Course Overview
Embark on a journey into the dark corners of Active Directory (AD) exploitation with this intensive bootcamp, tailored for those looking to master the art of breaching AD environments. This course strips away the defensive layers, focusing purely on exploitation tactics that can be used against Active Directory systems.
Dive into the architectural nuances of AD, understanding how its components and services interconnect, forming the backbone of enterprise networks. This foundational knowledge sets the stage for exploring vulnerabilities inherent in the AD design.
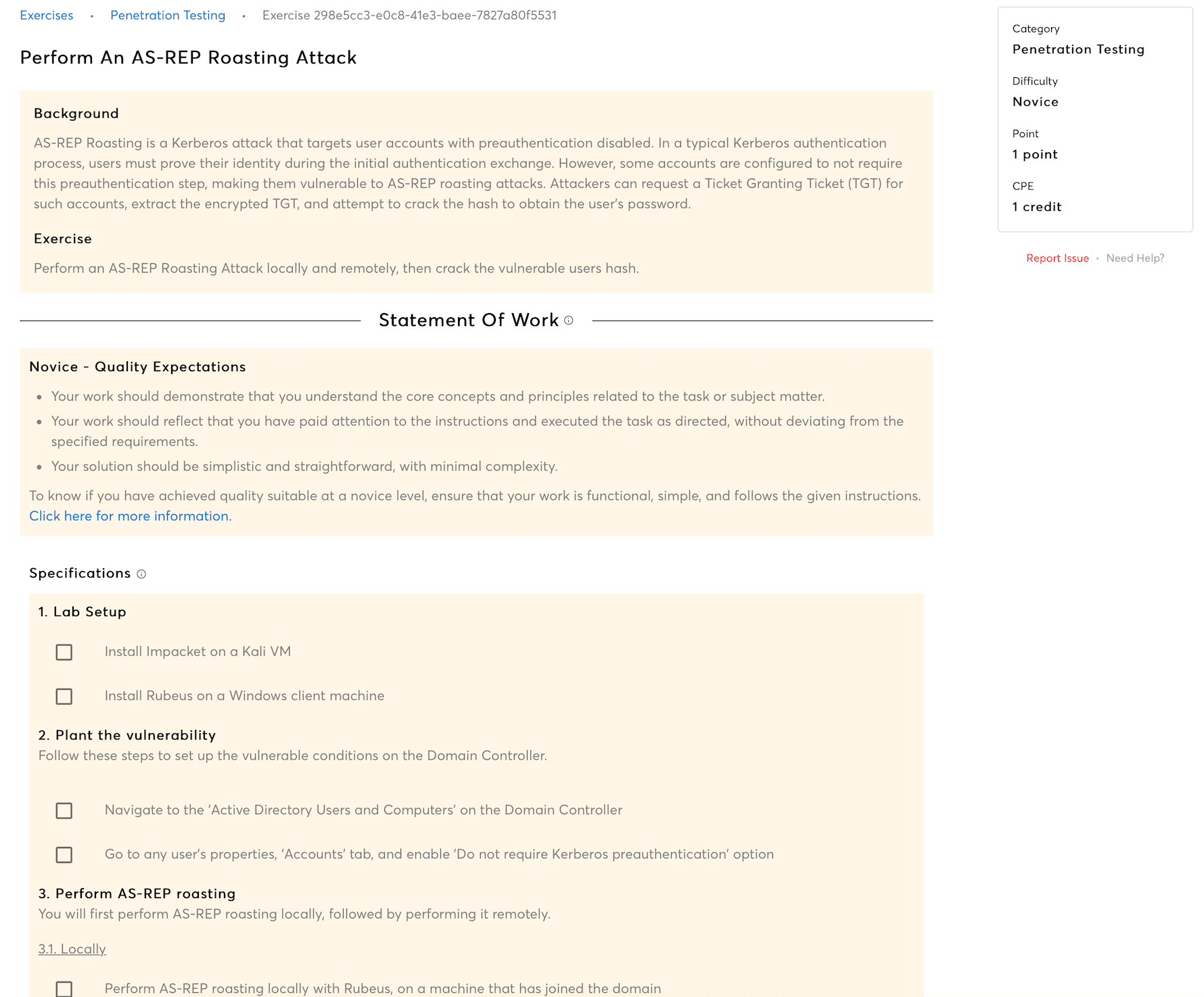
You will learn about reconnaissance techniques used to gather intelligence on AD environments, such as enumerating domain controllers, user accounts, and AD schema details. Understanding these elements is crucial for planning targeted attacks.
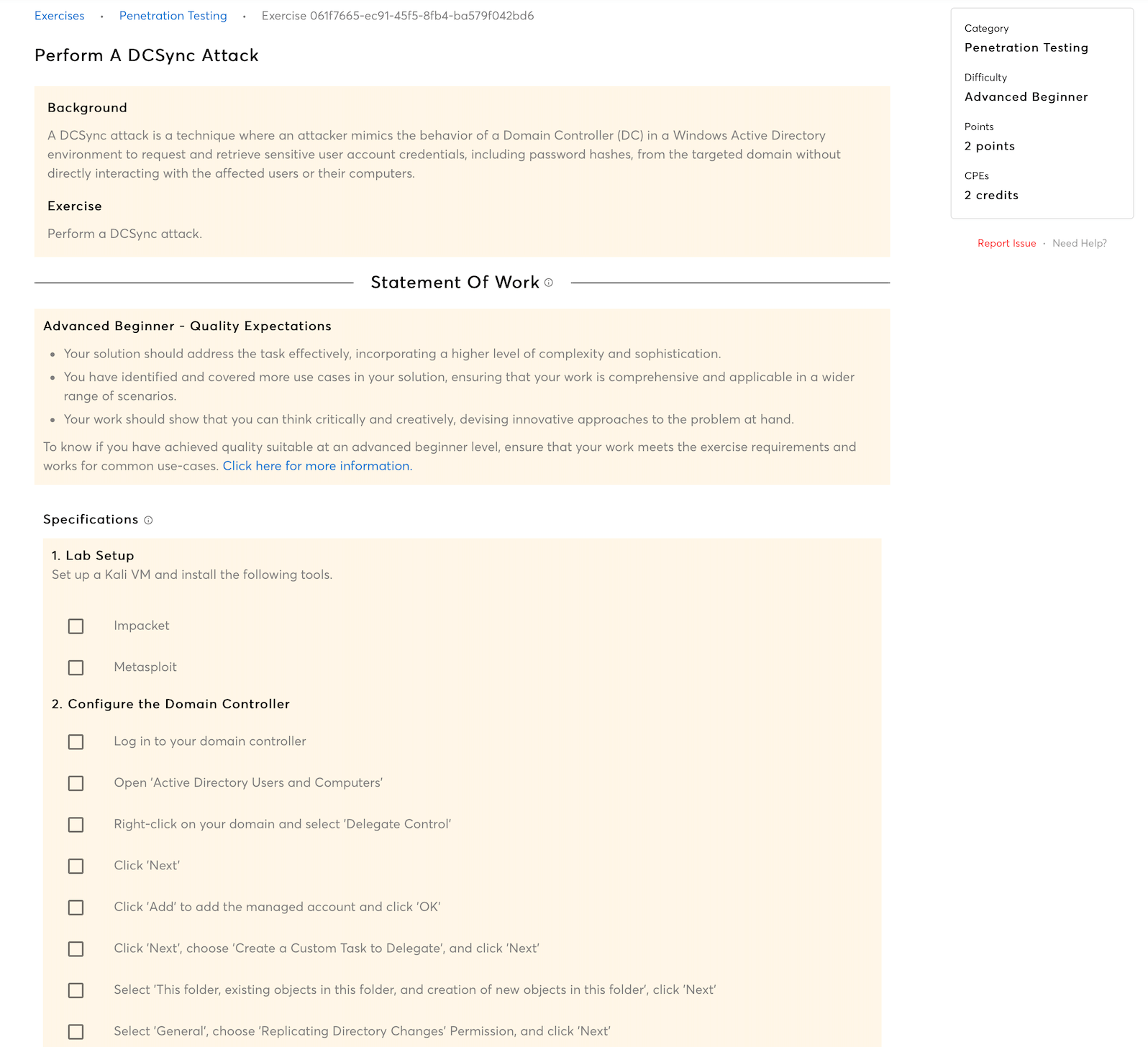
The course then advances to sophisticated exploitation methods, including DCSync attacks, where you mimic a domain controller to extract credential secrets from AD, bypassing standard authentication processes. You'll explore how to leverage pass-the-hash attacks to authenticate to network resources using hashed credentials, circumventing the need for plain text passwords.
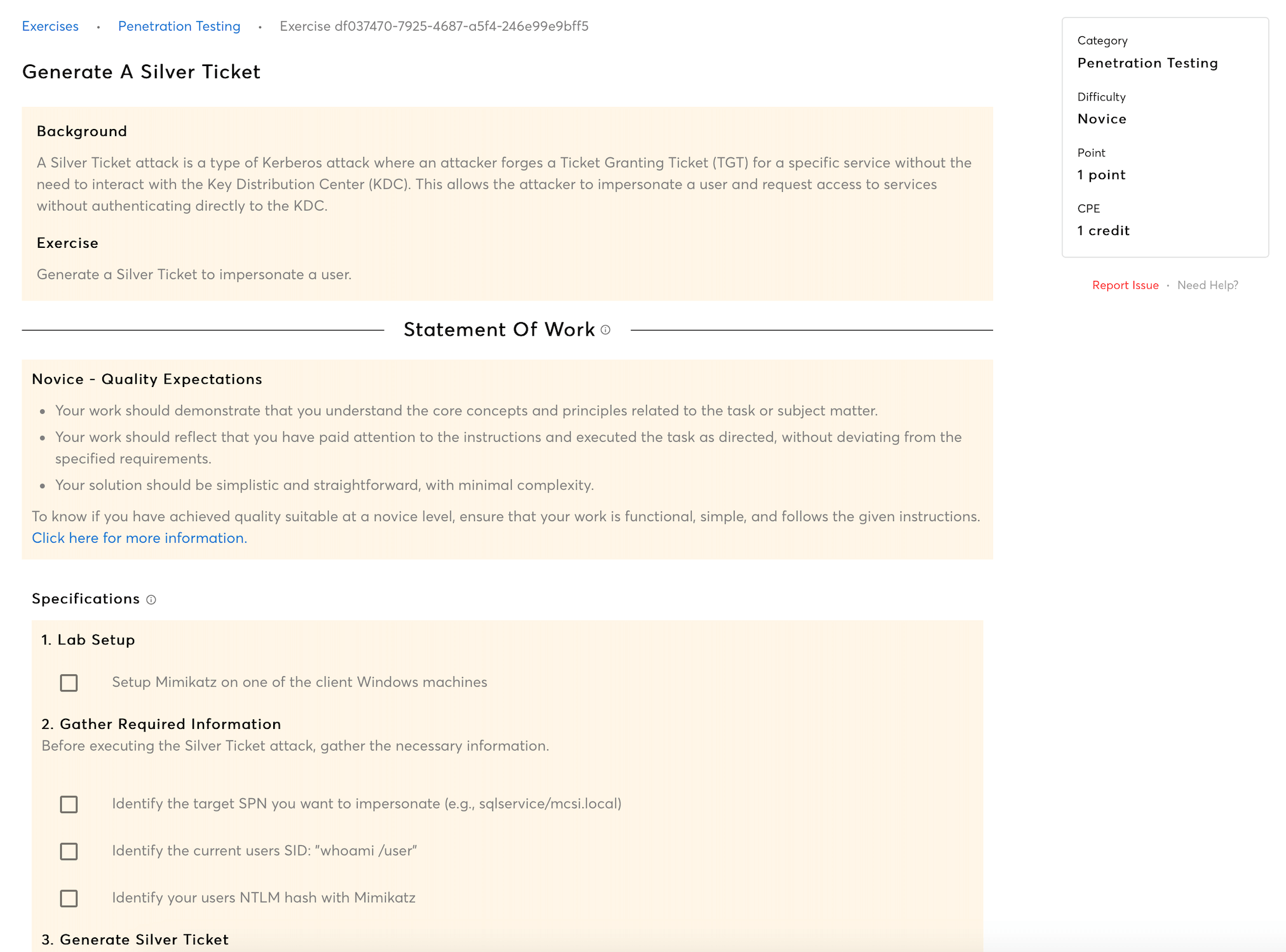
Delve into Kerberoasting, exploiting the Kerberos ticket-granting service. The intricate details of Golden Ticket and Silver Ticket attacks will be unpacked, showcasing how to create authentication tickets granting unlimited access to AD resources.
DCShadow attacks will be a key focus, teaching you how to manipulate AD data and objects stealthily, enabling persistent access and control over AD environments without triggering alerts.
Throughout the bootcamp, you'll engage in hands-on exercises, applying these exploitation tactics in a controlled setting. You'll use tools like Mimikatz and BloodHound to perform real-world attack simulations, honing your skills in AD exploitation.
By the end of this bootcamp, you'll have a deep understanding of Active Directory's vulnerabilities and be skilled in exploiting them, equipping you with the knowledge to test and enhance AD security through offensive tactics. This course offers a unique perspective into the attacker's mindset, providing you with the tools and techniques to exploit Active Directory systems effectively.
Training Modules
This course provides you with multiple training modules, each of which is designed to teach you practical skills that can help you solve important cyber problems. Each module offers exercises that will help you build your skills and capabilities.
-
AD-01:
Fundamentals
- 3 exercises
-
AD-02:
Network Footprinting
- 3 exercises
-
AD-03:
File Based Attacks
- 4 exercises
-
AD-04:
Privilege Escalation
- 5 exercises
-
AD-05:
Lateral Movement
- 5 exercises
-
AD-06:
Post-Compromise and Persistence
- 2 exercises
-
AD-07:
Documentation
- 1 exercises
Certificate of Completion
You will receive a Certificate of Completion when you complete this course.
A Certificate of Completion can be very beneficial, especially when job hunting. It proves that you have completed a course and can be a great way to stand out among other candidates. Even if you do not have much experience, it shows that you are willing to learn and have the basic skills required for the job. In addition, some employers may require a Certificate of Completion for certain positions. Therefore, adding it to your portfolio is always an excellent choice.

 Intermediate
Intermediate