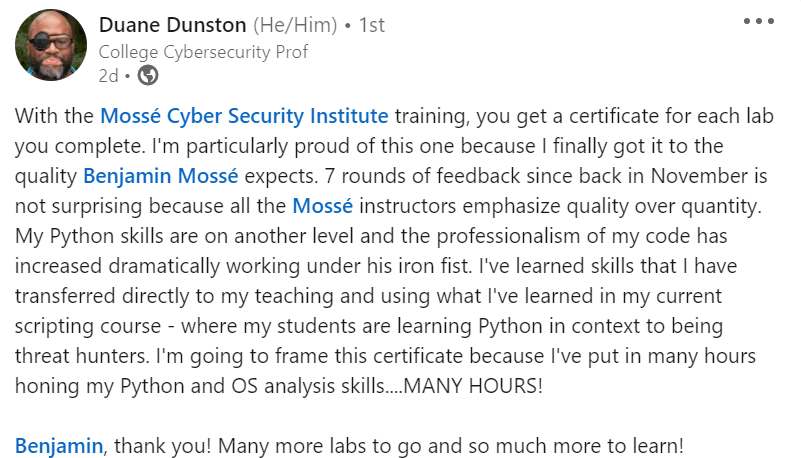
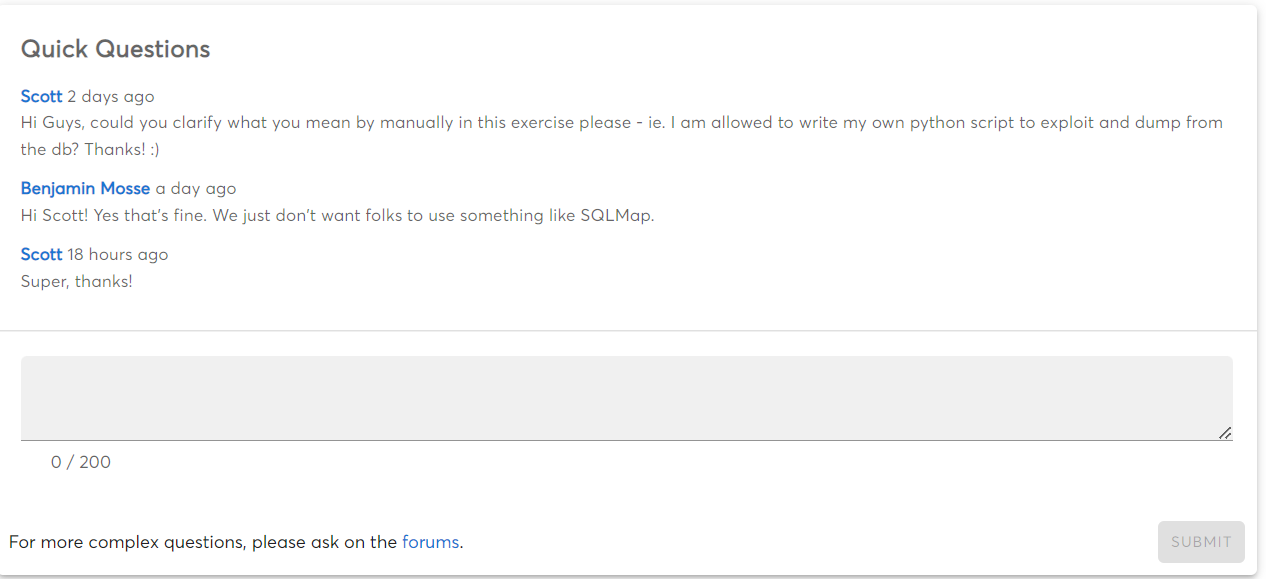
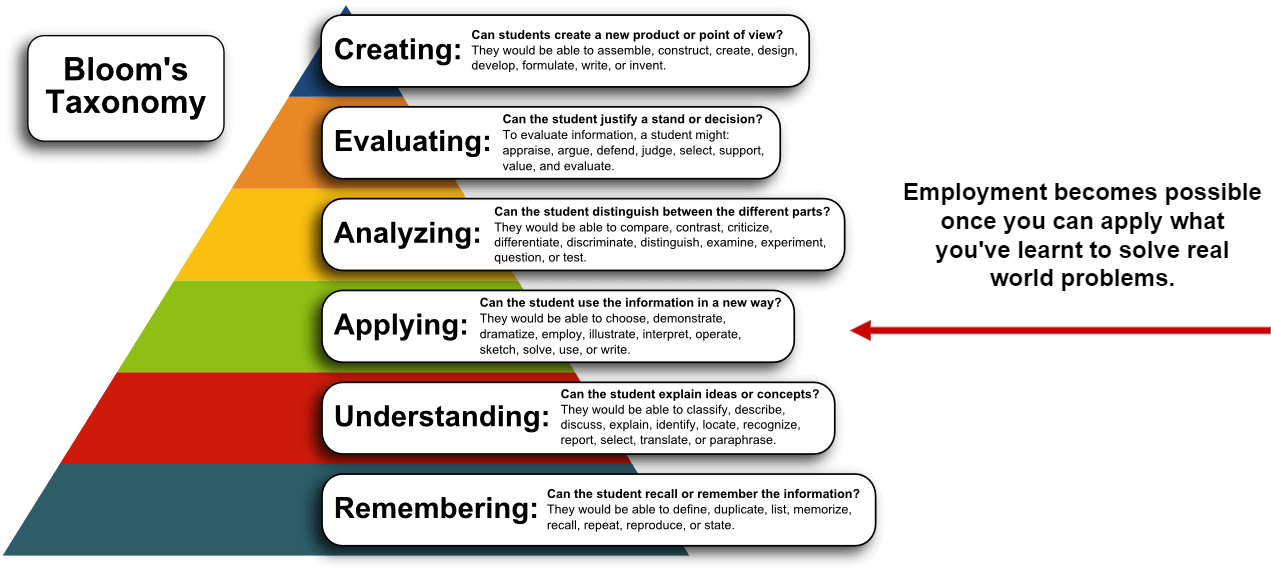
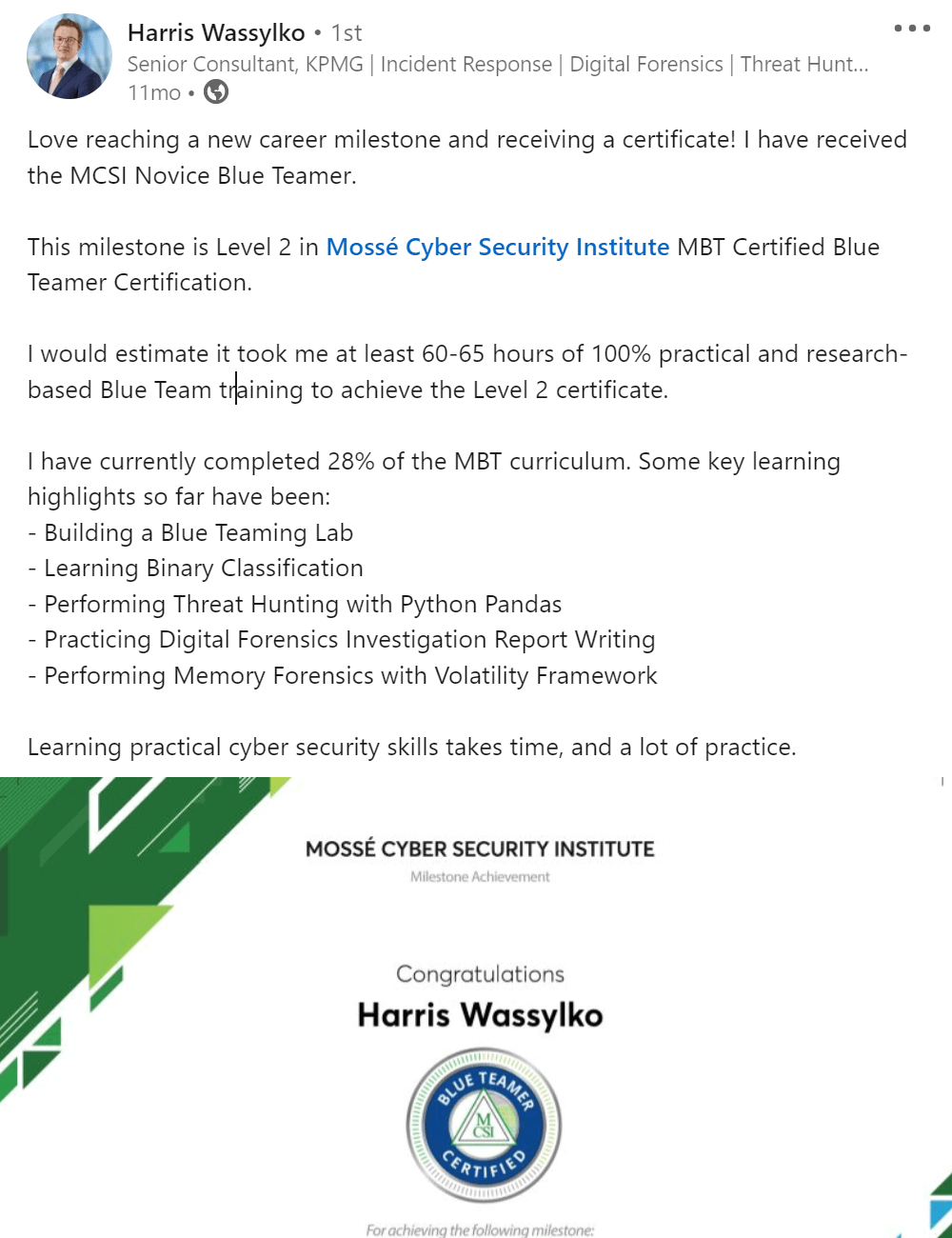
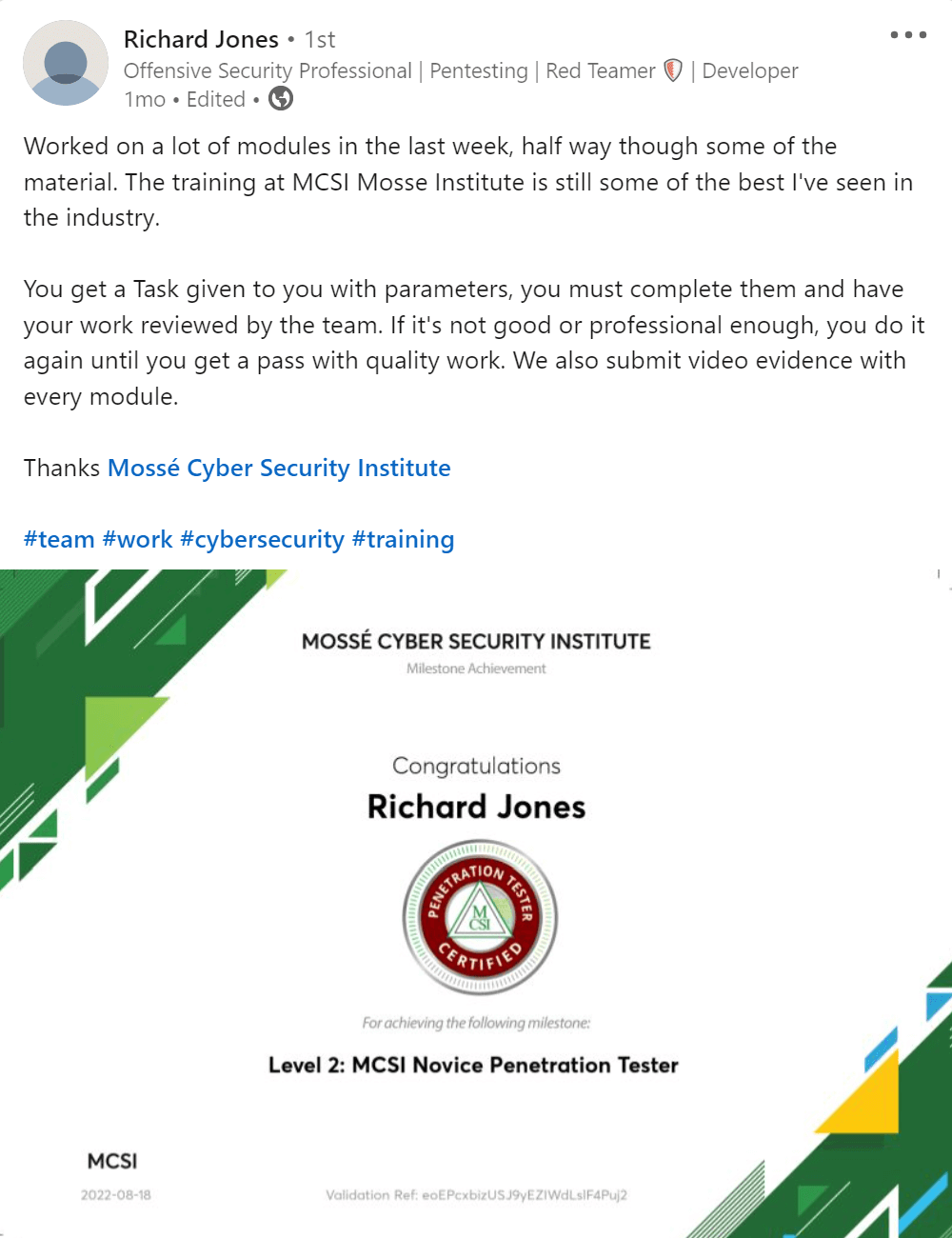
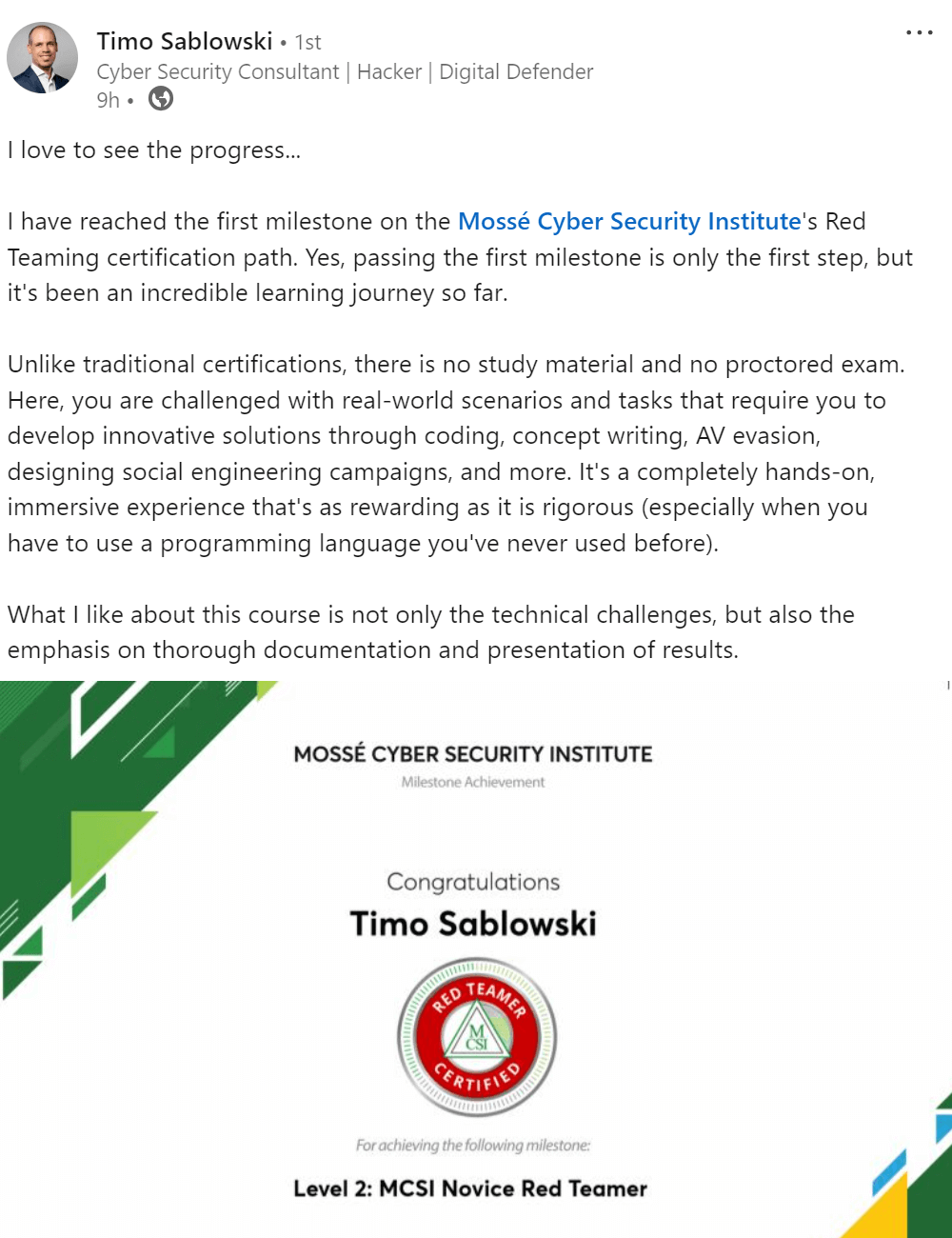
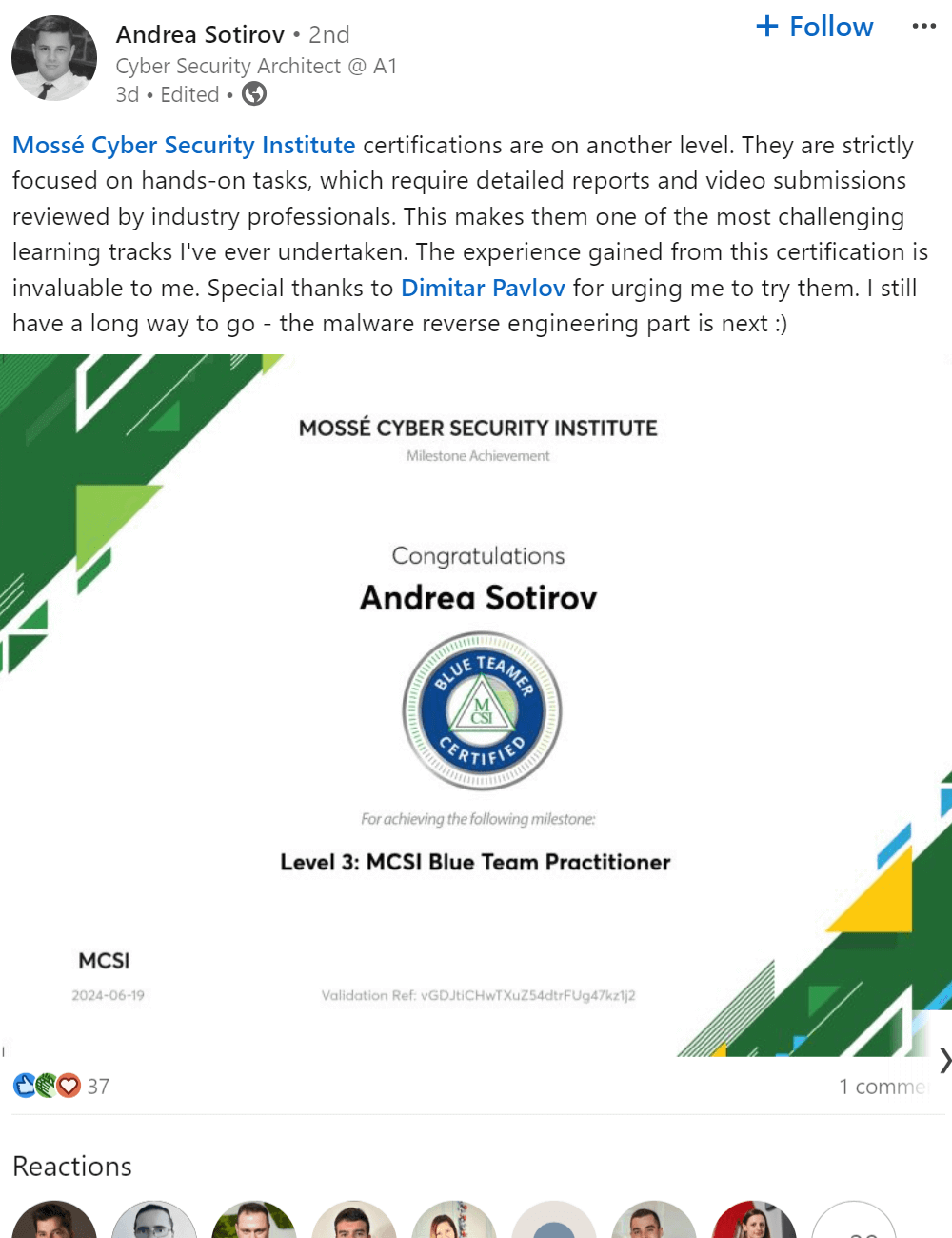
The MCSE certification teaches how to Configure and manage cloud accounts securely. One of the main goals of the certification is to ensure that cloud accounts are properly secured. This is done by teaching students how to create and manage passwords, configure security settings, and more. By completing the MCSE certification, students will be able to protect their cloud accounts from unauthorized access and ensure that their data is safe and secure.
Account Security
Cloud security is a critical factor to consider when moving to the cloud. One important aspect of cloud security is account security. Protecting your account is essential to protecting your data and preventing unauthorized access.
Identity and Access Management
Identity and Access Management, or IAM for short, is a critical element of cloud security. IAM is the practice of managing user identities and the access permissions associated with them. When properly implemented, IAM can help organizations securely access and use cloud resources while minimizing the risk of unauthorized access.
One of the main benefits of IAM is that it enables organizations to control who has access to which resources. This helps to prevent accidental or unauthorized access to sensitive data, applications, and other cloud resources.
Network and Instance Security
Network security is one of the most important aspects of using the cloud. You need to make sure that your data is protected while it is in transit between your devices and the cloud. You also need to ensure that your data is safe while it is stored in the cloud.
Instance security is another important consideration when using the cloud. You need to make sure that your instances are secure, and that only authorized users can access them.
Encryption and Storage Security
Data encryption and storage security are key concerns for many organizations when it comes to moving to the cloud. It's important to ensure that your data is encrypted before it's stored in the cloud and that the cloud provider has taken appropriate steps to secure the storage infrastructure. Many providers offer encryption services, but it's important to verify that the service is implemented correctly and that the provider holds to a high standard of security.
Micro-Segmentation
Micro-segmentation is a process of dividing a data center or cloud infrastructure into multiple, smaller compartments. This can be done manually, or through the use of software-defined networking (SDN) technologies. Micro-segmentation can help to improve security by isolating systems and applications from one another, making it more difficult for attackers to move laterally and compromise multiple systems. It can also help to improve performance and efficiency by routing traffic only where it is needed.
Virtualisation and Containers
Virtualisation and Containers are technologies that allow for the abstraction of computing resources. Virtualisation is the creation of a virtual machine that runs on a physical server. A container is a lightweight virtual machine that shares the kernel of the host operating system. Containers are created by packaging an application with its dependencies into a single unit.
Virtualisation and containers offer a number of benefits for cloud security. Virtual machines can be isolated from one another, limiting the damage that can be done if one is compromised. Containers can also be shielded from one another, and can be spun up and down quickly, making them more resilient to attack.
Both virtualisation and containers can be monitored and patched more easily than physical servers, making them more secure. Additionally, virtualisation and containers can be used to create separate virtual networks, which can help to isolate different parts of the organisation from one another.

 Intermediate
Intermediate