Course Overview
"Don't just find bugs, exploit them too!"
As technology advances, so do the methods used by hackers to exploit vulnerabilities. Web applications are increasingly complex, making them more difficult to secure. Penetration testers must therefore keep up with the latest trends in web exploitation in order to identify security weaknesses before attackers do.
Web exploitation requires a different skillset than other types of penetration testing. In addition to traditional hacking techniques, web testers must also be familiar with web application design and development in order to understand how vulnerabilities can be exploited. By learning web exploitation, penetration testers can provide their clients with a more comprehensive assessment of their security posture.
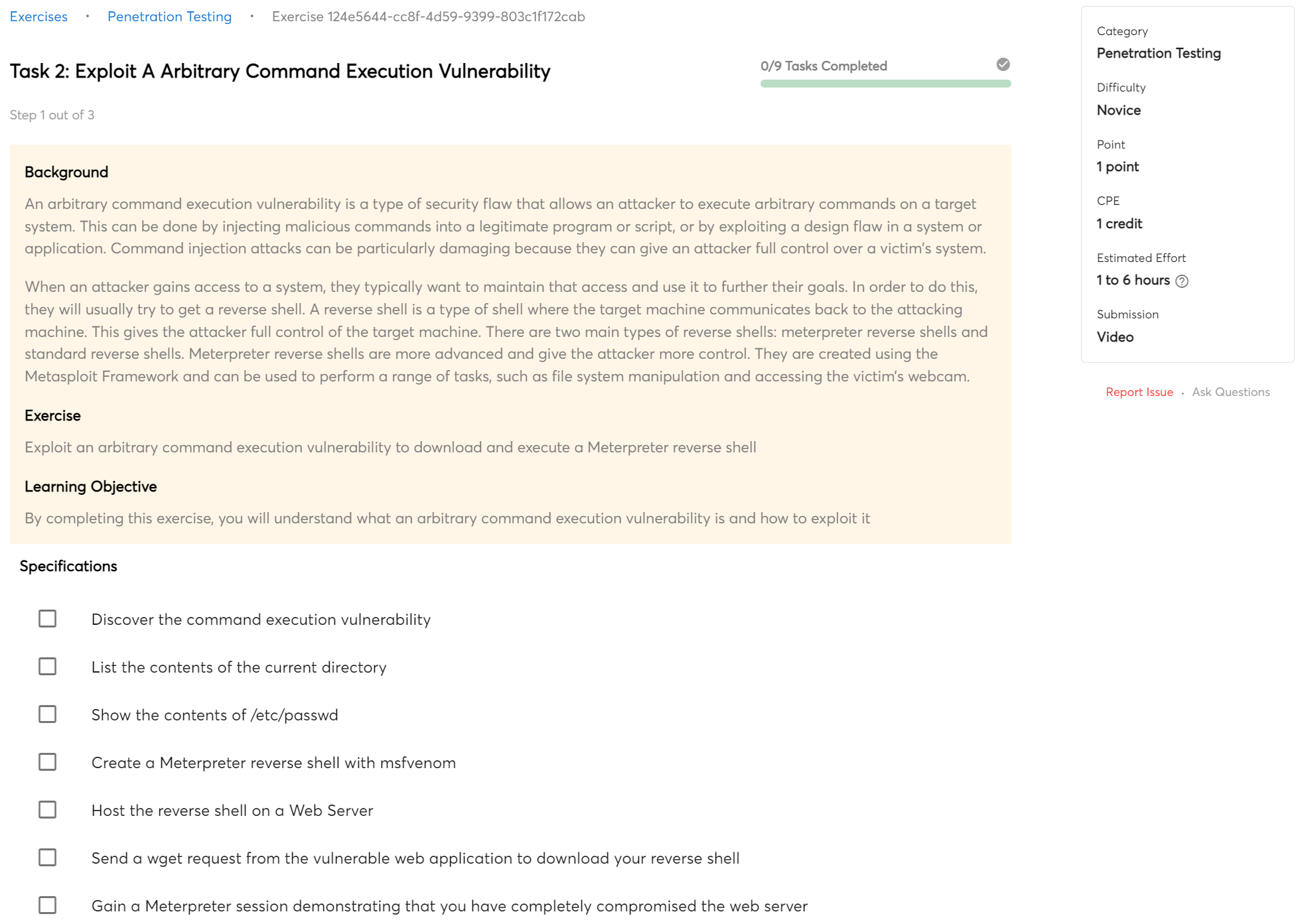
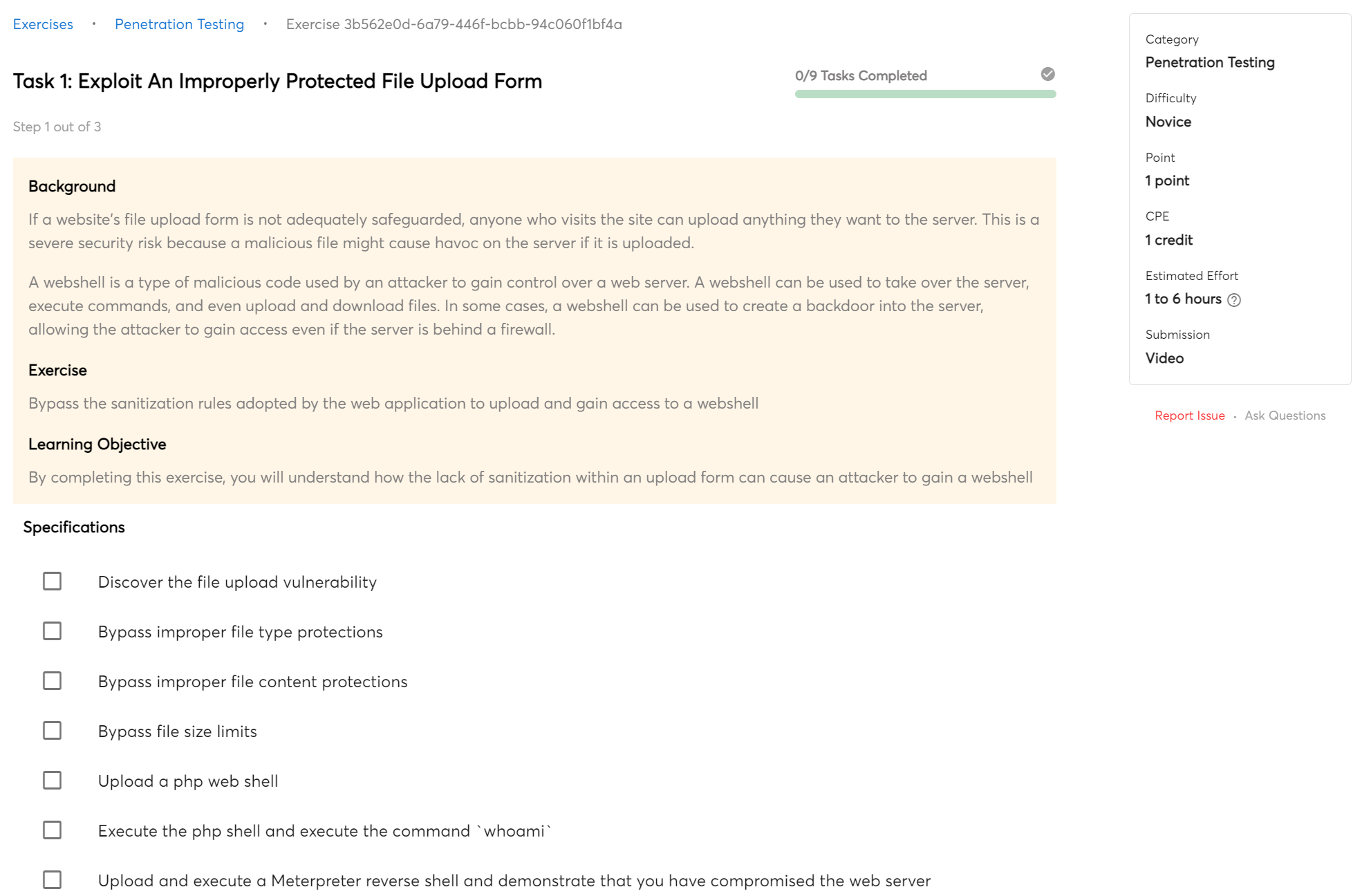
Command Execution
In web exploitation, command execution is the process of running a command on a remote server. This is usually done by injecting a malicious code into a web page or application. The code is then executed by the server and can allow the attacker to gain access to the system or take control of it.
You will master fundamental command execution techniques that will allow you to breach web servers by finishing this bootcamp.
This bootcamp will teach you how to find and exploit typical e-commerce platform business logic flaws. This experience will aid in the development of a mindset for finding similar issues in other types of software.
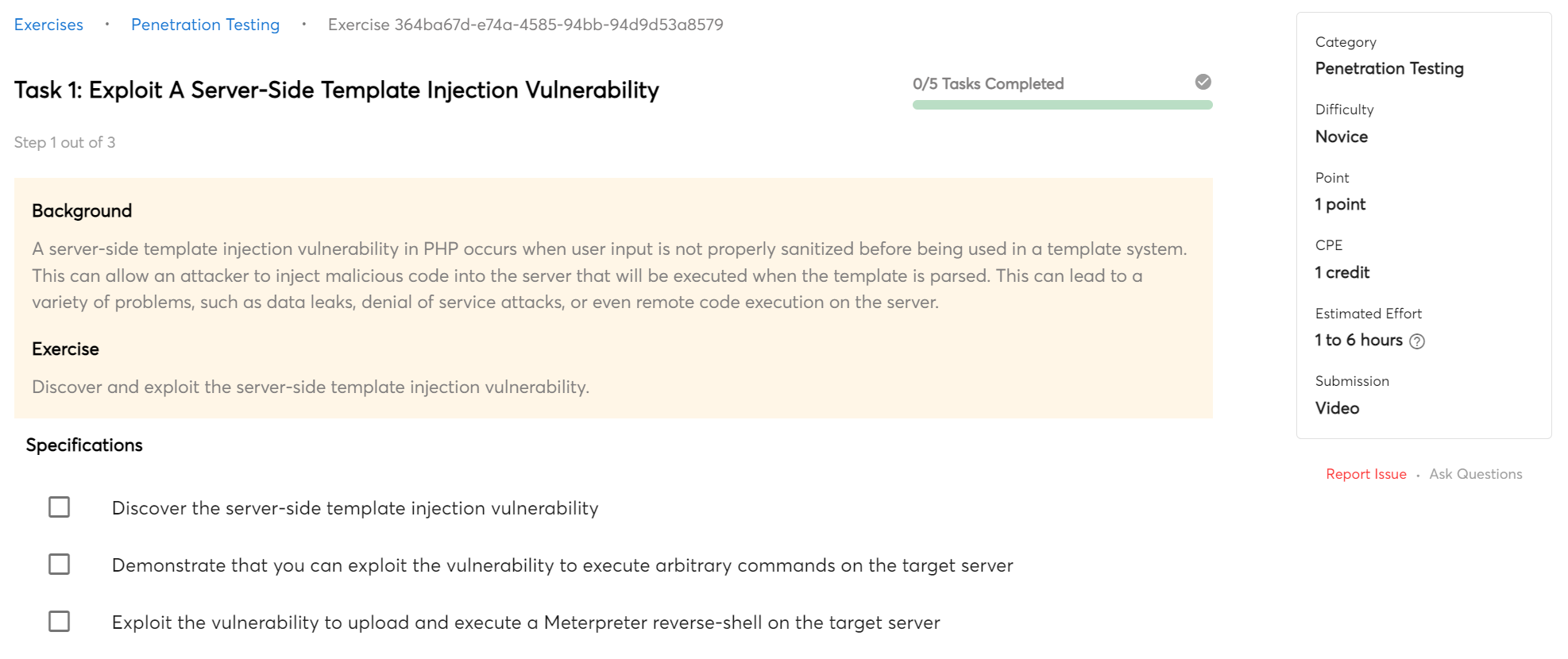
Code Injection
Code injection is a type of attack where the attacker inserts malicious code into a web application. The code is then executed by the web application, allowing the attacker to gain access to sensitive data or perform other malicious actions. Code injection can be used to attack any type of web application, including those based on PHP, ASP, Java, and others.
This course will teach you how to identify and exploit common code injection vulnerabilities such as SQL injection.
Training Modules
This course provides you with multiple training modules, each of which is designed to teach you practical skills that can help you solve important cyber problems. Each module offers exercises that will help you build your skills and capabilities.
-
WE-01:
Command Execution
- 6 exercises
-
WE-02:
Code Injection
- 4 exercises
-
WE-03:
Advanced SQL Injection
- 4 exercises
-
WE-04:
Bypass Improper Protections
- 3 exercises
Certificate of Completion
You will receive a Certificate of Completion when you complete this course.
A Certificate of Completion can be very beneficial, especially when job hunting. It proves that you have completed a course and can be a great way to stand out among other candidates. Even if you do not have much experience, it shows that you are willing to learn and have the basic skills required for the job. In addition, some employers may require a Certificate of Completion for certain positions. Therefore, adding it to your portfolio is always an excellent choice.

 Beginner
Beginner