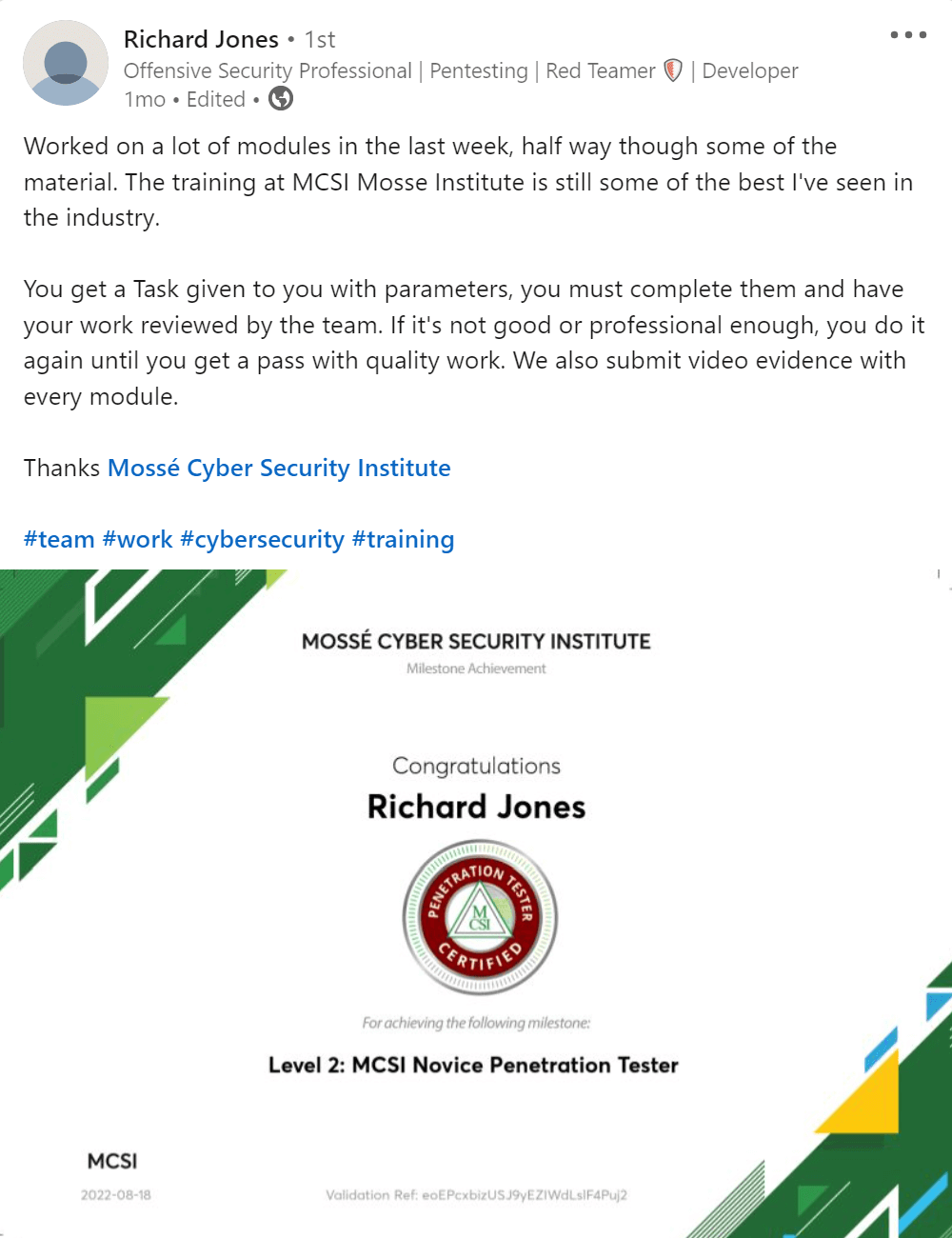
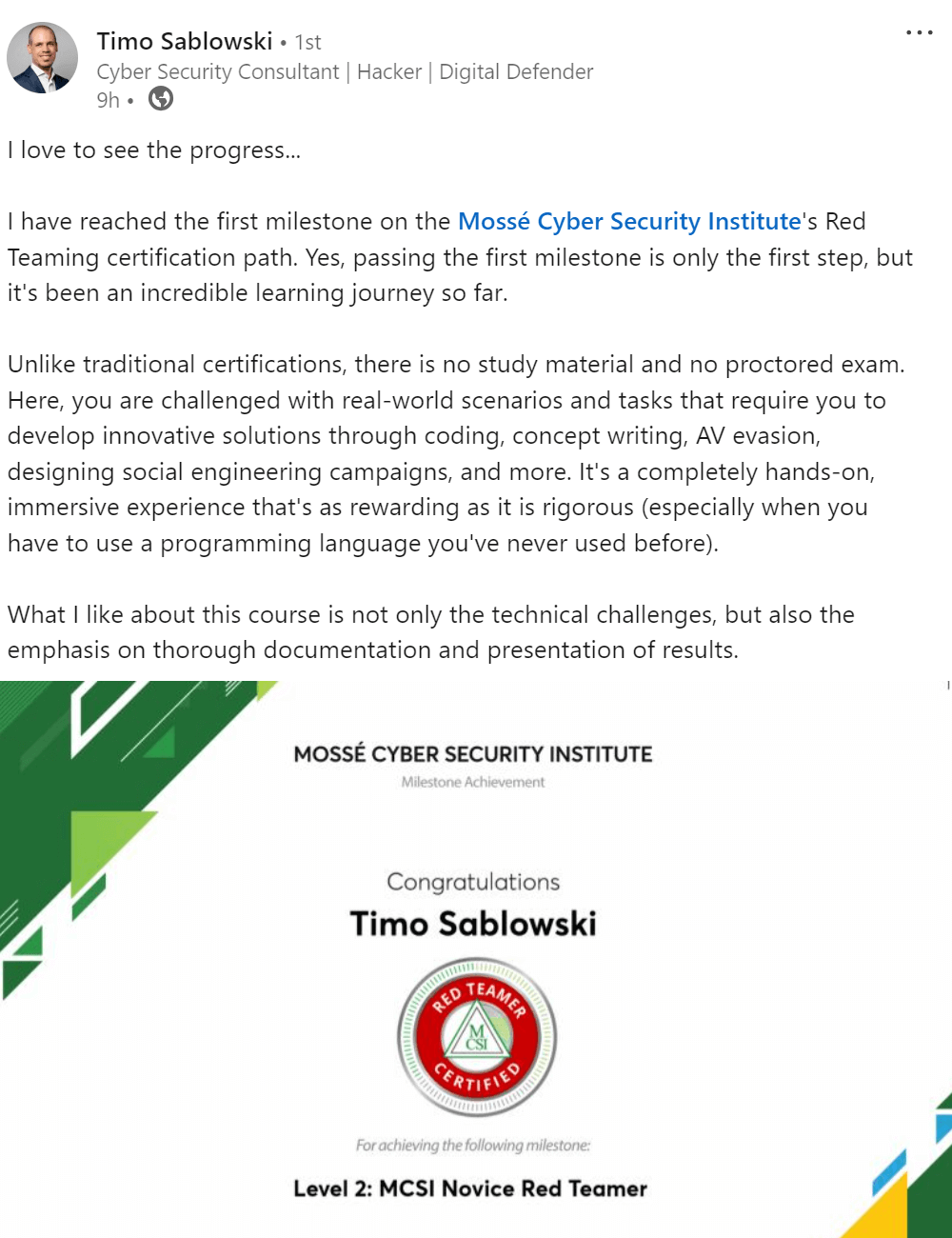
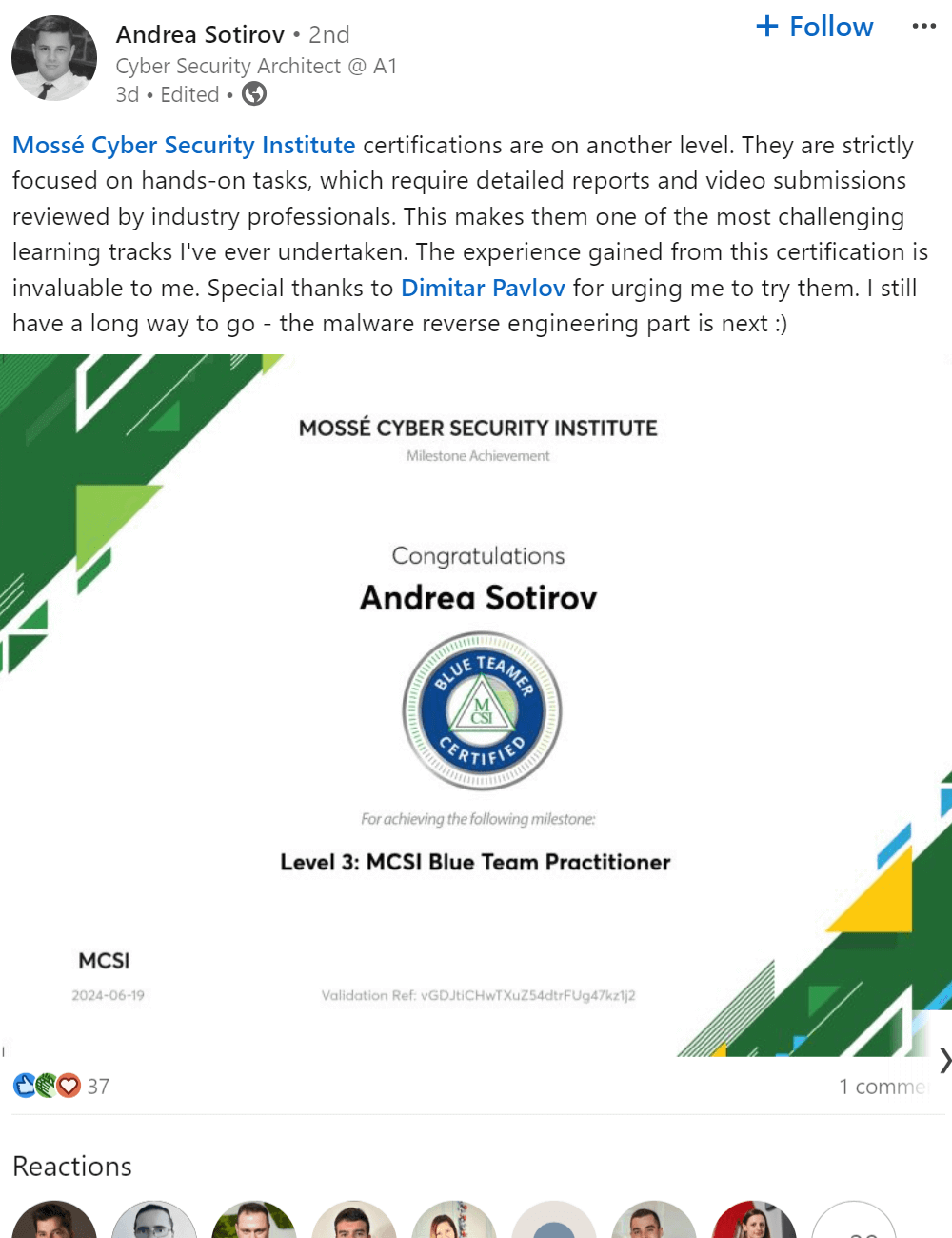
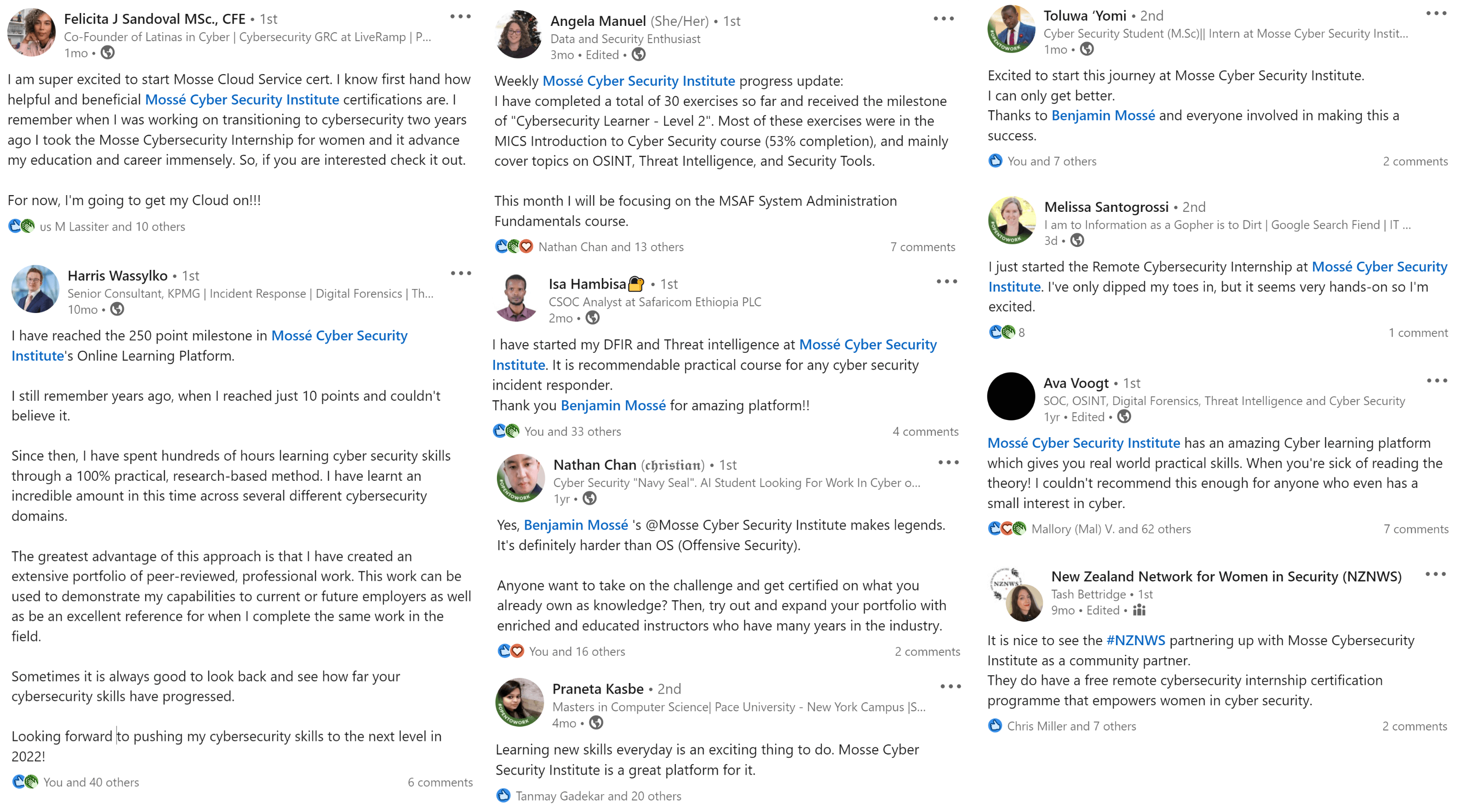
Executive Summary
An executive summary is a high-level overview of a document that synthesizes the key points. It is typically used to give decision-makers a quick, executive-level understanding of complex topics. The executive summary should be clear, concise, and free of jargon. It should also contain enough detail to give the reader a good understanding of the document's contents.
Tags and Keywords
malware can have many different tags and keywords depending on its purpose. Some common tags and keywords for malware include: viruses, worms, Trojan horses, spyware, adware, and ransomware. Identifying and extracting these keywords and tags will help you summarize what the report is about.
Sensitivity Classification
The Traffic Light Protocol is a color-coding system used to indicate the sensitivity of information contained within a document. The colors represent different levels of classification, with red being the most sensitive, followed by amber, green, and white. The system is designed to help recipients of a document quickly identify the level of sensitivity of the information contained within.
When conducting malware analysis, it is often necessary to share findings with other members of the security team. The Traffic Light Protocol can be used to classify the sensitivity of information contained in a report, making it easier for recipients to identify the level of risk associated with the malware.
Hashes
A common technique used to detect and analyze malware is to hash the contents of the sample and compare the result to a known database of hashes. This technique is effective because it is quick and does not require any prior knowledge of the sample. The most common algorithms used for hashing are MD5 and SHA-256.
Methodology
A malware analysis methodology is a process for reverse engineering malware to determine its functionality, capabilities, and purpose. The goal of malware analysis is to understand what the malware does, how it works, and how it can be detected and removed. The first step in malware analysis is to identify the type of malware and its capabilities. This can be done by looking at the code, researching the malware online, or running it in a controlled environment. Once the malware has been identified, the next step is to determine its purpose. This can be done by looking at the code, observing its behavior, or analyzing how it interacts with other systems.
Limitations
There are a number of limitations to malware analysis. Firstly, it can be time consuming and resource intensive. Secondly, there is a lack of standardization in tools and techniques, which can make it difficult to compare results across different analysts. Thirdly, malware can be designed to evade detection by malware analysis techniques, making it difficult to obtain accurate results. Finally, the dynamic nature of malware means that it can be difficult to obtain repeatable results.
Identification and Classification of Sample(s)
Information regarding the malware. For example, filename, file size, file type and format, first detection in the wild, and attributed threat actor.
Features
Different malware can have different features. For example, some malware is designed to steal information, while other malware is designed to disable systems. These features can then be graded by confidence level.
Dependencies
Malware dependencies are what make a given piece of malware effective. Without the proper dependencies, a piece of malware may not be able to function properly or may not be able to infect a system. Malware dependencies can include things such as specific operating system versions, specific hardware, or even specific applications. In some cases, a piece of malware may have dependencies on multiple items in order to function properly. In other cases, a piece of malware may only have a few dependencies. Properly analyzing a piece of malware's dependencies is important in order to determine how effective it may be.
Conclusions of Code Analysis and Observed Behavior
Conclusions of code analysis can include an understanding of the functionality of the malware, how it works, and what it is designed to do. Additionally, code analysis can reveal the level of sophistication of the malware and who might have created it. Observations of behavior can also provide information on what the malware does, how it works, and what it is designed to do.

 Intermediate
Intermediate