Course Overview
Advanced persistent threats (APTs) use sophisticated phishing and spear-phishing techniques to gain access to an organization's network.
Phishing is a type of social engineering attack that uses email or other communication channels to trick users into clicking on a malicious link or opening a malicious attachment. Spear-phishing is a targeted form of phishing that is designed to trick a specific individual or group of individuals into taking action that will give the attacker access to their systems.
APTs use these techniques to gain initial access to an organization's network, and then they use a variety of tools and techniques to maintain their presence on the network and move laterally to other systems.
OSINT Research
OSINT (Open Source Intelligence) research is extremely important in spear-phishing and phishing campaigns. By definition, spear-phishing is a targeted email attack that seeks to gathering sensitive information from a specific individual or organization. In order to carry out a successful spear-phishing attack, the attacker must first research their target. This is where OSINT comes in.
OSINT is the process of collecting data from publicly available sources. This can include social media, websites, news articles, etc. By conducting thorough OSINT research, the attacker can learn everything they need to know about their target in order to create a believable and effective phishing email.
By completing this bootcamp, you will learn OSINT techniques to profile any organization or individual in order to create targeted phishing emails.
Resilient C2 Infrastructure
When conducting phishing and spear-phishing campaigns, it is important to use a resilient C2 infrastructure. This will ensure that your campaign can withstand any attempts to shut it down. By using a C2 infrastructure that is designed to be resilient, you can be sure that your campaign will be able to continue running and emails are not blocked by spam filters.
This bootcamp teaches you how to deploy and configure a resilient C2 infrastructure.
Attack Payloads
A spear-phishing payload is a malicious email that appears to come from a trusted source. The email contains a link or attachment that, when clicked, will install malware on the victim's computer. Spear-phishing payloads are important because they can be used to steal sensitive information or to gain access to sensitive systems.
Examples of payloads you will learn to use:
-
Legacy HTA files
-
Microsoft Office Macros
-
Shortcut files
Bypassing Security Protections
In this bootcamp, you will learn how to bypass spam filters and anti-virus software.
When delivering a spear-phishing campaign, it is important to bypass security protections in order to increase the chances of success. By bypassing security protections, attackers can more easily gain access to sensitive information and systems. Additionally, bypassing security protections can help attackers avoid detection and increase their chances of remaining undetected.
Training Modules
This course provides you with multiple training modules, each of which is designed to teach you practical skills that can help you solve important cyber problems. Each module offers exercises that will help you build your skills and capabilities.
-
PSP-01:
Researching Your Target
- 16 exercises
-
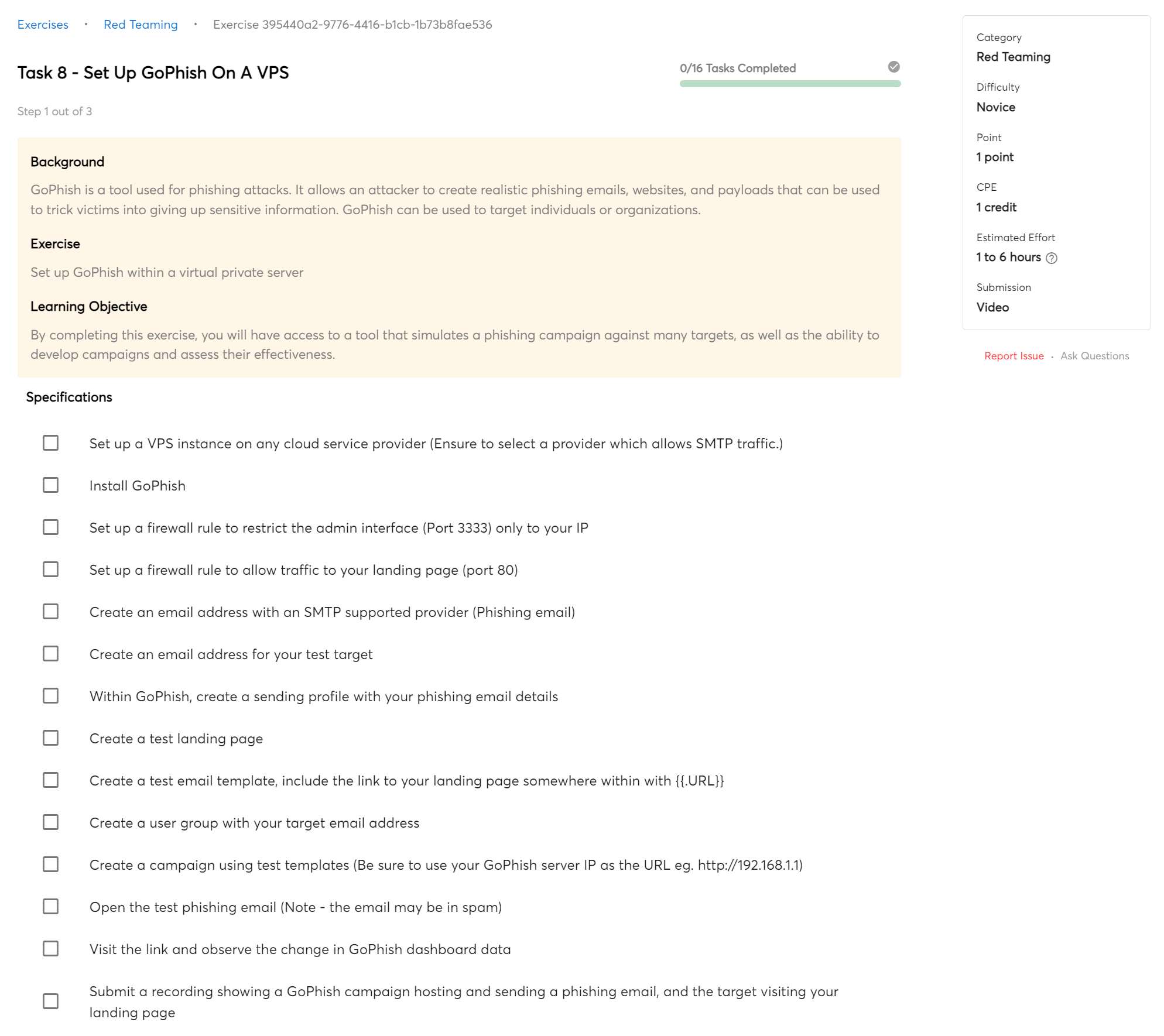
PSP-02:
Setting up the infrastructure
- 12 exercises
-
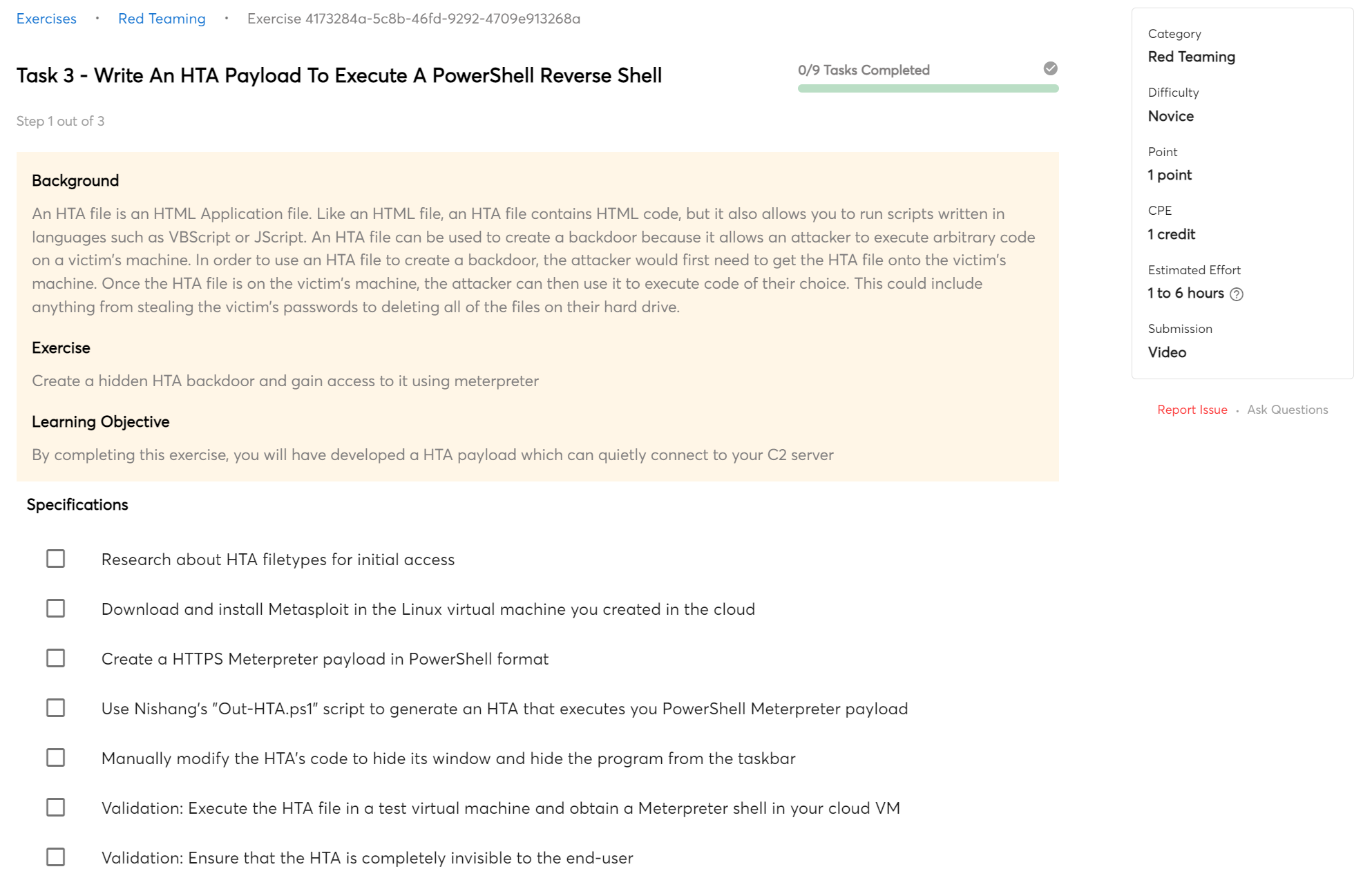
PSP-03:
Payload Generation
- 9 exercises
-
PSP-04:
Payload Delivery
- 6 exercises
-
PSP-05:
Setting-Up the Campaign
- 8 exercises
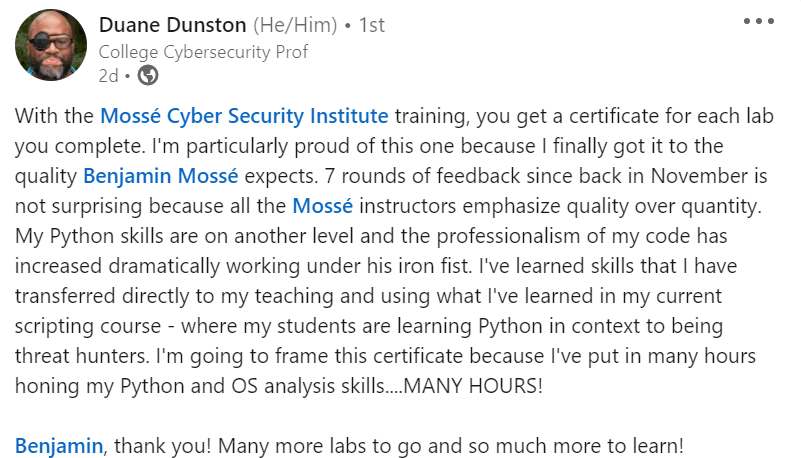
Certificate of Completion
You will receive a Certificate of Completion when you complete this course.
A Certificate of Completion can be very beneficial, especially when job hunting. It proves that you have completed a course and can be a great way to stand out among other candidates. Even if you do not have much experience, it shows that you are willing to learn and have the basic skills required for the job. In addition, some employers may require a Certificate of Completion for certain positions. Therefore, adding it to your portfolio is always an excellent choice.

 Beginner
Beginner