Course Overview
Learn the Foundations of Information Security Management with Our Specialized Bootcamp!
Immerse yourself in the dynamic realm of information security management, where you'll gain insight into the foundational aspects of identifying, assessing, and mitigating information security risks through research-based exercises.
In this bootcamp, you'll delve into the fundamentals of information security management, learning various techniques for risk identification, assessment, and mitigation. Through research-based exercises, you'll understand the development of policies, procedures, and controls and their role in safeguarding information assets.
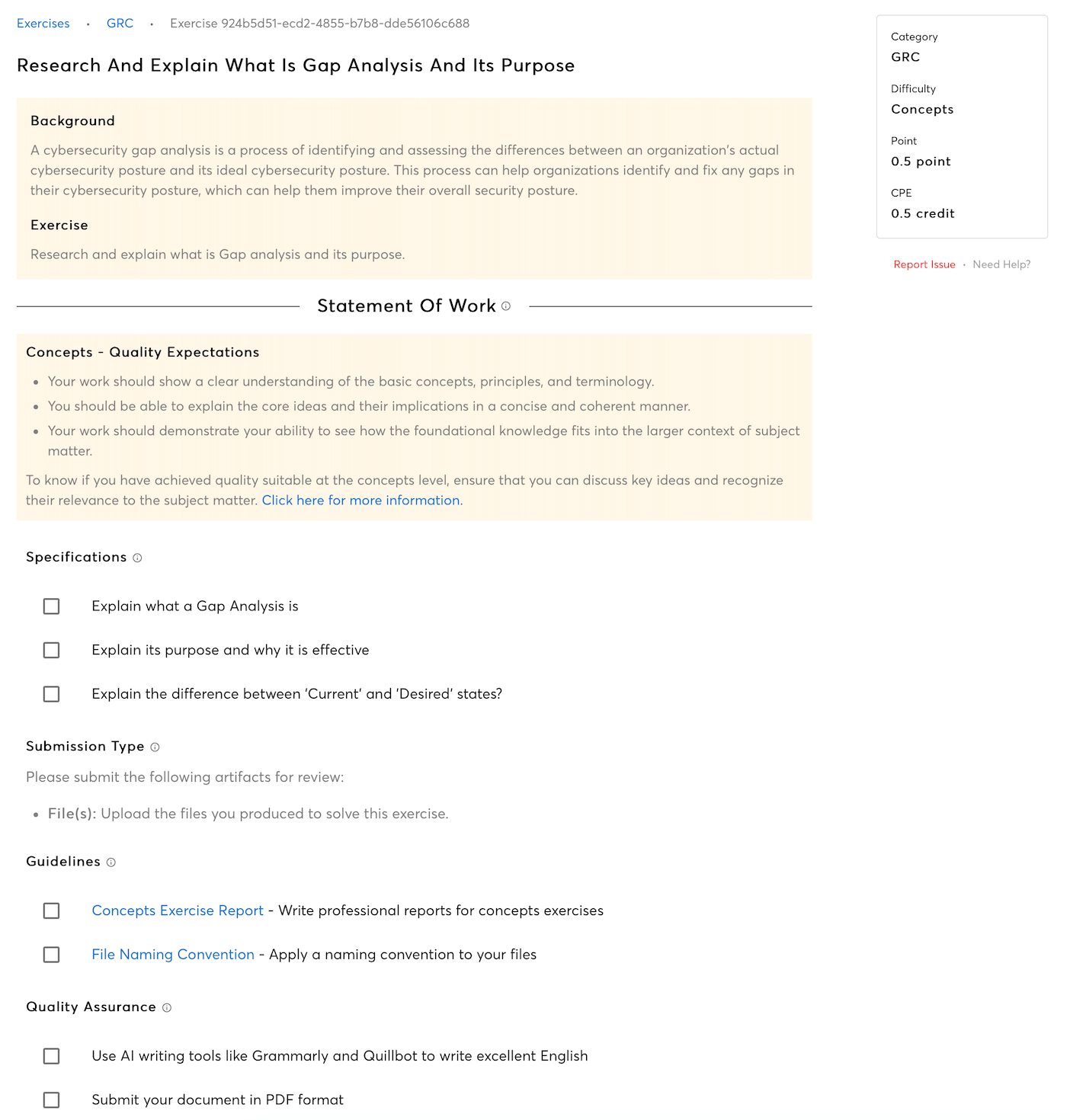
Risk Identification
Understand the theoretical significance of identifying and assessing information security risks across organizational operations.
Policies, Procedures, and Controls
Learn why the development and implementation of policies, procedures, and controls are important, and how they play a role in protecting information assets.
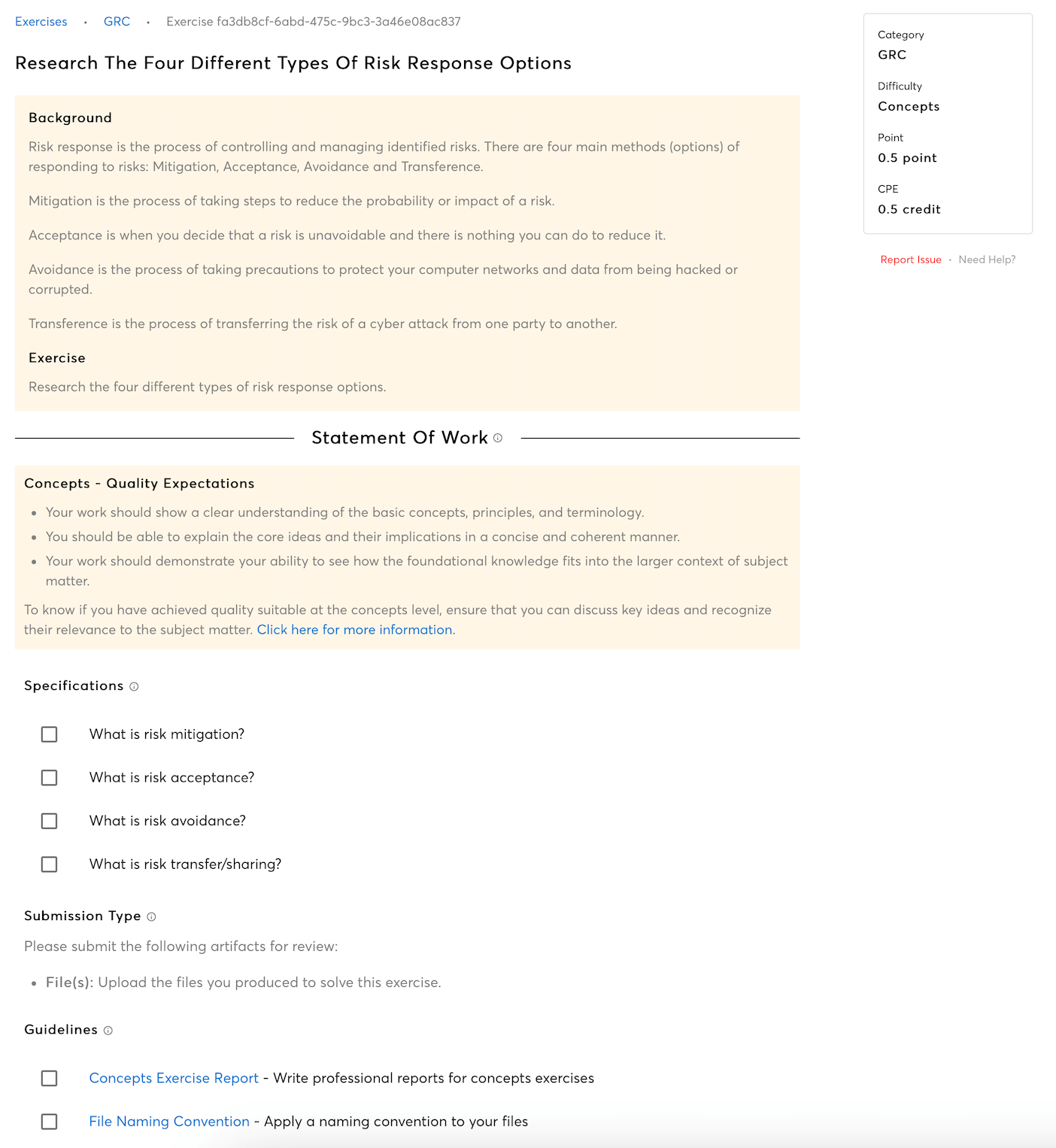
Comprehensive Risk Assessment Methodologies
Learn why formulating comprehensive risk assessment methodologies are significant, and learn how these frameworks enable accurate evaluation and prioritization of information security risks for effective mitigation strategies.
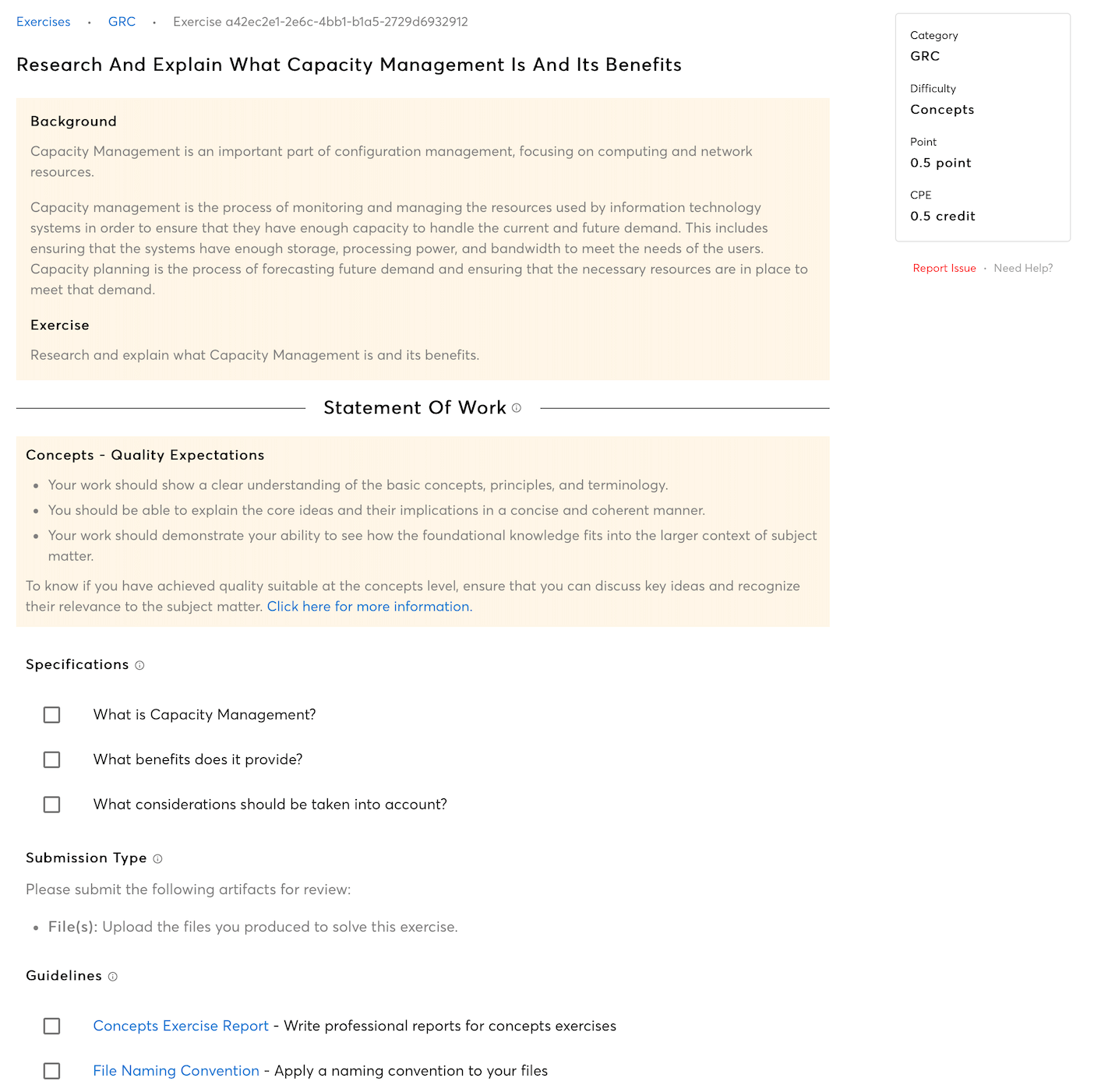
Monitoring and Evaluating Information Security Measures
Learn about the theoretical aspects of monitoring and evaluating information security measures, and understand how these frameworks ensure ongoing compliance with organizational policies and regulatory requirements while adapting to evolving security threats.
By the end of this comprehensive bootcamp, you'll emerge with a solid theoretical understanding of the foundational principles and practices of information security management. Whether you're aiming to advance your career in this field or enhance your cybersecurity skill set, this research-intensive bootcamp will provide you with the theoretical knowledge needed to excel and make a significant impact on organizational security.
Training Modules
This course provides you with multiple training modules, each of which is designed to teach you practical skills that can help you solve important cyber problems. Each module offers exercises that will help you build your skills and capabilities.
-
ISM-01:
Governance
- 29 exercises
-
ISM-02:
Risk Management
- 29 exercises
-
ISM-03:
Program Development and Management
- 29 exercises
-
ISM-04:
Incident Management
- 19 exercises
Certificate of Completion
You will receive a Certificate of Completion when you complete this course.
A Certificate of Completion can be very beneficial, especially when job hunting. It proves that you have completed a course and can be a great way to stand out among other candidates. Even if you do not have much experience, it shows that you are willing to learn and have the basic skills required for the job. In addition, some employers may require a Certificate of Completion for certain positions. Therefore, adding it to your portfolio is always an excellent choice.

 beginner
beginner