Course Overview
Organizations use SIEMs to help them detect, investigate, and respond to cybersecurity threats. SIEMs can give organizations visibility into what is happening on their networks and help them to identify and respond to potential threats.
This online bootcamp teaches how to use Elasticsearch and Kibana as a SIEM. Elasticsearch is a powerful open-source search engine that can be used to collect, store, and analyze data. Kibana is a visualization tool that makes it easy to work with Elasticsearch data. Together, these tools can be used to build a SIEM system.
Important: The concepts, techniques and tactics you will learn from this bootcamp will work on any modern SIEM.
Infrastructure Deployment
You will learn how to deploy Elasticsearch and Kibana in a test environment.
They are many use cases when a cyber professional needs to deploy their own tools. For example, you may be engaged to protect a network with active threat actors, and no SIEM. Deploying one would give you and your team the visibility required to defend the network.
Other benefits include:
-
Gaining a better understanding of how SIEMs work and how they can be used to support an organization's security goals
-
Being able to customize a SIEM deployment to meet the specific needs of an organization
-
Having the ability to troubleshoot SIEM issues as they arise
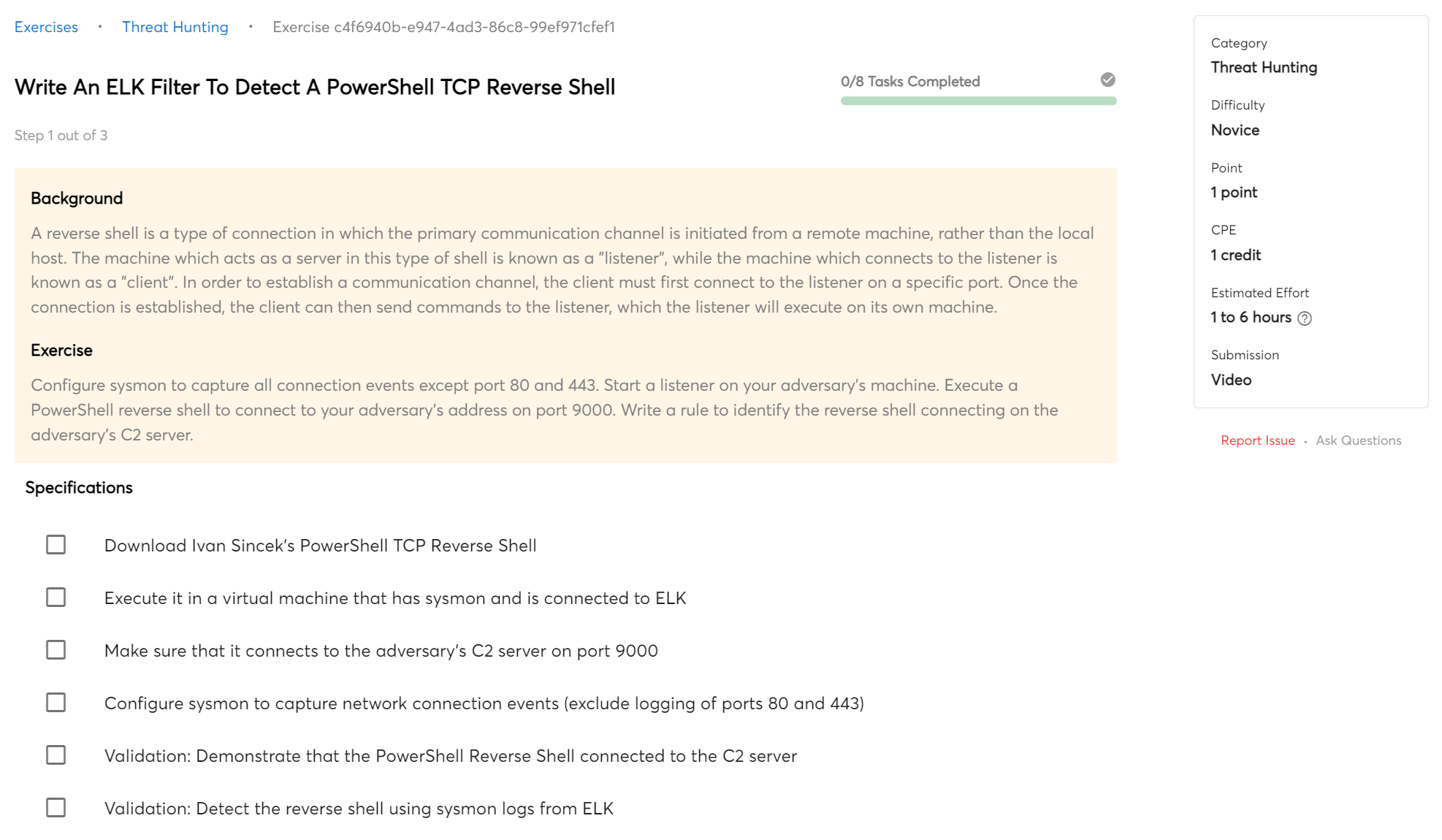
Detect Indicators of Compromise (IOCs)
SIEMs can provide a wealth of data that can be used to search for indicators of compromise (IOCs). IOCs are data points that can be used to determine if a system or network has been compromised. They can include things like IP addresses, file hashes, and registry keys. Knowing how to search for IOCs using a SIEM can help analysts quickly and efficiently identify systems that may have been compromised so that they can take steps to remediate the issue.
This bootcamp will teach you how to search for IOCs and detect compromised machines.
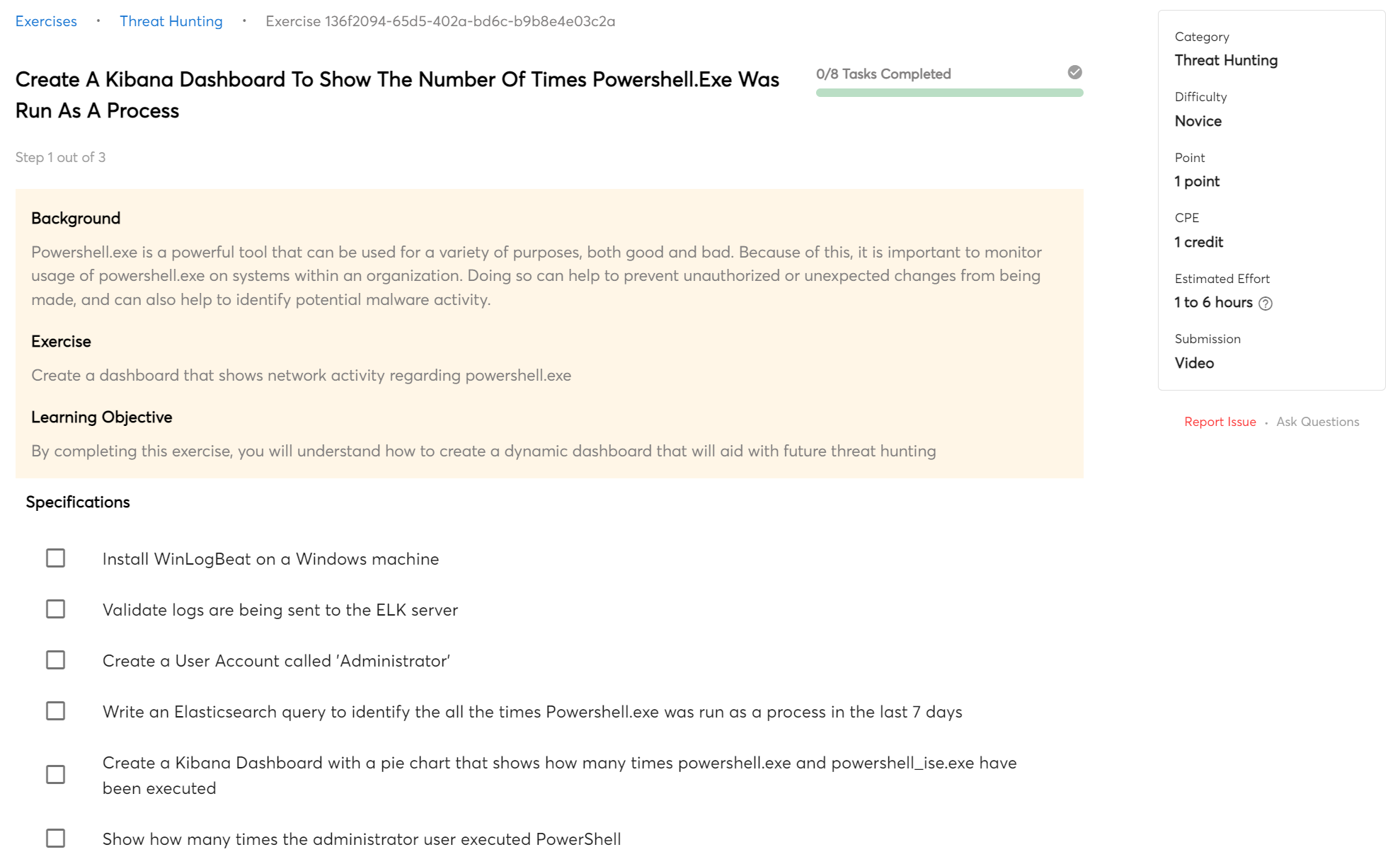
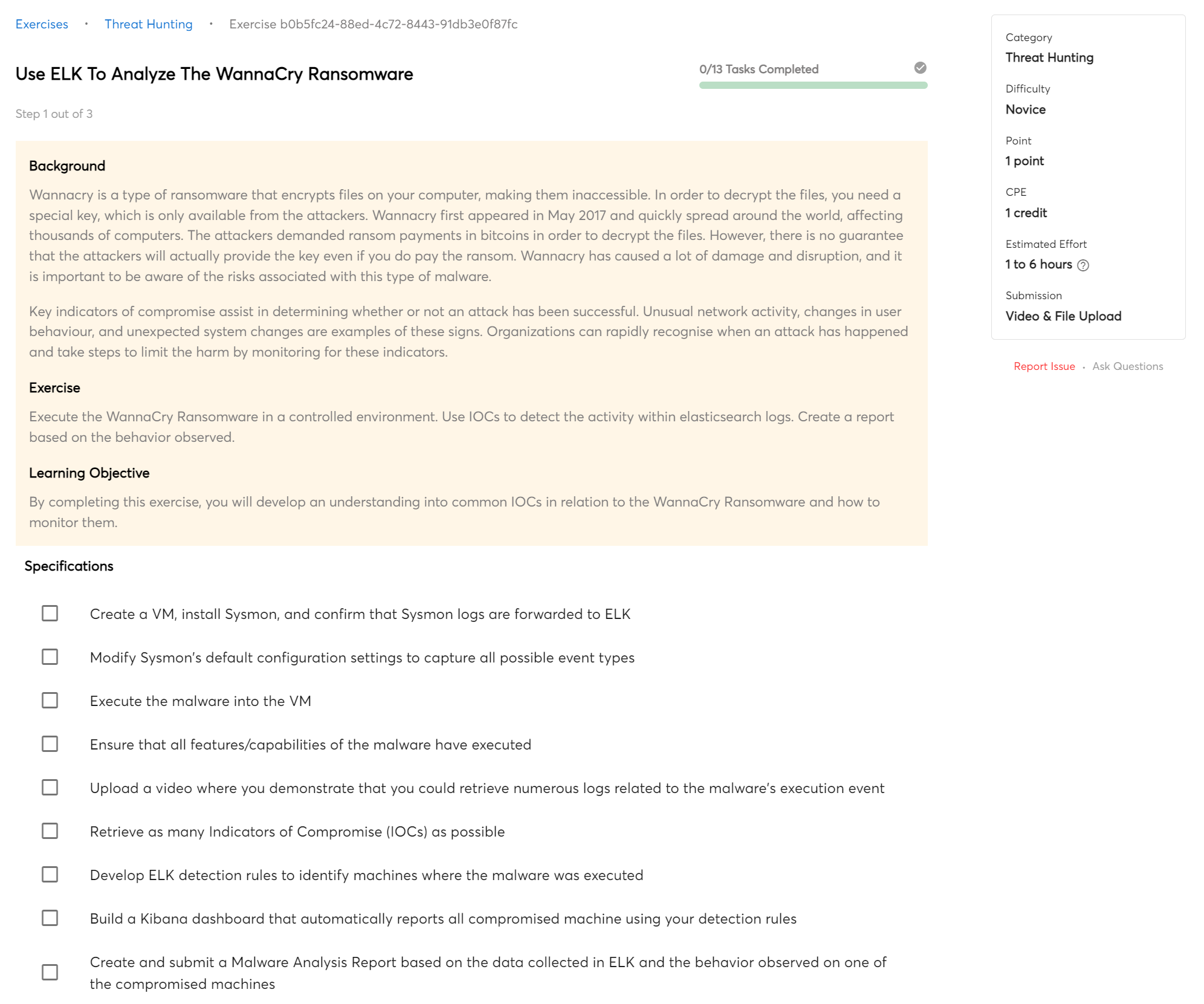
Malware Analysis
A SIEM can be used for dynamic malware analysis, which can be a valuable tool in understanding and mitigating malicious activity on a network. By tracking and analyzing data in real time, a SIEM can help identify malicious behavior and allow for rapid response.
In this course, you will use a SIEM to analyze multiple malware samples.
Training Modules
This course provides you with multiple training modules, each of which is designed to teach you practical skills that can help you solve important cyber problems. Each module offers exercises that will help you build your skills and capabilities.
-
SIEM-01:
SIEM Concepts
- 6 exercises
-
SIEM-02:
Elasticsearch Fundamentals
- 6 exercises
-
SIEM-03:
Basic ELK Security Searches
- 5 exercises
-
SIEM-04:
Intermediate ELK Security Searches
- 5 exercises
-
SIEM-05:
Dashboards
- 3 exercises
-
SIEM-06:
Malware Analysis
- 6 exercises
Certificate of Completion
You will receive a Certificate of Completion when you complete this course.
A Certificate of Completion can be very beneficial, especially when job hunting. It proves that you have completed a course and can be a great way to stand out among other candidates. Even if you do not have much experience, it shows that you are willing to learn and have the basic skills required for the job. In addition, some employers may require a Certificate of Completion for certain positions. Therefore, adding it to your portfolio is always an excellent choice.

 Beginner
Beginner